First Officer’s log, Terrestrial date, 20220801. Officer of the Deck reporting.
Our presentations on 20220727 were quite successful, with mission professionals attending virtually from across the planet. It is always gratifying to know that people appreciate the work we do to support the mission and are willing to come and participate in a mission-focused conference. Fortunately, the proceedings were recorded so people who could not attend will still be able to share the experience. Access is available from Memory Alpha at the designated datalink.
I will be on shore leave for this coming week, so Officer of the Deck responsibilities will fall to one of my crew mates. I have every confidence in their abilities to maintain the level of professionalism those who rely on us have come to expect.
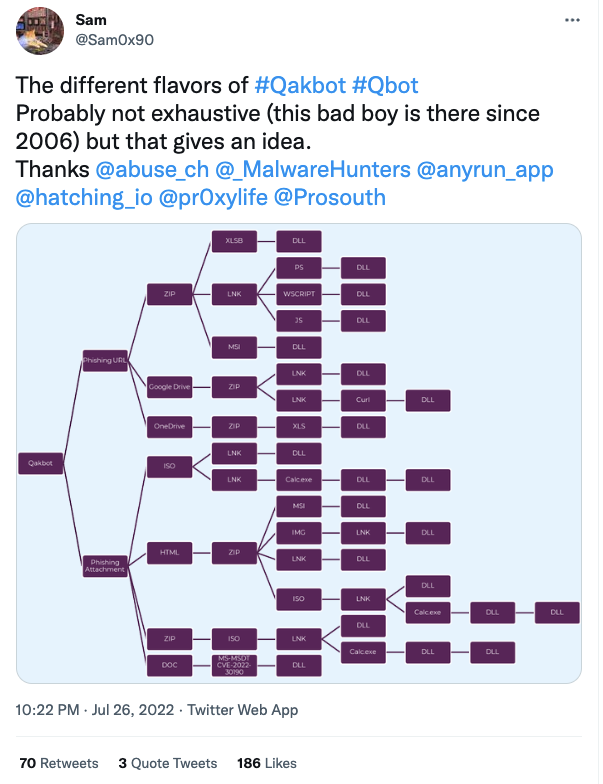
Qakbot chaos in Windows 7
What happened
Threat actors using the Qakbot (aka QBot) malware were discovered using the Windows 7 version of calc.exe to execute a DLL sideload attack and deploy their malware. The initial stage runs as a phishing attack, enticing victims to open a link, which launches Calc, which triggers the dll sideload and the infection.
Why it matters
The two real points here are that Qakbot starts as a phishing attack, where the user clicks on a link and initiates the infection. Which, by now, they should know better than to do. Of course, we know users are still falling for it, and the attackers know they’re still falling for it, which is why they use it. There are a lot of tools that can keep the spam from reaching the user, but the user still has to have the education to avoid the ones that get through.
The second factor here is that this dll sideload attack relies on the Windows 7 version of calc.exe, and Windows 7 has been End of Life for over two years now. We all know some organizations that have at least a few legacy systems in the environment, but Windows 7 in mid-2022? The attack won’t work against Windows 10 or newer. No word on Windows 8 or 8.1. But with Windows 11 out, there’s no reason an organization should be on an obsolete OS.
What they said
Appropriately for news about a hacked calculator, people are commenting by the numbers. See what people are saying about Qakbot.
All the malware rusting
What happened
A recently discovered piece of malware known as Luca Stealer written in the Rust programming language. The team at Cybel who documented the discovery suggests the original author may have released to code to gain some street cred for themselves. Which is not an unreasonable assumption, given the circumstances.
Why it matters
While Rust is gaining in popularity, it still lags behind a lot of the more widely known languages like C++, etc. in uptake. But that won’t stop malware writers from adopting it and finding the same advantages others have found when they moved to Rust. It kind of shows that any new tool will be abused at some point if it’s at all possible.
There doesn’t seem to be any indication that malware written in Rust is harder to detect than any other compiled malware, but the easier it is to write malicious code, the more malicious code, and variants of said code, we’re likely to see.
What they said
The vulnerability may be in code, but the ramifications are clear. Learn more.
Did it come from outer space?
What happened
Malware authors and threat actors will use whatever tool they can to get the job done, especially if it is effective. A recent report by SpiderLabs, attackers have been leveraging the InterPlanetary File System (IPFS) to host their phishing attack payloads. IPFS has a number of advantages for legitimate users, and even more for malicious phishers, who can distribute their payloads to help avoid being removed and may be able to leverage the legitimate SSL certificate from the IPFS site to trick an unwary victim.
Why it matters
Stopping phishers and malware distribution takes a layered approach. User education is always the first step, but there are tools to block malicious emails, defend the endpoints, and block the users from reaching malware-hosting sites. Moving to distribution helps threat actors avoid that particular layer of defense, by distributing the payload and making it harder to block.
What they said
As expected, any news about phishing gets plenty of coverage. Check it out.
Want to get ahead of the stories? Join the conversations as they happen with the Vulcan Cyber community Slack channel