First Officer’s log, Terrestrial date, 20230109. Officer of the Deck reporting.
The USS [REDACTED] has reached Starbase 998 to undergo a round of required inspections after the incident with our Warp Drive controller, a faux chess fan, and a well-intentioned scientist a bit lacking in security awareness. While our own Engineering and IT teams are more than competent, Starfleet regulations require a full inspection as soon as possible after an incident like this. Which means we will be here at 998 for at least a few days. Possibly longer if they find evidence the breach was deeper than anticipated.
This did put some additional delay into our schedule but was necessary given what had happened. There had been cases in the past where a ship’s computing systems were compromised, and they continued after an initial cleanup, only to find the attackers had left other presents for the crew buried deeper in the systems than expected. As a support ship, our mission was more flexible when something like this came up. Where a front-line combat ship might have been too important to draw back to base and an exploration ship might have been too far from support to follow the process, that wasn’t us.
The captain was confident our teams had acted quickly and correctly and didn’t expect the investigation and cleanup teams to find anything left in our systems. Still, it was worth taking the time to check. You never knew if something was missed or if the attacker had found some new technique.
It wasn’t how we planned to start our new calendar year, but there were already requests coming in from the starbase for our assistance, so this wouldn’t be a wasted stop.
As for the worlds expecting us down the line, they’d have to accept the delay, since Starfleet didn’t have that many options available as substitutes for what we do.
Your average home user needs to do what?
What happened
A vulnerability was revealed in popular router models from Netgear, tracked as CVE-2022-48196. Owners of the affected equipment are urged to update their routers with the latest firmware as soon as practical.
Why it matters
While there’s no word yet on what a threat actor could do if they exploited the vulnerability, or if there are any exploits in the wild, it is still best to update. The challenge is that a lot of home users rarely, if ever, update their equipment. It’s not that the process is difficult, because it’s usually very straightforward. The problem is that unless a home user is in IT themselves, they don’t think about it. And even if they are in IT, they often neglect the home equipment.
But you are reading this, so you know to update your own home equipment. Right?
What they said
With routers being such a ubiquitous household and office fixture, it’s no surprise to see this story getting plenty of attention.
Sure, we can totally trust the supply chain
What happened
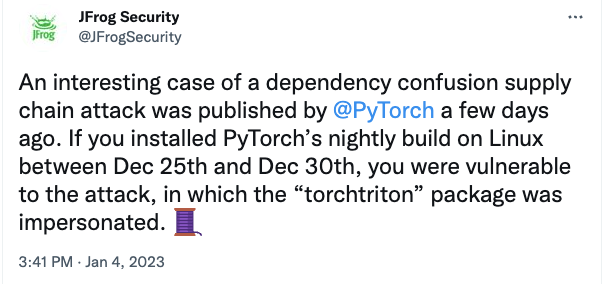
An unknown actor compromised the torchtriton library on the PyPI repository using a dependency confusion attack. This library is used by PyTorch, a framework used for machine learning development. Developers who built PyTorch between 25 December and 30 December 2022 are advised to uninstall it and rebuild using the nightly build dated after 30 December 2022.
The attacker has claimed that this was the result of a research project gone awry, has apologized, and said that all exfiltrated data has been deleted.
Why it matters
While this may very well just be a security research project gone bad, it points out one of the (multiple) vulnerabilities in the existing software development supply chain. And there are a fair number of them. It also brings up the question of who’s responsible for it when these things happen. Obviously, the attacker is responsible, but who’s responsible for keeping the repos clean? Does that fall to PyPI or GitHub, or any of the others? Or does it fall to the developers to vet everything they include? Both?
Open Source has myriad advantages that, in total, outweigh the few disadvantages, like this one, that can impact the development supply chain.
What they said
This one had a lot of people talking.
Seriously, you knew this was coming!
What happened
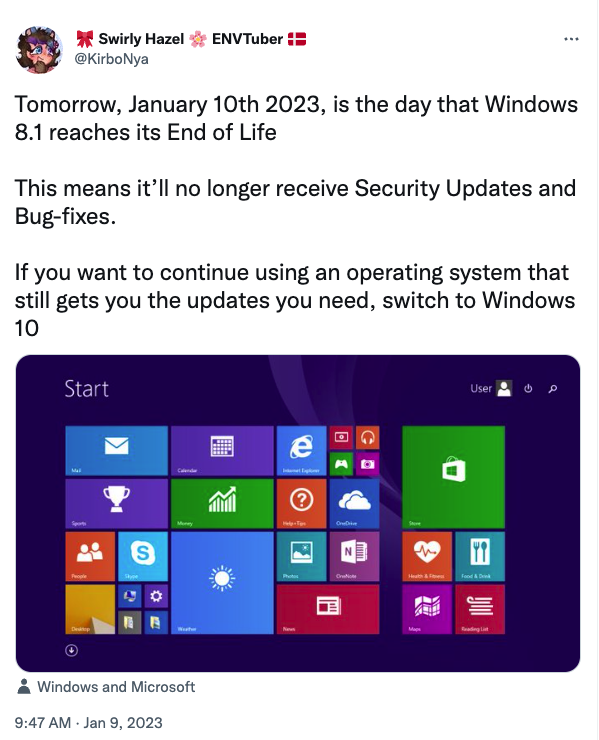
As previously announced, Microsoft will stop supporting Windows 8.1 on Jan. 10. This follows their end of support for Windows 7 back in January 2020. This expected end of life is expected to have an impact on organizations that rely on systems that cannot be easily upgraded to a more recent OS.
Why it matters
Windows 8.1 reaching End of Life and losing support has been expected for years. Literally. Years. But there are some organizations that will still struggle to deal with losing support. There are a lot of reasons it can be an issue, from having specialized, vital, applications that still rely on Windows 8.1 and haven’t been updated, if they’re even still supported, to having budget constraints that force them to keep old equipment running well past it’s Best Before date.
Organizations that find themselves in this situation are going to have to either put in compensating controls and hope for the best until they can upgrade or replace the kit, or bite the bullet sooner rather than later and replace the obsolete systems now before the lack of updates leads to an otherwise preventable compromise.
What they said
With the ramifications potentially significant, there’s been a good amount coverage about the end of Windows 8.1.
__________________________________________________________________________________________________________________________
Want to get ahead of the stories? Join the conversations as they happen with the Vulcan Cyber community Slack channel