First Officer’s log, Terrestrial date, 20221212. Officer of the Deck reporting.
The captain has delayed our departure from Frontier Station [REDACTED] to let Ensign [REDACTED] participate in the final round of the 3D chess tournament, knowing it will mean traveling at higher Warp speeds in order to reach our next destination on schedule.
The final round of the tournament had our Ensign going head-to-head with the [REDACTED] who’d cheated his way into the final. Our crewmate made it to this stage fairly and we wanted to do what we could to make sure the game was played fairly at the end.
And for that, we had a plan.
Our Engineering team pulled some spare communications equipment from stores, left over from a previous operation, and adapted it to emit a subaudible frequency that would interfere with the back-channel communications the [REDACTED] was using to relay moves from their shipboard computer to the player at the table. If everything was working correctly it would be undetectable to anyone except, possibly, the cheating player and their spotter. It shouldn’t even cause any discomfort. But if it worked it would effectively act as a jammer and garble the communication.
The final round of the tournament was the event at the station, with a surprisingly good turnout from station personnel and visitors, including us.
For the opening, we left our signal jammer off, leaving the [REDACTED] undisturbed and, as expected, they opened strong. We waited several rounds, then turned the system on shortly before he made his 5th move and the effect was immediate. One moment he was faintly smiling, looking at the board as if contemplating his next move, and the next he was looking perplexed, then vaguely panicked.
He exchanged worried glances with his spotter, then, after considerably longer than his previous moves, he played.
From there, it was a foregone conclusion. With only his own skills, the [REDACTED] was no match for our Ensign and within a dozen moves he was forced to concede the game.
We did half expect him to complain about interference, but to do so would mean admitting that he’d been cheating all along and hadn’t made it to the finals on his own skill. Our Ensign, for his part, managed not to gloat about the win, even if it was a low-profile tournament on a Frontier Station that no one really paid any attention to.
Though that didn’t stop our crew from celebrating once we pulled away and entered Warp for our next destination, sharing the fact that we had somehow made the solo experience of 3D Chess into a team event.
Just in time for the holidays
What happened
Recent reporting indicates that many businesses are not prepared to deal with ransomware attacks or other security incidents over the holiday period. A combination of staffing issues increased pressure from threat actors, and business needs all contribute to increased risks during the end-of-year period.
Why it matters
For many organizations in the US and Europe, the holiday period can be very hectic. With retail outlets experiencing some of the most frantic time of the year, whole other industries are experiencing exactly the opposite with much of the staff having days off work.
Cybersecurity teams during this period can be caught somewhere in the middle, with many of the team wanting to spend time with family while their adversaries take advantage of the situation to launch a last round of attacks before the new year.
Advice? Get that last round of patches in. Make sure the team knows who’s on-call. And be prepared for either a blissful quiet, or some hectic long nights, depending on how it all comes together.
What they said
Something tells us this story might be the gift that keeps on giving.
The machine learned to do what, exactly?
What happened
Researchers have developed a proof-of-concept exploit that can deliver obfuscated malware through a downloaded machine-learning model. While there is no evidence that threat actors have used this technique in the wild, it shows that doing so is technically possible. This could enable attackers to deploy malware that would be largely undetectable until the model was unpacked and executed on the endpoint.
Why it matters
Threat actors are always looking for ways to bypass their target’s defenses. While this technique is somewhat convoluted, and there are much easier ways to land malware on a target, the fact that pre-built machine learning models for some popular machine learning engines can be “infected” with malware theoretically gives threat actors yet another way to ply their trade.
There is currently no evidence that this is being done, and other defenses on the endpoint or looking for other malware behaviors could detect it after the fact. Still, it means more files to sanitize between download and deployment.
What they said
Machine learning is all the rage. Read more.
Shared infrastructure. Shared problems.
What happened
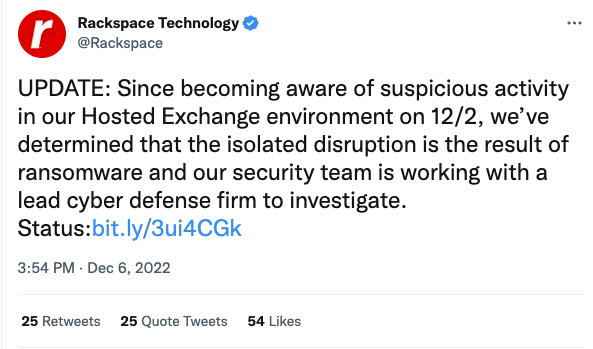
A breach of Rackspace’s hosted Exchange services has left multiple customers without their data and Rackspace helping to migrate many of these customers to Microsoft’s Exchange 365 platform while they help their customers recover. While there is some speculation that the Rackspace breach may have leveraged the ProxyNotShell vulnerability, Rackspace has not confirmed details.
Why it matters
The specifics of how the attackers executed the Rackspace breach isn’t necessarily as notable as the fact that the attack affected multiple customers of Rackspace’s service. One of the reasons for moving to cloud instances and software as a service (SaaS) or infrastructure as a service (IaaS) model is that the hosts are responsible for the platform’s security and, at least in theory, will do a better job of it than you could do yourself.
Rackspace reacted quickly to try and get their customers back on their feet, but it points out what can happen when things go wrong in the cloud at the host level.
What they said
It’s no surprise to see a notable attack get plenty of attention, and the Rackspace breach is no different.
__________________________________________________________________________________________________________________________
Want to get ahead of the stories? Join the conversations as they happen with the Vulcan Cyber community Slack channel