First Officer’s log, Terrestrial date, 20221003. Officer of the Deck reporting.
We’ve gotten a final favorable report on the planetary defense network update on [REDACTED] from Lieutenant [REDACTED] and will be returning there to recover the team shortly. To the delight of the planetary government, the team was able to finish on time and within budget, using the Federation-supplied equipment to integrate the existing systems.
While the [REDACTED] were never willing to admit that the logic system they implemented with their planetary shield system was simply too complex for its own good, we were able to use the universal translator integrated into our communications platform to perform translations on the fly into a more generally useful form.
They agreed our solution was logical.
We were able to achieve similar results with the [REDACTED] sourced point defense. By leveraging the translator and part of our bi-directional communication capabilities, we were able to give the point defense better targeting information so it would stop trying to shoot down friendly spacecraft.
While they are still not entirely pleased someone else is telling them what to do, their representatives have said they believe we acted honorably and rescinded their demand for ritual combat to settle the matter.
Unfortunately, at least for the [REDACTED] sales reps, the traffic control system has proven to be impossible to integrate. With virtually anything. While we could receive data from it, the data was either redundant or useless, or both. And while we could send command requests to it, the system had no way to act on external information.
The government’s planetary security team admitted, after the fact, that the system had been forced on them by a senior Minister with ties to the [REDACTED] vendor. That led to some discussions in Parliament that we were not privy to, ultimately leading to a decision to completely remove the traffic control system and have ours fill that role. While the equipment we deployed wasn’t specifically designed to handle that duty, it is well within our capabilities.
When the [REDACTED] were told their system was being removed because it didn’t actually work, the response was essentially:
Rep #1: “Our system does not work.”
Rep #2: “Yes. Our system does not work.”
We will be returning to [REDACTED] to retrieve the team within the next day or so, once we finish the current assignment. I have put Lieutenant [REDACTED] in for a commendation for both her extraordinary work in getting the system deployed and for not phasering any of the vendor reps.
Overall, a good mission.
What’s in a name? A completely incomprehensible name. . .
What happened
Researchers at Akamai have flagged nearly 79 million newly created malicious domains during the first half of 2022. That works out to roughly 13 million new ones a month, which is over 20% of the total newly created domains during any given month.
Why it matters
Threat actors have used and abused the DNS system for multiple reasons almost since its inception. In fact, user education usually included something on how to identify a typo-squatted domain name. But Human-readable domains aren’t the only ones malicious actors will leverage. Their bots don’t care whether the domain name makes sense. They only care if it resolves. Which is why you’ll see them reaching out to domains that make absolutely no sense, and why millions of those garbage domains are created in the first place.
Threat actors need that stack of disposable domains because they can get shut down or blocked by gateway software pretty quickly. The problem’s big enough that there are entire products based on identifying malicious domains and keeping users from resolving them, though what’s really needed is some kind of secure and validated standard to cut down on malicious domain registration in the first place.
What they said
Malicious domains might be on the rise, but they certainly aren’t going under the radar. Read more.
No, really. You can trust us.
What happened
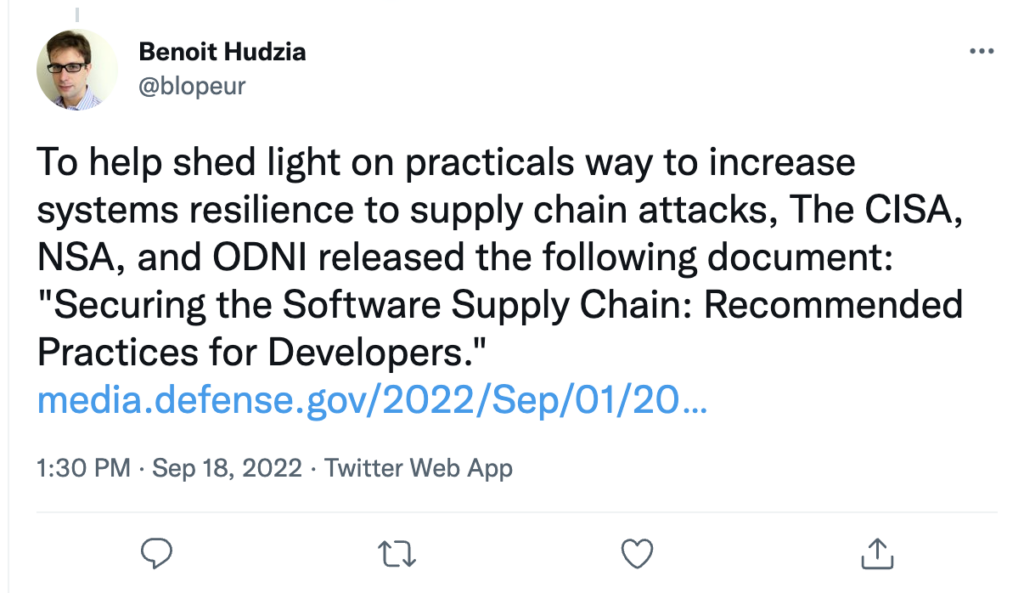
The National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA), and the Office of the Director of National Intelligence (DNI), have released guidance for developers on securing the software supply chain. The document, Securing the Software Supply Chain, is an effort to help developers secure their processes.
Why it matters
The NSA has a well-earned reputation for, well, spying on more or less everyone. Which leads people to question their motives whenever they give guidance on security or using cryptography, or anything else. But they have made some valuable contributions to the computing world that we rely on every day, and their charter also includes keeping their rivals from spying back. That said, consider the source but realize that they are very, very, good at what they do. If they suggest that something will keep you safer, it probably will.
And this isn’t just the NSA behind the guide. Both CISA and ODNI are involved, and their charter is very much to keep threat actors away. So, taken together, put away the paranoia, no matter how well justified, and take a look at the guide.
What they said
The news has been met with some positive industry reactions – and some questions.
New Exchange Server vulnerabilities (again)
What happened
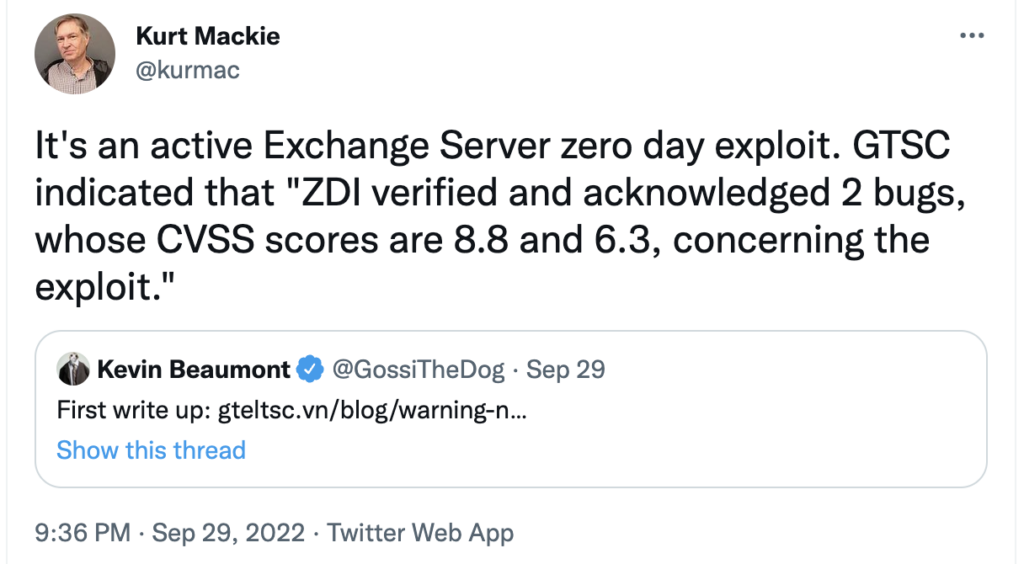
Researchers at Vietnamese cybersecurity firm GTSC have uncovered two new Microsoft Exchange Server vulnerabilities that are being exploited by threat actors believed to be based in China. Microsoft has acknowledged the Exchange Server vulnerabilities and released guidance on how to mitigate the issues until they can release a patch. Exchange Online does not appear to be affected by these new vulnerabilities.
Why it matters
Information on these new vulnerabilities is still coming to light, and there may be updates going forward. So far, the number of exploited systems appears to be relatively small and limited geographically, but once an exploit is in the wild it’s hard to say how far it will spread.
It’s likely that Microsoft will get a patch out quickly for these vulnerabilities, and organizations that have Exchange servers on-premises can deploy the workarounds now and patch them when those come out. We can hope this won’t turn into another mass exploitation event, which currently seems unlikely, but we’ll be keeping an eye on it and updating it as necessary.
What they said
We’ve been here before. But Microsoft Exchange Server Vulnerabilities will always get some attention.
___________________________________________________________________________________________________________________________
Want to get ahead of the stories? Join the conversations as they happen with the Vulcan Cyber community Slack channel