-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
Microsoft's May 2024 Patch Tuesday addresses 67 vulnerabilities, including critical zero-days. Key updates cover Windows, Office, and Visual Studio.

Microsoft Patch Tuesday’s May 2024 edition addressed 67 vulnerabilities, including one critical and 59 important severity vulnerabilities. Also in this month’s security updates, Microsoft has addressed zero-day vulnerabilities known to be exploited in the wild.
Here’s what you need to know.
Microsoft’s May 2024 Patch Tuesday addresses 67 vulnerabilities, including critical zero-days. Key updates include fixes for Windows, Office, and Visual Studio. Highlights include patches for remote code execution vulnerabilities in SharePoint Server and Hyper-V, and elevation of privilege vulnerabilities in the DWM Core Library.
The release also addresses bugs in lesser-used protocols and components like Windows Mobile Broadband. Microsoft emphasizes the importance of timely updates to mitigate risks from these actively exploited vulnerabilities.
This month, Microsoft released updates addressing 59 CVEs across Windows and Windows Components;
Microsoft Office and Components, Power BI, Visual Studio, Windows Cloud Files Mini Filter Driver, Windows Common Log File System Driver, Windows Cryptographic Services, .NET Framework and Visual Studio, Microsoft Dynamics 365, DHCP Server, Microsoft Edge (Chromium-based) and Windows Mobile Broadband.
Including third-party CVEs documented this month, the total count rises to 63, of which two vulnerabilities were reported through the ZDI program. Unlike Apple and VMware, which have addressed vulnerabilities reported at Pwn2Own Vancouver, Microsoft has yet to release patches for those disclosed during the contest.
Additionally, this release is about one-third the size of last month’s, which may indicate that the large volume of fixes seen previously will not become a regular occurrence. Two of the CVEs addressed this month are actively being exploited, and one is publicly known at the time of release. Although Microsoft does not specify the volume of attacks, the DWM Core bug appears to be more than a targeted attack. Here are some of the most notable updates for this month, starting with the DWM bug currently exploited in the wild:
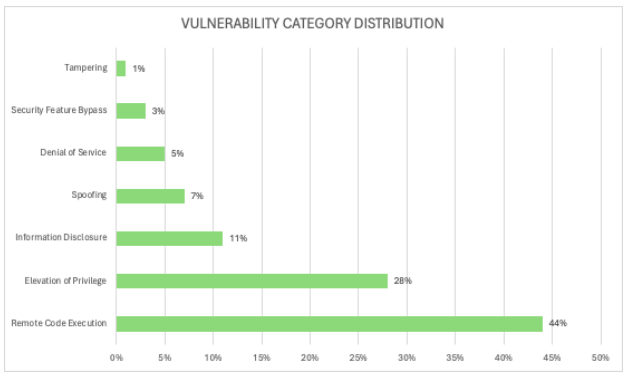
This month’s Update focuses primarily on vulnerabilities and patches across various Microsoft products. Starting with the Critical-rated vulnerability, there’s a remote code execution (RCE) flaw in SharePoint server. Exploiting this could allow an attacker to execute code in the context of the SharePoint Server, provided they have the necessary permissions.
Moving on to other RCE vulnerabilities, we see several in rarely used protocols such as the Windows Mobile Broadband driver and the Routing and Remote Access Service (RRAS). Noteworthy are also the bugs in Hyper-V, where one permits code execution on the host system, potentially leading to a guest-to-host escape scenario.
In terms of elevation of privilege (EoP) patches, almost all could result in SYSTEM-level code execution if a user runs specially crafted code. These are commonly exploited alongside code execution bugs to gain system control. However, there’s an exception with the bug in the Brokering File System component, which allows attackers to authenticate against a remote host using current user credentials.
Regarding security feature bypass (SFB) vulnerabilities, there’s a fix for the MSHTML engine, reminding us of potential code execution risks if malicious documents are opened.
Information disclosure bugs are limited this month, mostly resulting in info leaks of unspecified memory contents. However, the bug in Power BI and Deployment Services raises concerns about potential leakage of sensitive information, although specifics are not detailed by Microsoft.
Spoofing bugs are also addressed, including an XSS issue in Azure Migrate and Dynamics 365, along with a spoofing bug in the Bing search engine, emphasizing the need for vigilance against malicious redirections.
A single Tampering bug in Microsoft Intune Mobile Application Management is fixed, preventing potential disclosure of sensitive information on rooted target devices.
Lastly, there are Denial-of-Service (DoS) vulnerabilities in ASP.NET, DHCP server, and Hyper-V, although Microsoft hasn’t provided extensive details on these issues.
|
Vulnerability Category |
Quantity |
Severities |
|
Remote Code Execution Vulnerability |
27 |
Critical: 1 |
|
Elevation of Privilege Vulnerability |
17 |
Important: 17 |
|
Information Disclosure Vulnerability |
7 |
Important: 7 |
|
Spoofing Vulnerability |
4 |
Important: 4 |
|
Denial of Service Vulnerability |
3 |
Important: 3 |
|
Security Feature Bypass Vulnerability |
2 |
Important: 1 |
|
Tampering Vulnerability |
1 |
Important: 1 |
This Zero-Day vulnerability allows attackers to escalate privileges to SYSTEM on affected systems. Typically, such bugs are combined with code execution vulnerabilities to fully compromise a target, and they are frequently utilized by ransomware.
Microsoft credits four different groups for reporting this bug, indicating widespread attacks. The vulnerability is also publicly known. It is crucial to test and deploy this update promptly, as exploits are likely to increase now that a patch is available for reverse engineering.
Reported by ZDI researcher Piotr Bazydło, this XML external entity injection (XXE) vulnerability affects Microsoft SharePoint Server 2019.
An authenticated attacker could exploit this bug to read local files with the SharePoint Farm service account’s privileges, execute HTTP-based server-side request forgery (SSRF), and most significantly, perform NTLM relaying as the SharePoint Farm service account. This highlights the importance of not ignoring or deprioritizing information disclosure vulnerabilities.
This vulnerability, reported through the ZDI program, has a similar impact to another currently exploited bug but operates through a different mechanism. It is a link-following bug in the Windows Search service. By creating a pseudo-symlink, an attacker could redirect a delete operation to remove a different file or folder as SYSTEM. This can elevate privileges when the service restarts. Although a low-privileged user can’t directly restart the service, this vulnerability can be combined with a bug that allows a low-privileged user to terminate any process by PID. The service will restart automatically after termination, successfully triggering the vulnerability.
Windows MSHTML, the browser engine used to render web pages, is still relevant despite the end of support for the Internet Explorer 11 desktop application. Microsoft continues to patch MSHTML vulnerabilities.
This Zero-Day vulnerability can bypass OLE mitigations in Microsoft 365 and Microsoft Office, which protect users from vulnerable COM/OLE controls. An unauthenticated attacker could exploit this vulnerability by convincing a user to open a malicious document, potentially executing code.
CISA has added this CVE to its Known Exploited Vulnerabilities Catalog and has advised users to patch it before May 6, 2024.
CVE-2024-30050 – A security feature bypass vulnerability in Windows Mark of the Web. An attacker could exploit this by hosting a file on a server and convincing a targeted user to download and open it. Successful exploitation might alter the functionality of the Mark of the Web.
CVE-2024-29996 and CVE-2024-30025 – Elevation of privilege vulnerabilities in the Windows Common Log File System Driver. Successful exploitation could allow an attacker to gain SYSTEM privileges.
CVE-2024-30032 – An elevation of privilege vulnerability in the Windows DWM Core Library. Exploiting this vulnerability could grant an attacker SYSTEM privileges.
CVE-2024-30034 and CVE-2024-30035 – Information disclosure vulnerabilities in the Windows Cloud Files Mini Filter Driver. Successful exploitation might allow an attacker to disclose certain kernel memory content.
CVE-2024-30038 – An elevation of privilege vulnerability in Win32k. A local, authenticated attacker could exploit this vulnerability to gain elevated local system or administrator privileges.
CVE-2024-30049 – An elevation of privilege vulnerability in the Windows Win32 Kernel Subsystem
Successful exploitation could enable an attacker to gain SYSTEM privileges.
CVE-2024-30046 – Visual Studio: Zero-Day DoS This vulnerability is a denial of service (DoS) issue in Visual Studio. Described by Microsoft, CVE-2024-30046 involves a highly complex attack that exploits a race condition through the repeated sending of constant or intermittent data. Due to the lack of detail in the advisory, the potential impact of this exploitation remains unclear. Only Visual Studio 2022 has received an update, indicating that older supported versions are presumably unaffected.
CVE-2024-30044 – SharePoint: Critical Post-Auth RCE
SharePoint administrators are familiar with patches for critical remote code execution (RCE) vulnerabilities. CVE-2024-30044 allows an authenticated attacker with Site Owner permissions or higher to execute code within SharePoint Server by uploading a specially crafted file and using specific API calls to trigger deserialization of the file’s parameters.
Microsoft considers exploitation of CVE-2024-30044 likely. Initially, the advisory incorrectly listed the “privileges required” as low, but it has been updated to high, reflecting the Site Owner authentication requirement. The advisory’s FAQ still contains some confusing wording, but the correction to the CVSS vector is a welcome change.
The vulnerability’s low attack complexity and network attack vector contribute to a CVSS 3.1 base score of 7.2, reduced from the original score of 8.8 after the CVSS vector correction. Microsoft has published an introduction to deserialization vulnerabilities, highlighting the risks of assuming data to be trustworthy, aimed at .NET developers.
Here is the entire list of CVEs in May’s Microsoft Patch Tuesday release:
|
CVE |
Title |
Severity |
CVSS |
Exploited |
Type |
|
CVE-2024-30044 |
Microsoft SharePoint Server Remote Code Execution Vulnerability |
Critical |
8.8 |
No |
RCE |
|
CVE-2024-4331 * |
Chromium: CVE-2024-4331 Use after free in Picture In Picture |
High |
N/A |
No |
RCE |
|
CVE-2024-4368* |
Chromium: CVE-2024-4368 Use after free in Dawn |
High |
N/A |
No |
RCE |
|
CVE-2024-30051 |
Windows DWM Core Library Elevation of Privilege Vulnerability |
Important |
7.8 |
Yes |
EoP |
|
CVE-2024-30040 |
Windows MSHTML Platform Security Feature Bypass Vulnerability |
Important |
8.8 |
Yes |
SFB |
|
CVE-2024-30046 |
ASP.NET Core Denial of Service Vulnerability |
Important |
5.9 |
No |
DoS |
|
CVE-2024-30045 |
.NET and Visual Studio Remote Code Execution Vulnerability |
Important |
6.3 |
No |
RCE |
|
CVE-2024-30053# |
Azure Migrate Spoofing Vulnerability |
Important |
7.5 |
No |
Spoofing |
|
CVE-2024-32002* |
CVE-2023-32002 Recursive clones on case-insensitive filesystems that support symlinks are susceptible to Remote Code Execution |
Important |
9.8 |
No |
RCE |
|
CVE-2024-30019 |
DHCP Server Service Denial of Service Vulnerability |
Important |
6.5 |
No |
DoS |
|
CVE-2024-30047 |
Dynamics 365 Customer Insights Spoofing Vulnerability |
Important |
7.6 |
No |
Spoofing |
|
CVE-2024-30048 |
Dynamics 365 Customer Insights Spoofing Vulnerability |
Important |
7.6 |
No |
Spoofing |
|
CVE-2024-32004 * |
GitHub: CVE-2024-32004 GitHub: CVE-2023-32004 Remote Code Execution while cloning special-crafted local repositories |
Important |
8.8 |
No |
RCE |
|
CVE-2024-30041 |
Microsoft Bing Search Spoofing Vulnerability |
Important |
5.4 |
No |
Spoofing |
|
CVE-2024-30007 |
Microsoft Brokering File System Elevation of Privilege Vulnerability |
Important |
8.8 |
No |
EoP |
|
CVE-2024-30042 |
Microsoft Excel Remote Code Execution Vulnerability |
Important |
7.8 |
No |
RCE |
|
CVE-2024-26238 |
Microsoft PLUGScheduler Scheduled Task Elevation of Privilege Vulnerability |
Important |
7.8 |
No |
EoP |
|
CVE-2024-30054 |
Microsoft Power BI Client Javascript SDK Information Disclosure Vulnerability |
Important |
6.5 |
No |
Info |
|
CVE-2024-30043 |
Microsoft SharePoint Server Information Disclosure Vulnerability |
Important |
6.5 |
No |
Info |
|
CVE-2024-30006 |
Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
Important |
8.8 |
No |
RCE |
|
CVE-2024-29994 |
Microsoft Windows SCSI Class System File Elevation of Privilege Vulnerability |
Important |
7.8 |
No |
EoP |
|
CVE-2024-30027 |
NTFS Elevation of Privilege Vulnerability |
Important |
7.8 |
No |
EoP |
|
CVE-2024-30028 |
Win32k Elevation of Privilege Vulnerability |
Important |
7.8 |
No |
EoP |
|
CVE-2024-30030 |
Win32k Elevation of Privilege Vulnerability |
Important |
7.8 |
No |
EoP |
|
CVE-2024-30038 |
Win32k Elevation of Privilege Vulnerability |
Important |
7.8 |
No |
EoP |
|
CVE-2024-30034 |
Windows Cloud Files Mini Filter Driver Information Disclosure Vulnerability |
Important |
5.5 |
No |
Info |
|
CVE-2024-30031 |
Windows CNG Key Isolation Service Elevation of Privilege Vulnerability |
Important |
7.8 |
No |
EoP |
|
CVE-2024-29996 |
Windows Common Log File System Driver Elevation of Privilege Vulnerability |
Important |
7.8 |
No |
EoP |
|
CVE-2024-30025 |
Windows Common Log File System Driver Elevation of Privilege Vulnerability |
Important |
7.8 |
No |
EoP |
|
CVE-2024-30037 |
Windows Common Log File System Driver Elevation of Privilege Vulnerability |
Important |
7.5 |
No |
EoP |
|
CVE-2024-30016 |
Windows Cryptographic Services Information Disclosure Vulnerability |
Important |
5.5 |
No |
Info |
|
CVE-2024-30020 |
Windows Cryptographic Services Remote Code Execution Vulnerability |
Important |
8.1 |
No |
RCE |
|
CVE-2024-30036 |
Windows Deployment Services Information Disclosure Vulnerability |
Important |
6.5 |
No |
Info |
|
CVE-2024-30032 |
Windows DWM Core Library Elevation of Privilege Vulnerability |
Important |
7.8 |
No |
EoP |
|
CVE-2024-30035 |
Windows DWM Core Library Elevation of Privilege Vulnerability |
Important |
7.8 |
No |
EoP |
|
CVE-2024-30008 |
Windows DWM Core Library Information Disclosure Vulnerability |
Important |
5.5 |
No |
Info |
|
CVE-2024-30011 |
Windows Hyper-V Denial of Service Vulnerability |
Important |
6.5 |
No |
DoS |
|
CVE-2024-30010 |
Windows Hyper-V Remote Code Execution Vulnerability |
Important |
8.8 |
No |
RCE |
|
CVE-2024-30017 |
Windows Hyper-V Remote Code Execution Vulnerability |
Important |
8.8 |
No |
RCE |
|
CVE-2024-30018 |
Windows Kernel Elevation of Privilege Vulnerability |
Important |
7.8 |
No |
EoP |
|
CVE-2024-29997 |
Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
Important |
6.8 |
No |
RCE |
|
CVE-2024-29998 |
Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
Important |
6.8 |
No |
RCE |
|
CVE-2024-29999 |
Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
Important |
6.8 |
No |
RCE |
|
CVE-2024-30000 |
Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
Important |
6.8 |
No |
RCE |
|
CVE-2024-30001 |
Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
Important |
6.8 |
No |
RCE |
|
CVE-2024-30002 |
Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
Important |
6.8 |
No |
RCE |
|
CVE-2024-30003 |
Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
Important |
6.8 |
No |
RCE |
|
CVE-2024-30004 |
Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
Important |
6.8 |
No |
RCE |
|
CVE-2024-30005 |
Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
Important |
6.8 |
No |
RCE |
|
CVE-2024-30012 |
Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
Important |
6.8 |
No |
RCE |
|
CVE-2024-30021 |
Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
Important |
6.8 |
No |
RCE |
|
CVE-2024-30039 |
Windows Remote Access Connection Manager Information Disclosure Vulnerability |
Important |
5.5 |
No |
Info |
|
CVE-2024-30009 |
Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
Important |
8.8 |
No |
RCE |
|
CVE-2024-30014 |
Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
Important |
7.5 |
No |
RCE |
|
CVE-2024-30015 |
Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
Important |
7.5 |
No |
RCE |
|
CVE-2024-30022 |
Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
Important |
7.5 |
No |
RCE |
|
CVE-2024-30023 |
Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
Important |
7.5 |
No |
RCE |
|
CVE-2024-30024 |
Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
Important |
7.5 |
No |
RCE |
|
CVE-2024-30029 |
Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
Important |
7.5 |
No |
RCE |
|
CVE-2024-30033 |
Windows Search Service Elevation of Privilege Vulnerability |
Important |
7 |
No |
EoP |
|
CVE-2024-30049 |
Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
Important |
7.8 |
No |
EoP |
|
CVE-2024-30059 |
Microsoft Intune for Android Mobile Application Management Tampering Vulnerability |
Important |
6.1 |
No |
Tampering |
|
CVE-2024-30050 |
Windows Mark of the Web Security Feature Bypass Vulnerability |
Moderate |
5.4 |
No |
SFB |
* Indicates CVE had been released by a third party
# Indicates further administrative actions are required to fully address the vulnerability.
Each new vulnerability is a reminder of where we stand and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors: