First Officer’s log, Terrestrial date, 20220818. Officer of the Deck reporting.
A great deal of our mission happens behind the scenes. It is the very nature of a support ship, after all. And this last cycle has been no exception. Though, it seems that more of our mission has been behind the scenes this last week. Many of our duties, while hardly secret, simply go unnoticed until they come online. That includes one of our most important tasks: communication. People support our mission when they know what it is, and that is where we place much of the unseen work. And whether it’s a Facebook an Instagram hack of a beloved global brand or a vulnerability found in the depths of Microsoft Teams, we’re always here to report on it.
A first-contact scenario is probably more glorious, for sure, but our mission is eminently satisfying.
And while this has not been an extraordinary week for “Fleet Command took notice” actions, it has been a very productive week just the same.
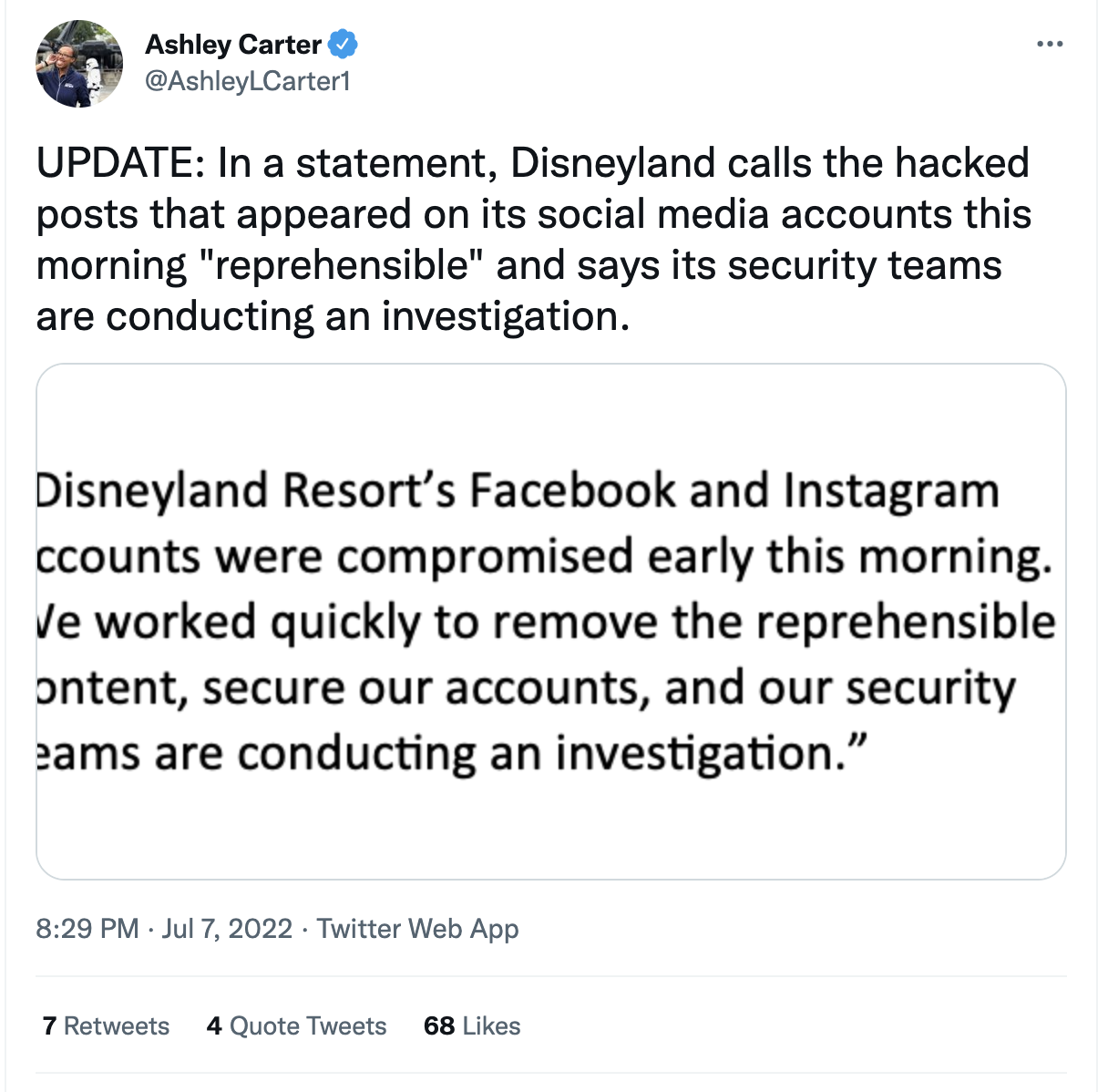
What’s old is new again? The Disneyland Facebook and Instagram hack
What happened
Recently, Disneyland had their Instagram and Facebook accounts defaced by someone claiming to be a “Super Hacker,” who posted a bit of wildly inappropriate rudeness on the sites that does not bear repeating. While details of how the attacker gained access to the accounts were not revealed, it had the feeling of an old-school website defacement rather than a sophisticated attack.
Why it matters
While we often hear about sophisticated APT groups planting malware, or spyware, or executing sophisticated ransomware attacks, the fact is Script Kiddies are still a thing. There is also the possibility that there was more to the attack than the simple defacement and this wasn’t just a script kiddie going old school. Even if it is just someone defacing Disney’s Instagram and Facebook accounts, there is still some reputational damage. With Disney’s reputation as a family-friendly outlet, anyone who went to the site and saw something seriously inappropriate as a result of this Instagram hack would be justifiably upset.
What they said
Disney is no stranger to being the subject of attention. They’re usually the ones cultivating it, though. Here’s what people are saying.
Yellow and blue make green
What happened
Yellow and Blue made Green in the old zip lock bag ads, while in the world of Cybersecurity the term would be Blue and Red make Purple. As in purple teaming.
Over the last several years, the idea of combining red and blue teams into a hybrid purple team has become more popular and has led to good results. There is a natural synergy between the team’s approaches and mindsets that can often produce better overall results than either team can get working alone.
Why it matters
Penetration testing with a red team engagement is one of the more effective ways of ensuring an organization’s security posture and systems are working as advertised. While the opposing blue and red teams often work isolated from each other, there is a lot to be gained from having them work together in real-time. It is a different kind of engagement and takes a lot of cooperation and solid communication to pull off, but the gains are real.
Of course, one of the things the article doesn’t mention is how a cyber risk management tool like Vulcan Cyber can fit neatly into the stack and make the whole purple team engagement more effective.
What they said
Naturally, improving cyber security processes is always a major subject of conversation. Here’s what Dice had to say.
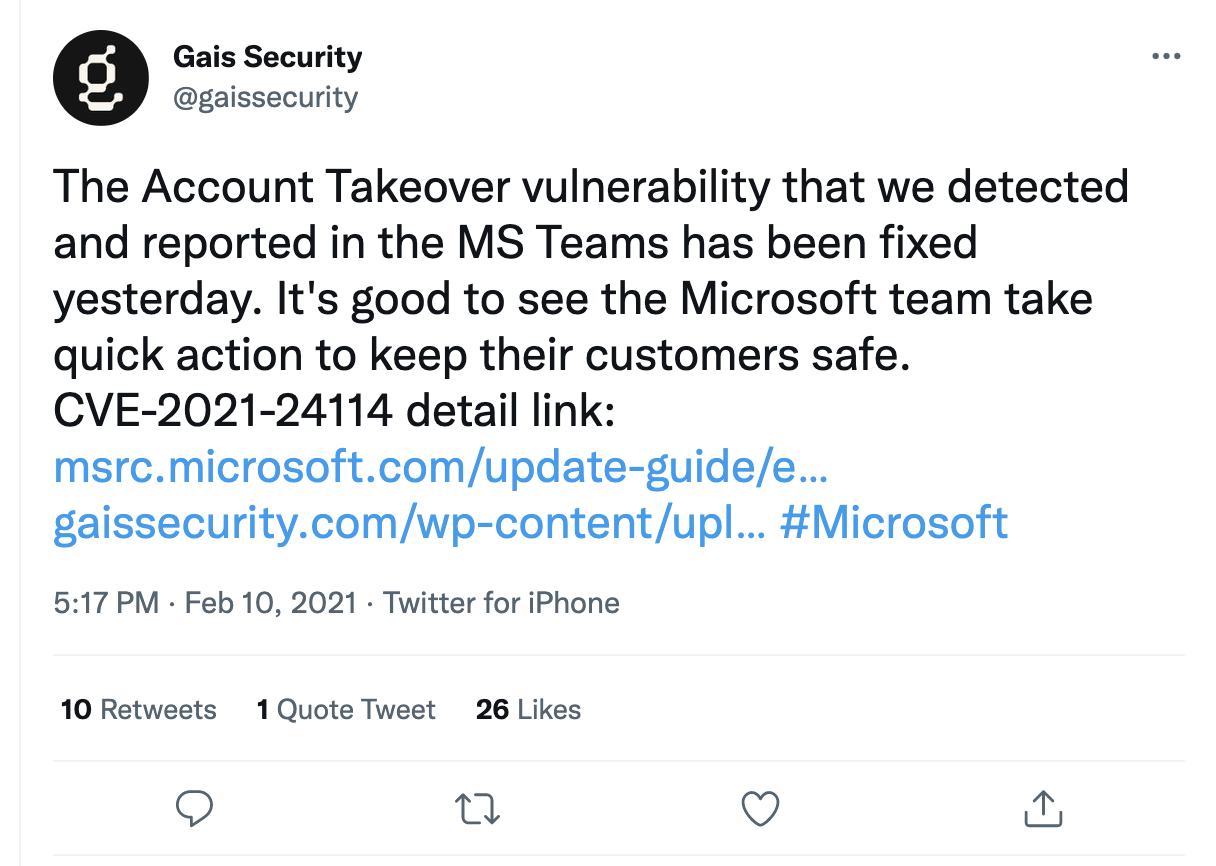
Unintended part of the team?
What happened
A security researcher posted an article on Medium going into some depth on a Cross Site Scripting (XSS) vulnerability they had discovered in Microsoft Teams. This work was a follow-up to their discovery of CVE-2021-24114 reported in early 2021. Apparently, Microsoft gave them a $6000 bounty for the find. The original post on Medium is very detailed and explores the entire route he took to finding the bug.
The only curious point is the post doesn’t include any links to Microsoft’s patch or any CVE associated with the finding. A quick search of the MITRE and Micosoft’s MSRC sites didn’t turn anything up, which is a shame because there is a lot of detail in the initial blog.
Why it matters
As web code has become more complex, it’s become more difficult to keep it clean and eradicate issues like XSS vulnerabilities. Long gone are the days when you could easily read the raw code, spot errors with an Eye-grep, and fix them in vi. While we have tools like WAF’s that can mitigate the problem, nothing’s going to be as effective as making sure the code is clean in the first place.
What they said
Vulnerabilities get people talking. And this one was no different. Read more.
Want to get ahead of the stories? Join the conversations as they happen with the Vulcan Cyber community Slack channel