The cost of a data breach
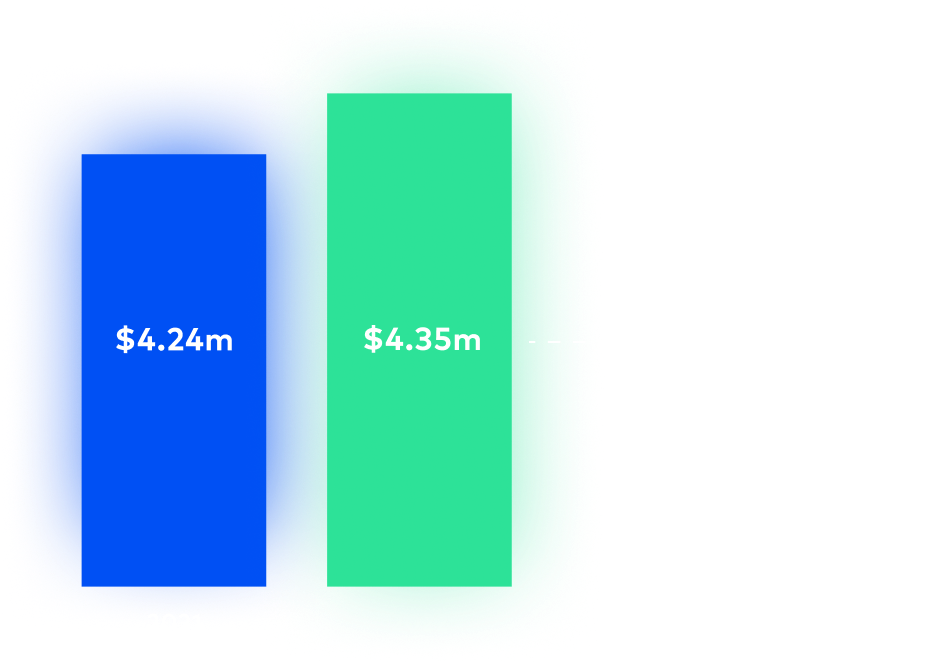
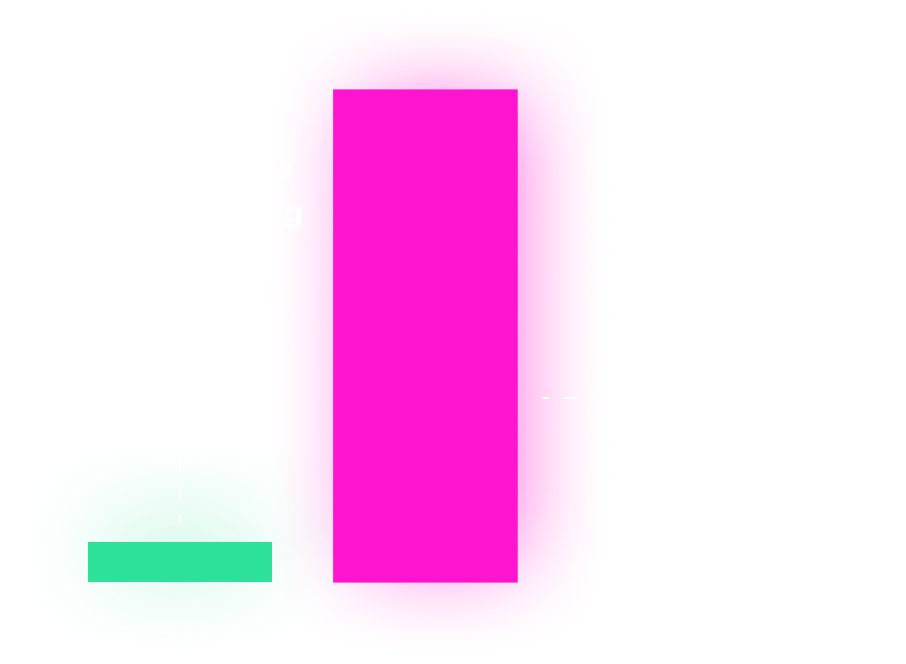
Organizations aren’t only facing more threats than before, but the cost of a potential breach is higher than it was last year. Incidents racked up a record $4.35 million in cost, while organizations not employing zero trust strategies incurred an even greater loss at $5.14 million.
Moreover, the rapid rise of cloud adoption means that organizations are storing critical data in an environment for which the security frameworks are often still in their infancy. For those with less mature cloud security programs, the cost of a breach was $660,000 more on average.