Update: The login issue has been resolved as of Monday, December 18, 2023.
MongoDB is a key player in the database software industry, catering to a vast array of businesses and individual users worldwide. However, this reputation for innovation and reliability faced a challenge when the company encountered a significant security incident.
This blog post delves into the details of the unauthorized access to MongoDB’s corporate systems, a development that has raised concerns in the cyber security community and among MongoDB’s extensive user base.
Here’s everything we know so far.
Incident discovery and immediate response
The security breach came to light on December 13, 2023, when MongoDB detected unusual activity indicating unauthorized access to certain corporate systems. This discovery was not just a momentary lapse but hinted at a more prolonged period of vulnerability, suggesting that the unauthorized access might have been occurring undetected for some time.
Upon identifying this breach, MongoDB swiftly activated its incident response plan. This rapid response underscores the company’s commitment to security and its readiness to address such threats. The incident response team at MongoDB sprang into action, aiming to assess the scope of the breach, contain the incident, and prevent further unauthorized access.
This section of the incident is particularly crucial as it highlights the importance of having robust detection mechanisms and a well-prepared incident response strategy. For MongoDB, the ability to quickly detect and respond to the breach played a pivotal role in mitigating potential damage.
However, the revelation that the unauthorized access might have been ongoing before its discovery raises significant questions about the duration of the exposure and the extent of the information that might have been compromised. This aspect of the incident serves as a stark reminder of the persistent and evolving nature of cyber security threats in today’s digital landscape.
Impact and fallout
The unauthorized access to MongoDB’s corporate systems has led to the exposure of sensitive customer data, a development that has understandably caused concern among its users. The data compromised in this breach primarily includes customer account metadata and contact details. This information, while not directly impacting the integrity of the data stored within MongoDB’s databases, still represents a significant privacy concern for the affected individuals and organizations.
Most notably, MongoDB has assured its users that there has been no known exposure of data stored by customers in MongoDB Atlas, the company’s fully managed cloud database service. This clarification is crucial as it helps to alleviate concerns about the security of critical data hosted on MongoDB’s cloud platform. However, the exposure of account metadata and contact details is not a matter to be taken lightly, as it could potentially be leveraged for targeted social engineering or phishing attacks.
For MongoDB’s customers, this incident underscores the need for continuous vigilance and robust security practices, not just at the organizational level but also for individual users. The fallout from this breach is a clear indication that cyber security is an ongoing battle, requiring constant attention and proactive measures to safeguard sensitive information.
Customer advisory and precautionary measures
In the wake of the security breach, MongoDB has taken a proactive stance in advising its customers on how to safeguard their accounts and data. Recognizing the potential risks posed by the exposure of customer account metadata and contact details, MongoDB urges all its users to be particularly vigilant against social engineering and phishing attacks. These types of attacks often exploit personal information to gain trust and manipulate individuals into divulging confidential information or performing actions that compromise security.
To enhance account security, MongoDB strongly recommends the enforcement of phishing-resistant multi-factor authentication (MFA). MFA adds an additional layer of security, making it significantly more difficult for unauthorized parties to gain access even if they have obtained a user’s credentials. This measure is particularly effective against the types of attacks that might stem from the data exposed in this incident.
Additionally, MongoDB advises its customers to undertake regular password rotations. Changing passwords periodically is a fundamental security practice that can prevent ongoing unauthorized access, especially in scenarios where credentials might have been compromised without the user’s knowledge.
The bottom line
As discussed above, this latest data breach demonstrates two things. First, the increasing growth of the attack surface. The below image shows just how complex things have become for enterprise security teams, and how many tools they need just to maintain visibility of their environments:
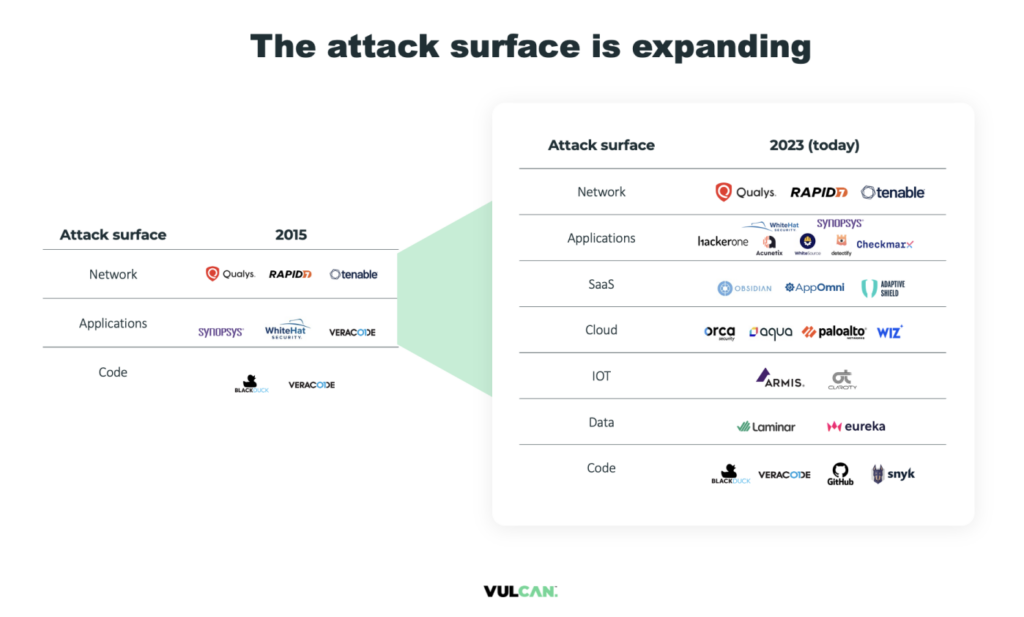
Moreover, this breach underlines the need for teams to take swift action on the threats that matter most. An incident response plan is essential, while effective risk-based vulnerability management ensures that the biggest cyber risks are identified and mitigated before they can cause real damage to organizations or their customers.
The Vulcan Cyber risk management platform enables end-to-end risk correlation, prioritization, and mitigation across the entire attack surface. Book a demo today.









