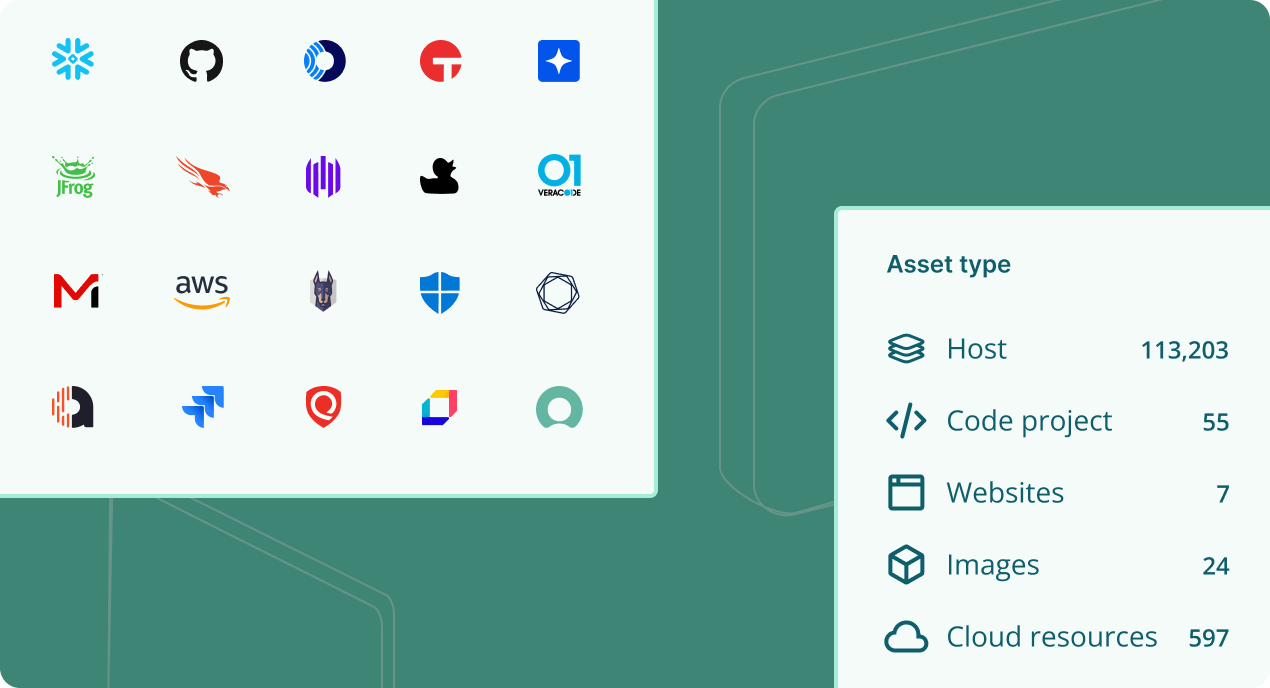
See your risk in one place
Consolidate vulnerability scan data across your critical attack surfaces, including traditional and cloud-based infrastructure and application environments. Connect to 100+ tools to ingest security findings into the exposure data lake.
Learn more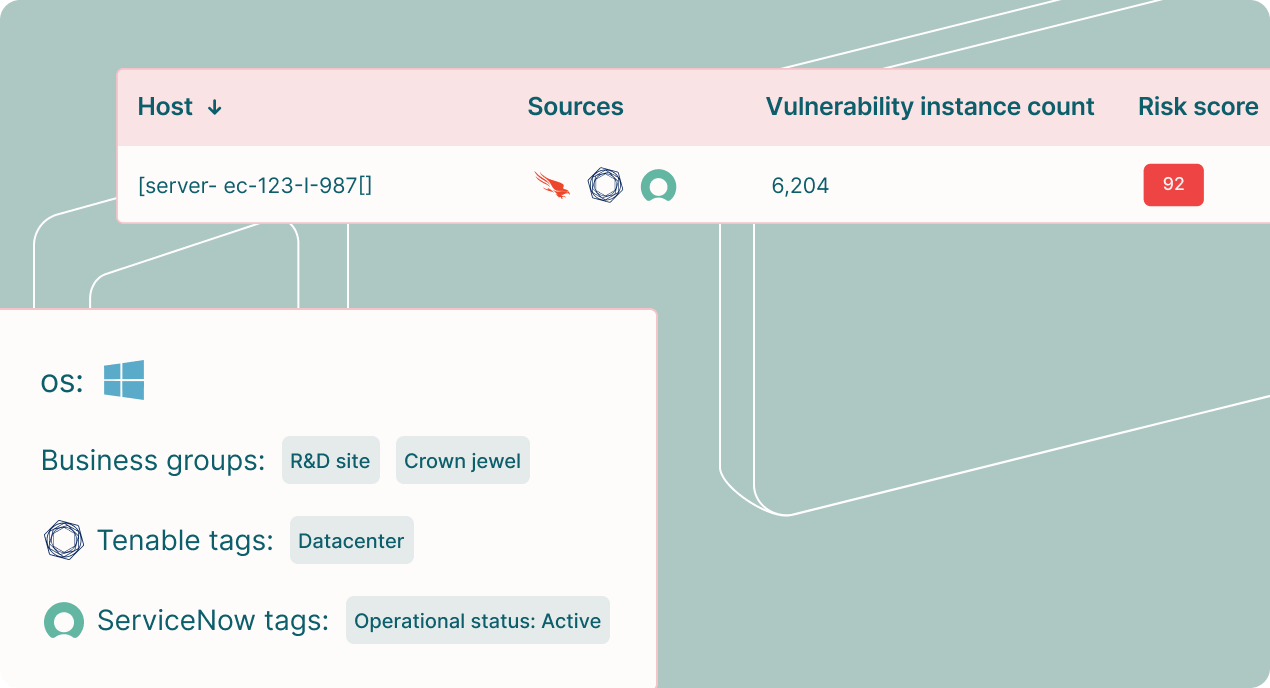
Normalize vulnerability and asset data at scale
Get the most out of your scan and asset data. Deduplicate and correlate cyber signals to generate a consistent data model and a unified exposure risk language.
Learn more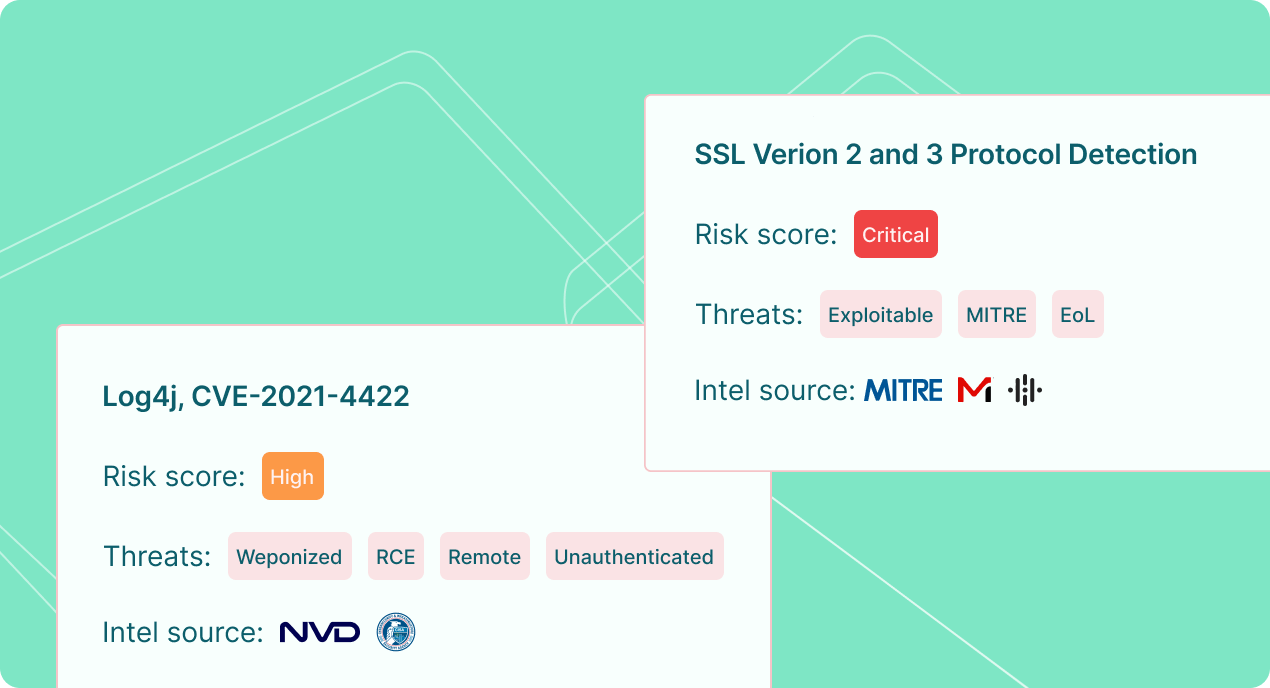
Add context to gain a deeper understanding of risk
Enrich with 20+ threat intelligence including vulnerability criticality, exploitability metrics, attack vectors, End-of-Life info, organization risk tolerance, and asset details.
Learn more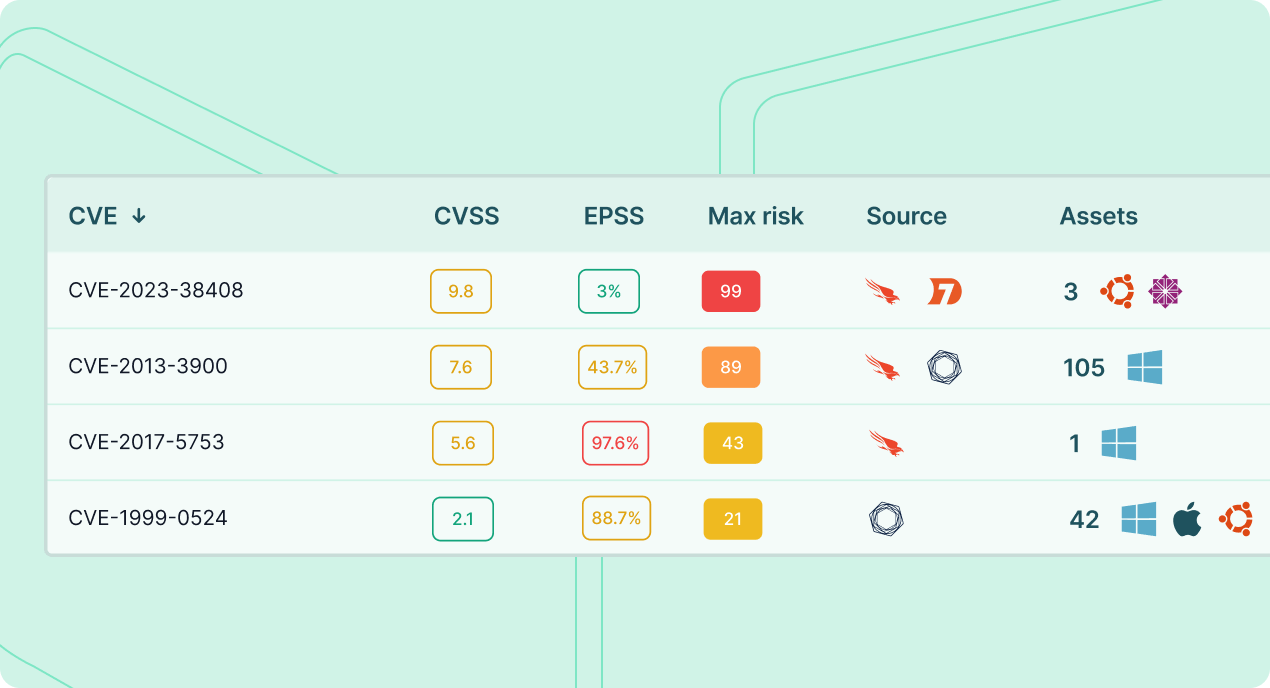
Prioritize risk that matters most
Go beyond technical severity scoring to prioritize vulnerabilities based on actual, meaningful cyber risk to the specific organization.
Learn more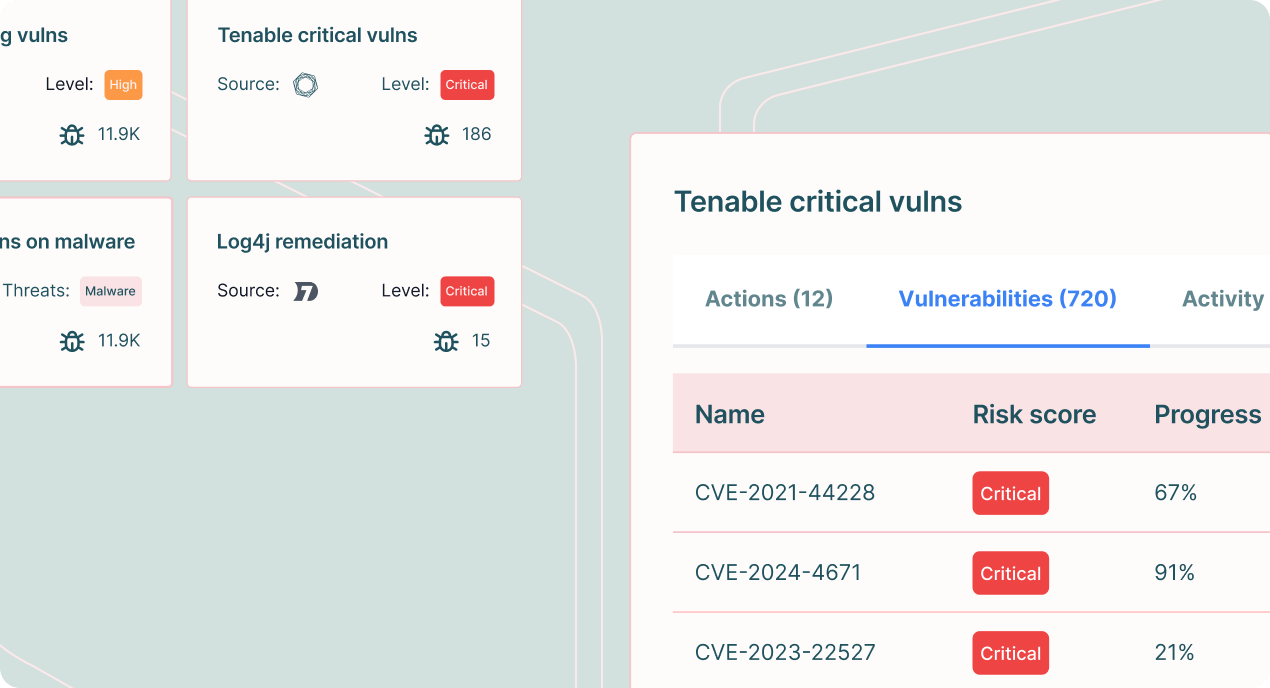
Save time and mitigate risk efficiently
Uncover vulnerability root causes, and automate remediation actions through workflows designed to address risk at scale.
Learn more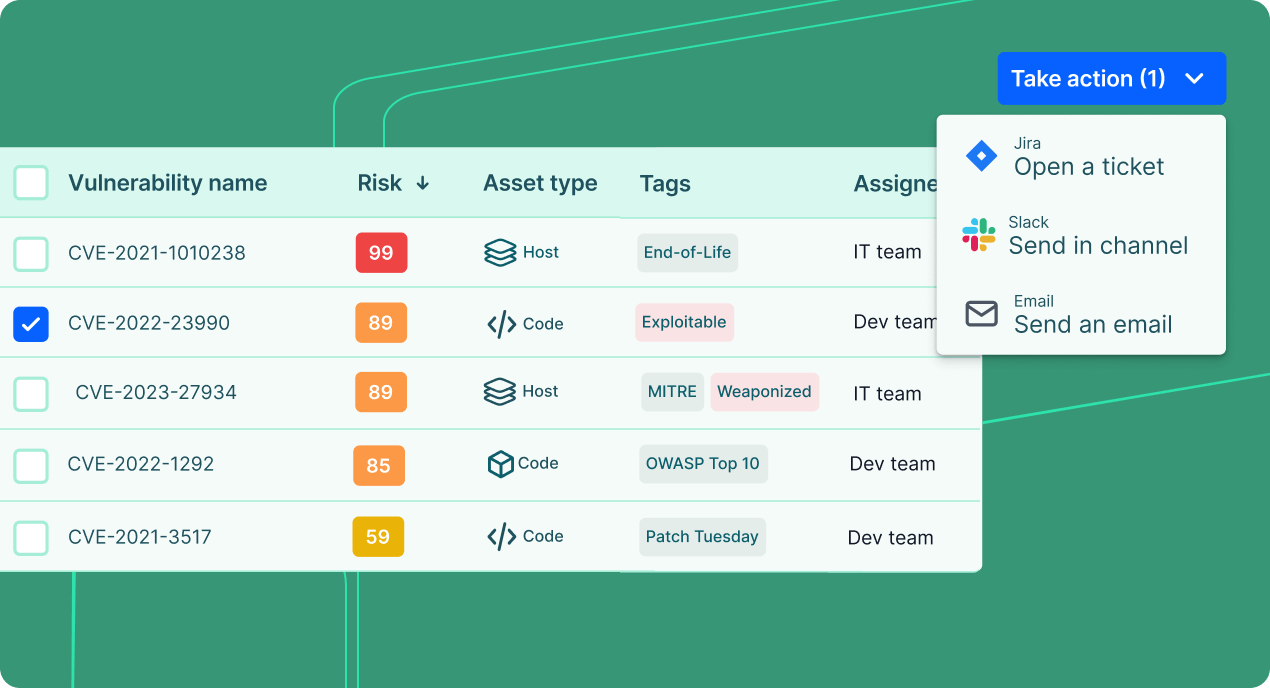
Facilitate frictionless cross-functional collaboration
Identify stakeholders in the remediation process and collaborate with teams like IT, engineering and DevOps. Integrate with native ticketing tools (e.g., Jira, ServiceNow) and communication tools.
Learn more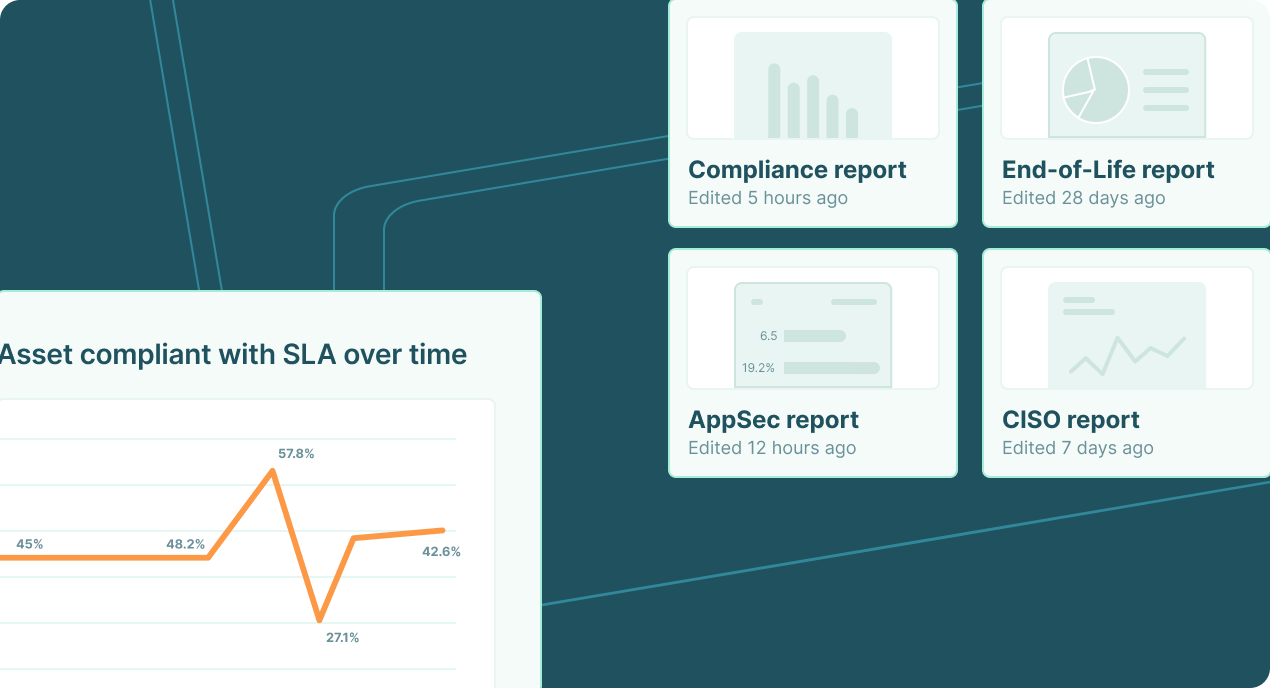
Communicate risk across the organization
Make data-driven mitigation decisions and ensure compliance with regulations. Provided reports are highly customizable to meet the specific needs of your organization and security leaders.
Learn more