-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
Cybersecurity researchers have uncovered a technique that allows attackers to exploit entry points across various programming ecosystems, to conduct software supply chain attacks.

Cybersecurity researchers have uncovered a technique that allows attackers to exploit entry points across various programming ecosystems, such as PyPI, npm, Ruby Gems, NuGet, Dart Pub, and Rust Crates, to conduct software supply chain attacks.
In a report from Checkmarx, researchers Yehuda Gelb and Elad Rapoport explain how attackers can manipulate these entry points to run malicious code when developers execute certain commands, posing a significant threat across open-source platforms.
The widespread use of open-source software has made it a key target for supply chain attacks. Malicious actors frequently take advantage of built-in features within open-source packages to silently distribute and execute harmful code. Two commonly exploited techniques include the use of automatic pre-install scripts that run during package installation and seemingly legitimate packages that secretly import harmful dependencies. While security tools and vigilant developers have become more adept at identifying these methods, there is another, often overlooked, feature that poses significant risks: entry points.
In this post, we’ll take a dive into Checkmarx’s research and conclusions on how attackers can potentially exploit entry points across various programming ecosystems, with a focus on PyPI, to deceive users into executing malicious code.
CLI (Command-line interface) commands are a key way for users to interact with their operating system via a text-based environment. The shell is responsible for interpreting and executing these commands, serving as the link between the user and the operating system.
When a command is entered, the shell uses a defined process to find and execute the corresponding program. To view directories in their PATH, users can type “echo $PATH” (a command which varies across different operating systems), thus displaying the search paths used by the shell to locate executables. In this context, it’s important to understand this behavior when considering how Python entry points might interact with or even conflict with existing system commands.
Entry points are a versatile feature of the packaging system that allow developers to make specific functionality accessible via a CLI command, eliminating the need for users to know the package’s internal structure or import paths.
In languages like Python, entry points enable developers to expose specific functionality as command-line tools or plugins for packages.
While this enhances modularity, Checkmarx warns that this feature can also be weaponized to distribute malicious software through methods like command-jacking and the creation of rogue plugins.
Moreover, though this approach may not immediately compromise a system as swiftly as auto-executing scripts or hidden dependencies, it allows attackers to infiltrate systems more discreetly, potentially bypassing typical security defenses.
They can be exploited by attackers to introduce and execute malicious code. To fully grasp how Python entry points might be misused by threat actors, we need to first explore how they are designed to function.
In essence, entry points serve multiple purposes such as enabling users to run command-line scripts after a package installation and defining plugin systems that allow third-party packages to extend the capabilities of a core package.
The most common type of entry point is console_scripts, which links a function to a command-line tool, making it available to anyone who installs the package.
The way entry points are specified can differ based on the type of package format being used, such as wheel or source distribution.
Wheel Files (.whl) – Wheel files are a compiled package format in which entry points are specified in the entry_points.txt file located inside the .dist-info directory. Here’s an example of what the entry_points.txt file might look like for the previous case:
 From checkmarx.com
From checkmarx.com
Source Distributions (.tar.gz) – In the case of Source distributions, in most cases entry points will nost probably be declared within the package’s setup configuration files. In traditional setups, this can include setup.py or setup.cfg.
When dealing with more developed packaging methods it can be defined in pyproject.toml. Below is an example of how entry points can be defined in setup.py:
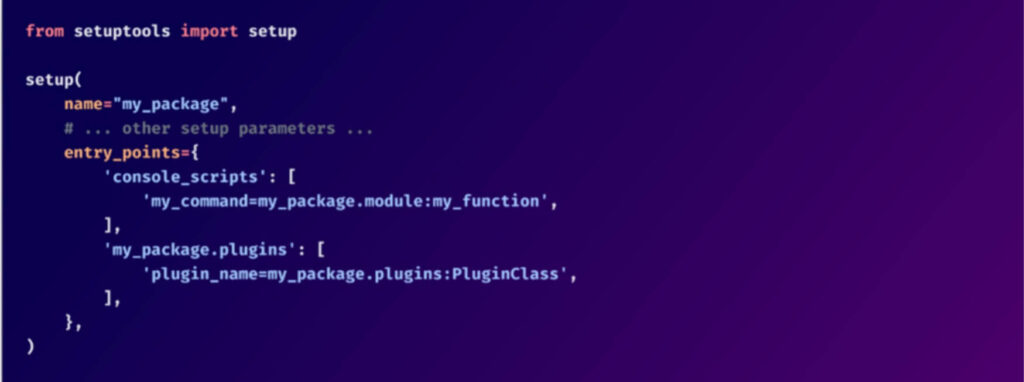 From checkmarx.com
From checkmarx.com
Shown here is how the my_command entry is a console script that gets set up during installation. After the package is installed, whenever a user types this command in the terminal, it triggers the execution of my_function from mypackage.module.
Then, these entry points are saved in the package’s metadata, which can be queried by other packages or tools to find and use the specified entry points.
An attacker with the ability to tamper with the metadata of a legitimate package or persuade a user to install a malicious one, they may be able to run arbitrary code on the user’s system whenever the specified command or plugin is called.
Attackers can take advantage of Python entry points in several ways to deceive users into executing malicious code. Researchers Gelb and Rapoport examined various techniques:
1. Command-Jacking – By faking popular Third-Party tools, entry points allow malicious packages to disguise themselves as well-known third-party utilities, targeting developers who regularly rely on these tools. A threat actor could for example create a malicious package that mimics the ‘aws’ command. Once installed, developers using AWS services who unknowingly execute this package could inadvertently trigger a command that steals their AWS credentials.
This could have serious implications in CI/CD environments, where AWS credentials are commonly used for automated deployments, potentially giving attackers access to entire cloud environments.
Similarly, a fake ‘docker’ command could target developers working with containerized applications, secretly transmitting sensitive container images or configurations to an attacker’s server. In a microservices architecture, this could expose confidential service configurations or proprietary container images.
Other widely-used third-party commands are essential in many development environments, making them prime targets for attackers aiming to maximize the damage of their malicious packages:
2. Mimicking System Commands – Threat actors can also exploit entry points by masquerading as basic system utilities. Commands like ‘touch’, ‘curl’, ‘cd’, ‘ls’, and ‘mkdir’ can be hijacked, leading to major security issues when users unknowingly run the altered commands.
This approach works best when the directory containing the malicious entry point appears higher in the PATH than the system directories, making it more likely the malicious command will be executed first. This is particularly common in development environments, where locally installed packages may be prioritized.
Globally installed malicious packages (requiring administrative privileges) could override system commands for all users, whereas packages installed by a specific user would only affect that user’s environment.
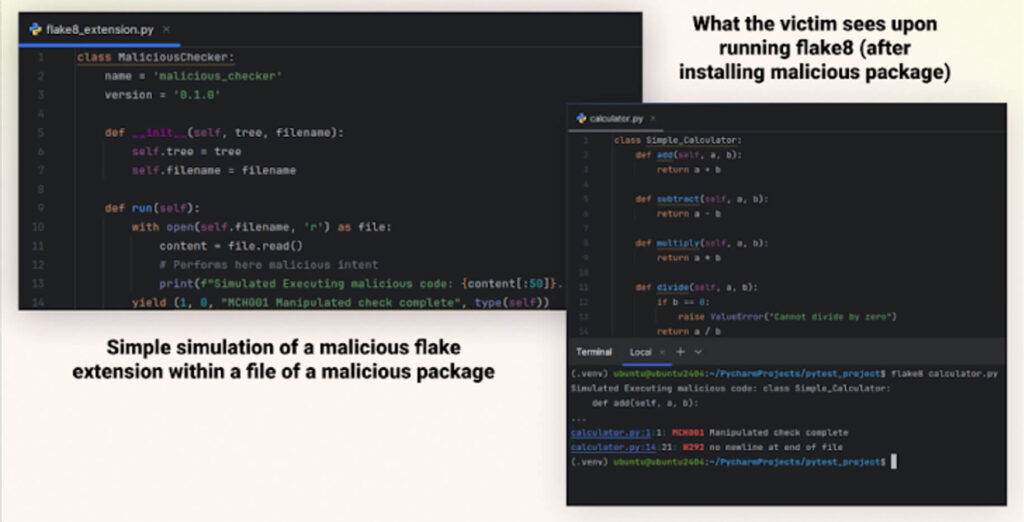
Checkmarx show in detail how an ‘ls’ command is added to the PATH /home/ubuntu/.local/bin/ls, takes priority over the PATH of the legitimate ls command by comparing the Ubuntu terminal outputs before and after installation of a specific malicious package.
Although Checkmarx research focuses mostly on Python, the misuse of entry points to introduce malicious code spans multiple programming ecosystems. Our research has uncovered this vulnerability in several key ecosystems, including npm (JavaScript), Ruby Gems, NuGet (.NET), Dart Pub, and Rust Crates, but it is not confined to these platforms alone.
 From checkmarx.com
From checkmarx.com
Entry points, which serve as a powerful tool for enabling functionality in software packages, can also be exploited to carry out attacks such as Command-Jacking, or by introducing harmful plugins and extensions in widely-used development environments.
This update follows Sonatype’s annual State of the Software Supply Chain report, which highlighted a sharp rise in malicious activity within open-source ecosystems. Since November 2023, over 512,847 malicious packages have been identified across platforms like Java, JavaScript, Python, and .NET, marking a staggering 156% increase compared to the previous year.
“Traditional security tools often fail to detect these novel attacks, leaving developers and automated build environments highly vulnerable,” the company said. “This has resulted in a new wave of next-generation supply chain attacks, which target developers directly, bypassing existing defenses.”
By recognizing this subtle attack vector, we can enhance our defenses against the ever-evolving threats in the open-source supply chain. Gaining an understanding of how entry points operate across different languages and package managers is essential for recognizing the widespread nature of this threat and devising effective defenses.
Ensuring the security of these mechanisms requires a holistic approach to prevent abuse, not just within the Python ecosystem but across the broader software supply chain. Through continuous monitoring, the Checkmarx Supply Chain Security team identifies suspicious activity and alerts users to potential threats, helping to protect developers and organizations from sophisticated attacks that exploit entry points in open-source software packages.
Each new vulnerability is a reminder of where we stand and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors: