-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
A SQL injection vulnerability in FlyCASS exposed serious airport security risks, allowing unauthorized access to secure areas and cockpits. Here's what you need to know.

For frequent travelers, airport security lines are a familiar scene. However, for airline employees—such as pilots and flight attendants—bypassing these lengthy lines is made possible through the TSA’s Known Crewmember (KCM) program. KCM allows a wide range of Airlines’ crew members to access secure areas of the airport without going through traditional security screening, even when flying domestically for personal reasons.
The process is straightforward: the crew presents their KCM barcode, employee number, and airline information to a TSA agent, who verifies their employment status using a dedicated system. If authenticated, they are granted access to the sterile area without further screening.
Another system, the Cockpit Access Security System (CASS), allows pilots who need to commute or travel to access jumpseats in the cockpit if no passenger seats are available. Gate agents verify the pilots’ authorization through CASS before granting them access to the cockpit.
The crucial element here is employment status verification. If an individual is no longer employed by an airline, they lose the ability to use KCM or CASS. This employment verification system, while vital for security, became the focus of Ian Carroll and Sam Curry’s investigation into the vulnerability, which led them to ARINC and, eventually, Flyclass.
ARINC, a subsidiary of Collins Aerospace, is contracted by the TSA to operate the Known Crewmember system. ARINC functions as the intermediary for KCM and CASS processes, handling requests from the TSA and routing them to the appropriate airline’s authorization system.
The TSA and airlines can send requests such as ‘CockpitAccessRequest’ and ‘CrewVerificationRequest’ to ARINC which serves as an agent for routing it to the appropriate airline’s system, then later receiving the response.
Each and every single airline that participate in KCM and CASS operates its own system to verify employment status and authorize access. For larger airlines, custom-built systems are likely in place to handle these requests, but for smaller airlines, managing KCM and CASS authorization involves third-party vendors.
This is where FlyCASS comes into play, a vendor that offers a web-based interface for smaller airlines to participate in CASS and KCM authorization.
On April 23, 2024, while investigating the systems that support KCM and CASS, researchers Ian Carroll and Sam Curry stumbled upon FlyCASS – a platform designed to assist smaller airlines in handling their authorization requests.
As part of their research, they accessed FlyCASS’s login page, which appeared to offer individual logins for each airline, including Air Transport International (ATI). Upon finding nothing but a login page, they decided to test for common vulnerabilities.
As is standard practice in web application security testing, they input a simple SQL injection attempt by entering a single quote in the username field. Almost immediately, they received a MySQL error message, indicating the presence of an SQL injection vulnerability.
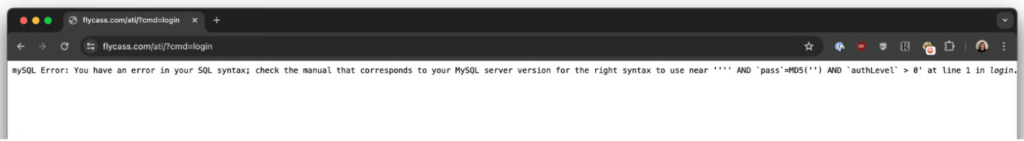
This result signified a major red flag. The system was directly interpolating user input into its SQL queries without proper sanitization, leaving the system wide open to attacks. Ian and Sam used a well-known SQL injection tool, sqlmap, to confirm their findings. By entering a basic SQL payload, such as ‘ or ‘1’=’1 and ‘) OR MD5(‘1‘)=MD5(‘1), they managed to log into FlyCASS as an administrator for Air Transport International.
Once inside the system as administrators for Air Transport International, the researchers discovered that they had gained the ability to manage the airline’s entire list of pilots and flight attendants. This included adding new employees, modifying existing ones, and approving personnel for KCM and CASS access.
Disturbingly, they’re research showed the absence of any additional verification checks beyond logging into the system to confirm the legitimacy of any changes made to the employee list.
To test the implications of this flaw, Caroll and Curry then created a new employee “Test TestOnly”, added this fictional employee to the Air Transport International crew list including attaching a photo to its profile.
After doing so, they used FlyCASS’s query features to verify that their test user had successfully been authorized for both KCM and CASS access, and found the system approved the newly created user without any further checks.
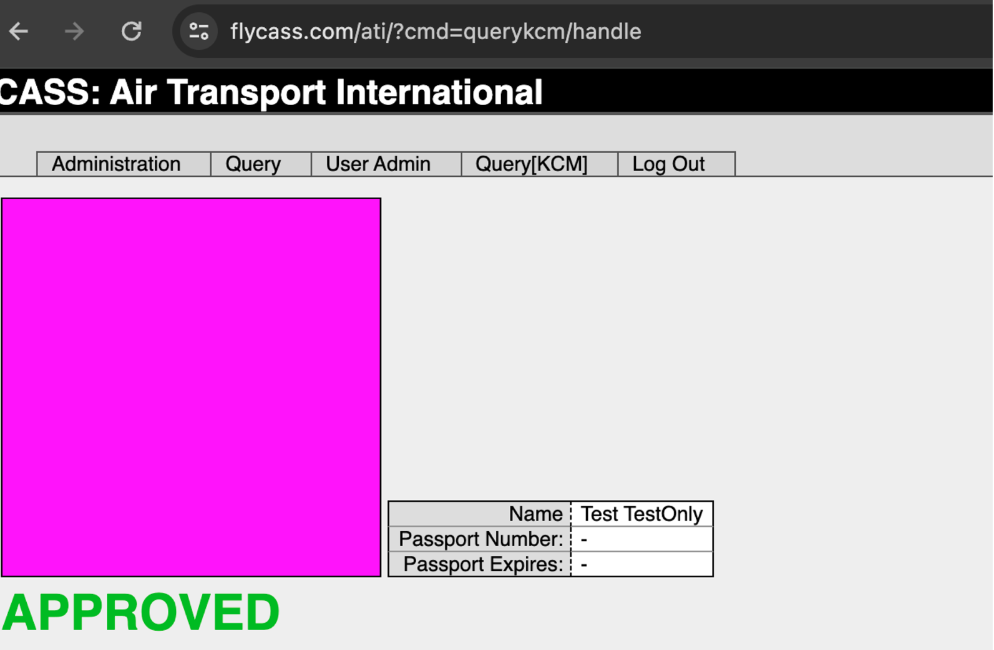
This meant that anyone with basic knowledge of SQL injection had the ability not only to bypass airport security screening by adding themselves to the KCM system, but also gain access to the cockpits of commercial airliners by authorizing themselves through CASS. The potential for abuse was staggering, with dire implications for airport and aviation security.
Recognizing the severity of the issue, Ian Carroll and Sam Curry began the responsible disclosure process immediately after confirming the vulnerability. On April 23, 2024, they reached out to the Department of Homeland Security (DHS) to inform them of the flaw, given the critical role DHS plays in overseeing national security.
In their report, the researchers noted initial challenges in identifying the appropriate point of contact for disclosure. They were hesitant to reach out to FlyCASS directly, as “it appeared to be operated only by one person and we did not want to alarm them “, they say.
On April 23rd, they successfully disclosed the vulnerability to the Department of Homeland Security (DHS), which acknowledged the issue and assured them that it was being taken “very seriously.” Shortly thereafter, FlyCASS was disabled within the KCM and CASS systems, and the vulnerabilities were subsequently addressed.
Once the flaw was resolved, the researchers attempted to coordinate a safe disclosure process but unfortunately, instead of collaborating, the DHS stopped communicating, and the Transportation Security Administration (TSA) issued a series of dangerously inaccurate statements regarding the vulnerability.
The TSA’s press office denied the researchers’ findings, claiming the flaw could not be exploited to access a KCM checkpoint, as new members undergo a vetting process before receiving a KCM barcode. However, the researchers pointed out that a KCM barcode isn’t required for checkpoint access, since Transportation Security Officers (TSOs) can manually enter an airline employee ID.
The agency’s response to Ian Carroll and Sam Curry bringing this to the TSA’s attention, was removing references to manual ID entry from their website, yet they failed to address the issue publicly. The researchers confirmed that the TSO interface still allowed manual input of employee IDs, contradicting TSA’s public statement.
Additionally, the vulnerability gave way to other potential attack vectors. An attacker could modify an existing KCM member’s profile by changing their name and photo, thereby bypassing any vetting processes that apply to new members. If someone managed to obtain an unenrolled KCM barcode, they could also enroll it themselves through the KCM website, linking it to an employee ID without any oversight.
By May 7, 2024, the DHS CISO confirmed that FlyCASS had been disconnected from both KCM and CASS to prevent any further unauthorized access while the vulnerability was remediated.
However, the response from the Transportation Security Administration (TSA), the agency responsible for airport security, was less cooperative. On May 17, 2024, the TSA issued a press statement claiming that the vulnerability could not be used to bypass airport security, as new members must undergo a vetting process before being issued a KCM barcode.
This statement was found to be incorrect: TSA agents can manually enter employee IDs into the system, bypassing the need for a KCM barcode altogether. Despite several follow-ups, including attempts on June 4, 2024, to correct TSA’s public statements, no further response was received from the DHS or TSA.
This use case serves as a sobering reminder of the critical importance of vulnerability management and the dangers of complacency in cybersecurity. A single SQL injection flaw in FlyCASS had the potential to compromise not just a few airlines but the security of an entire system designed to protect air travel.
Had this vulnerability been exploited by malicious actors, they could have easily bypassed airport security screening and gained unauthorized access to aircraft cockpits, posing an immense threat to both passengers and crew.
This highlights why organizations must adopt a proactive approach to vulnerability management, continuously auditing and testing their systems for vulnerabilities and, most importantly, promptly addressing those discovered.
Proactive vulnerability management is essential to maintaining security in today’s increasingly complex digital world. The story of the FlyCASS vulnerability is a perfect example of how a seemingly small flaw can have catastrophic implications when left unchecked.
As a vulnerability management company, we strive to ensure that critical vulnerabilities are identified and remediated before they can be exploited, safeguarding both enterprises and individuals from harm.
Each new vulnerability is a reminder of where we stand and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors: