-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
Reduce exposure risk across all attack surfaces with the Vulcan Cyber ExposureOS™. Centralize, prioritize, and take action on your vulnerability risk findings to mitigate critical threats efficiently.
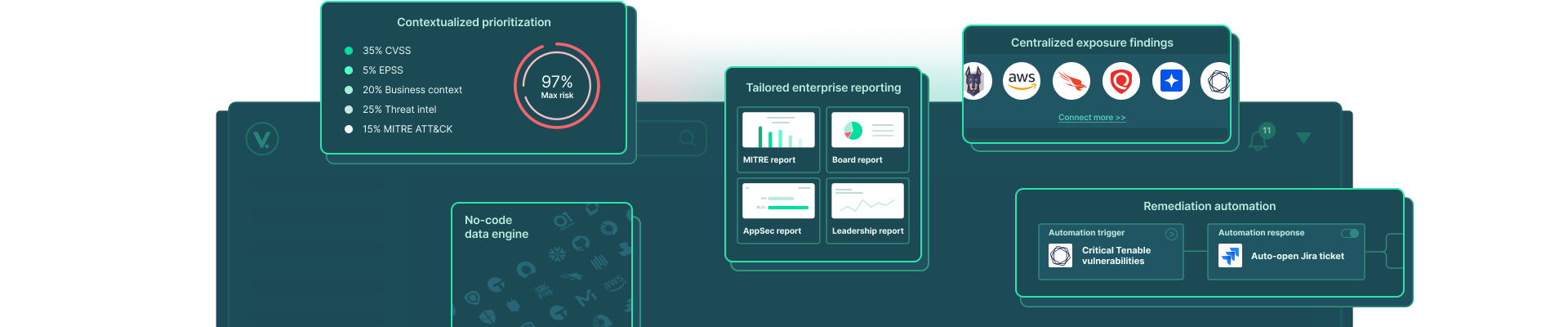

Consolidate all security findings into one holistic view to gain a full understanding of your exposure risk.
Complete visibility across the attack surface
Seamlessly connect to 100+ tools with our no-code integration engine.
Security tools
Compile security data from scanners, threat intelligence feeds, homegrown tools and data sources.
Asset inventory tools
Sync with your CMDB to view asset structure and dependencies.
Communication and ticketing tools
Integrate with collaborative tools to streamline cross-department workflows.
Learn more about vulnerability aggregation →

Normalize your security data
Correlate and normalize risk data to ensure accuracy and consistency.
Remove duplicates for clean data
Automatically identify duplicates ingested from multiple sources.
Organize data with smart clustering
Group vulnerabilities into clusters and take unified remediation actions.
Get a unified risk score
Combine risk signals from multiple sources to get a cohesive risk score.
Learn more about vulnerability correlation →

Go beyond technical severity scoring
Enrich security findings to ensure contextualized risk-based prioritization.
See asset risk in context
Use tags to enrich assets with business context and impact.
Utilize threat intelligence
Leverage built-in threat feeds with environmental and temporal intel.
Deliver remediation intelligence
Generate mitigation guidance for asset owners, powered by the largest remediation intelligence database.
Learn more about vulnerability intelligence →



Streamline your security operations to efficiently mitigate critical risk.
Separate true risk from exposure noise
Go beyond technical severity scoring to prioritize vulnerabilities based on business context.
Customize your risk scoring
Configure the impact of each vulnerability criteria on the overall score.
Prioritize across attack surfaces
Get full coverage by prioritizing any vulnerability or asset type.
Determine risk tolerance
Tag immaterial vulnerabilities as accepted risk.
Learn more about vulnerability prioritization →

Shorten the loop from scan to fix
Use sequenced workflows for a faster and more effective risk remediation process.
Automate remediation tasks
Automatically open tickets to relevant remediation owners.
Track remediation progress
Gain real-time visibility into remediation progress and SLA compliance.
Consistent remediation operations
Connect with ticketing tools for a smooth remediation process.
Learn more about remediation orchestration →

Make remediation a team effort
Automate remediation tasks for rapid vulnerability mitigation.
Apply remediation context
Provide asset owners with remediation intelligence and best practices.
Leverage dynamic ownership assignment
Automatically assign remediation tasks and update asset owners.
Streamline cross-functional collaboration
Integrate communication tools to share data and reduce the back-and-forth.
Learn more about collaborative security →

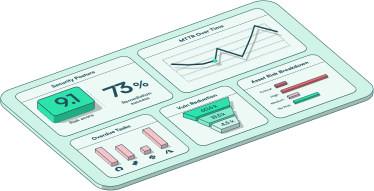
Utilize advanced reporting to track and analyze your exposure risk data.
Make data-driven mitigation decisions
Analyze and monitor your entire exposure risk management and remediation efforts.
Analyze your exposure risk
Use cohesive reporting to gain insights into your entire risk posture.
Filter results to suit your needs
Apply filters to hide irrelevant data and focus only on the risk data that matters most to you.
Drill down
Dig deeper into each data point for more detailed analysis.
Learn more about risk reporting →

Tailor reports to your teams’ needs
Build personalized reports catering to specific stakeholders, teams, and use cases.
Create custom reports
Start with pre-built reports and then tailor to your specific needs.
Customize widgets and visuals
Create personalized widgets to be re-used across your reports.
Control your sensitive data
Manage data access based on teams and roles to ensure confidentiality and compliance.
Learn more about risk reporting →

Communicate exposure risk across the organization
Clearly communicate the performance of your exposure risk management efforts.
Report to executives and board members
Provide a bird-eye view of exposure risk levels with concise reports tailored to leadership.
Track compliance with regulations
Align cyber security investments with regulatory requirements and monitor compliance.
Deliver actionable data
Share data-driven recommendations with the right teams at the right time.
Learn more about risk reporting →

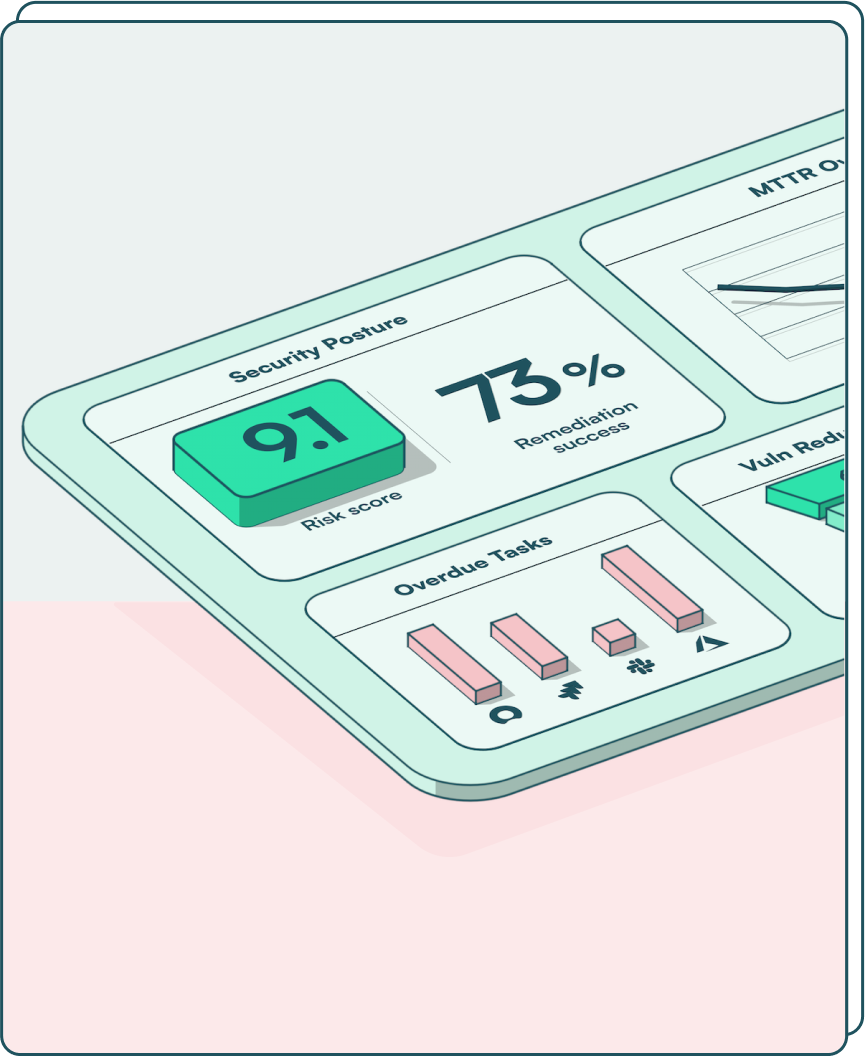
Manage all risk from one place
Focus on what matters most to you
Get buy-in from your remediation owners
Cut remediation timelines

“Vulnerability risk management at this level of scale would not be efficient, or even possible, without Vulcan Cyber risk prioritization and risk mitigation orchestration.”
Samira Jamnejad
Security Assurance Manager

“Our company uses Vulcan Cyber primarily for remediation tracking. Its matrix allows my team to quickly and accurately assess our current remediation trend and report this to our leadership in a way that is easy to digest. With its impressive asset management feature and CVE searching capabilities, Vulcan Cyber is an invaluable tool for any cyber-minded company.”
IT Analyst, Printing Company
“One of the best parts about Vulcan Cyber is its ability to ingest information from different sources, de-duplicate it, and present it on an easy-to-use platform.”
Security Engineer
Construction Company
“Vulcan Cyber is a wonderful tool for managing data, assets, and vulnerabilities from various sources. It’s a central hub for analyzing vulnerabilities, creating mitigation processes, and securing your organization’s data and assets. The tool offers great reporting, querying, and dashboards for understanding organizational risks.”
Engineer in Information Technology

“I was looking for a single platform where I could do everything at once. Manage vulnerabilities, keep track of remediation processes, and create reports that are easily consumable by my team and stakeholders”
Prajakta Badhe
Senior product security manager

“We use Vulcan Cyber to help with our technical debt. The ROI is almost immediate. It gives a better understanding of what assets are actually under real threat and allows much better prioritization.”
Director of IT, Marketing
& Advertising Company
“I’ve been working in Threat and Vulnerability management almost my entire security career. I have never seen a platform that is attempting to do what Vulcan Cyber is attempting to do.”
Neil Stewart
Director of Cyber Security


Jocelyn van Heerde
Application Security Engineer

“Our company uses Vulcan Cyber primarily for remediation tracking. It’s matrix allows my team to quickly and accurately assess our current remediation trend and report this to our leadership in a way that is easy to digest. With its impressive asset management feature and CVE searching capabilities, Vulcan is an invaluable tool for any cyber-minded company.”
IT Analyst, Printing Company

We use cookies to personalise content and ads, to provide social media features and to analyse our traffic. We also share information about your use of our site with our social media, advertising and analytics partners.
View more