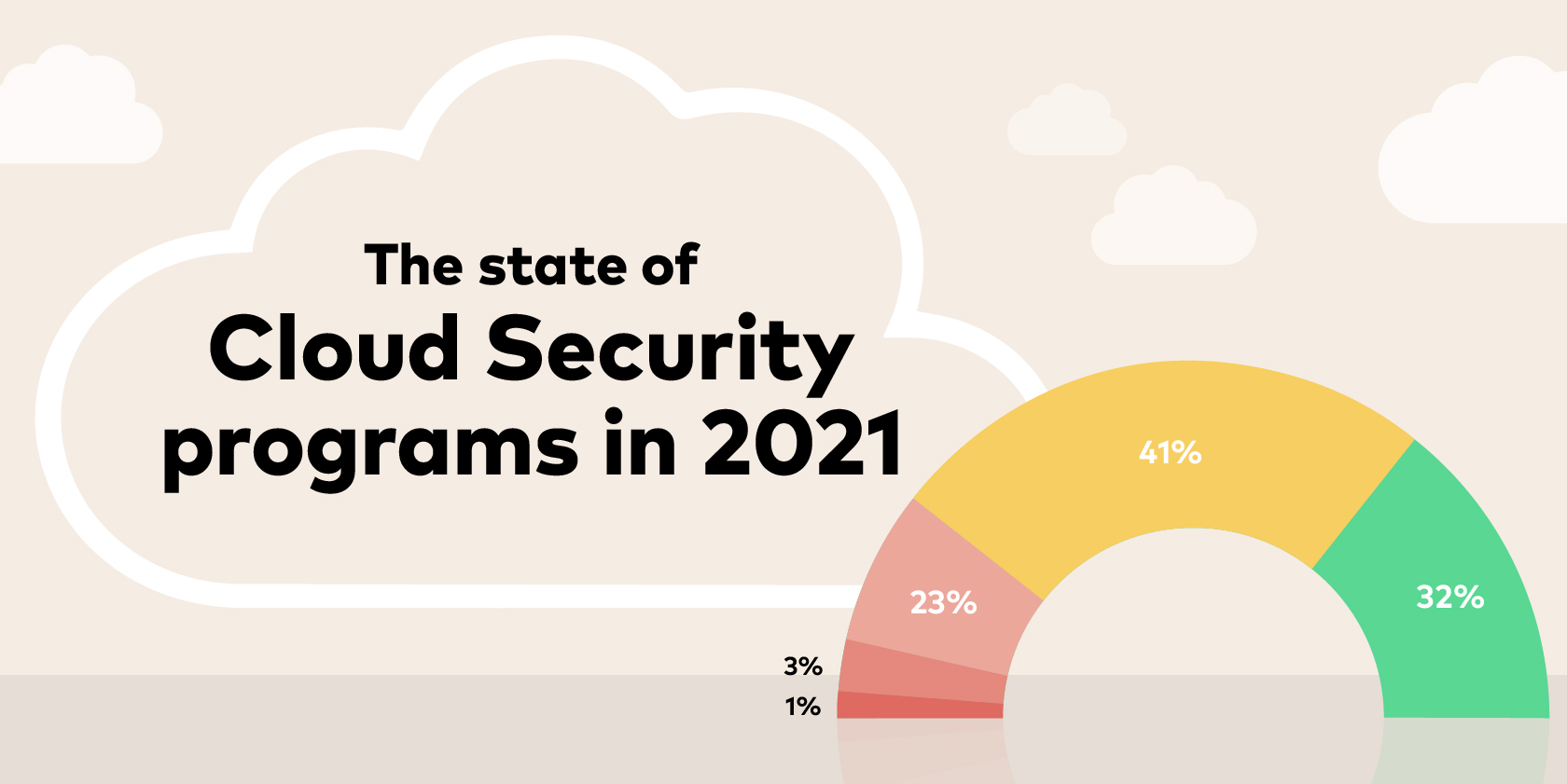
As companies accelerate their transition to the cloud, teams face a new category of cyber attack. This poses new problems and threatens the stability of enterprise workloads, and worse – client data. The benefits of cloud environments are clear, but the consequences of ineffective enterprise cloud security programs cast a dark shadow.
Using data from the likes of Gartner, Flexera and Fortinet, the below infographic shows how organizations are managing their cloud migration and addressing potentially prohibitive security concerns.

The need to become more efficient and more scalable never goes away for organizations, but security concerns must be addressed from the outset. This can be daunting, particularly when adapting to new technologies or multi-cloud environments, for example. Meanwhile, opportunistic hackers take advantage of the security gaps left by accelerated cloud migration but slow enterprise cloud security programs.
Vulnerability scanners and homegrown security tools might go some way to alleviate the threats, but create a mass of data that can cause confusion and more roadblocks for efficient security workflows. With security processes slowed down, attackers are free to exploit vulnerabilities, leading to major breaches and compromised client data.
It becomes clear that a single source of truth, consolidating all vulnerability data sources and prioritizing based on an organization’s unique cyber risk, has a drastic positive effect on teams’ ability to effectively manage workflows within their cloud environments.
With security under control, organizations can scale their cloud environments, comfortable in the knowledge that they are staying ahead of of their cyber risk.
A downloadable version of the above infographic can be found here.
For a deeper dive into some of the complexities of cloud security, click here.