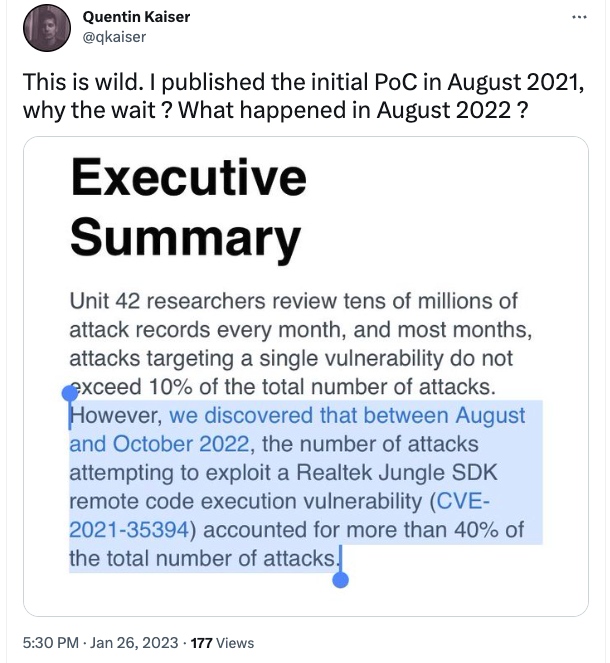
According to researchers, 40% of attacks from Aug-Oct 2022 targeted a remote code execution vulnerability, per researchers. The Realtek Jungle SDK vulnerability saw 134 million attempts and remains a threat.
Here’s everything you need to know about CVE-2021-35394 and the related vulnerabilities:
What are the vulnerabilities?
Last August, Realtek published an advisory for multiple vulnerabilities, after research conducted by the ONEKEY research team.
Realtek is a hardware company, which produces chipsets that are used by many IoT device vendors. Among these vendors, we can find familiar names such as D-Link, LG, Zyxel, etc., that use these chipsets on devices such as VoIP devices, IP cameras, and by almost all well-known IoT devices.
After researching various binaries running on RTL819xD module, four vulnerabilities were found:
- CVE-2021-35392 (‘WiFi Simple Config’ stack buffer overflow via UPnP)
- CVE-2021-35393 (‘WiFi Simple Config’ heap buffer overflow via SSDP)
- CVE-2021-35394 (MP Daemon diagnostic tool command injection)
- CVE-2021-35395 (management web interface multiple vulnerabilities
Do they affect me?
Although Realtek released the patch half a year ago, vendors often find themselves responding late to updates. This can happen because it is complex to push these updates to the end users’ products.
According to the ONEKEY research team, 65 different affected vendors and 200 unique affected devices were identified, extending the attack surface for threat actors around the globe, and making it harder to point to specific devices and secure them all.
Realtek has said that the following versions of Realtek AP-Router SDK are vulnerable:
- rtl819x-SDK-v3.2.x Series
- rtl819x-SDK-v3.4.x Series
- rtl819x-SDK-v3.4T Series
- rtl819x-SDK-v3.4T-CT Series
- rtl819x-eCos-v1.5.x Series
Has CVE-2021-35394 been actively exploited in the wild?
Heavily.
During the week the advisory was released, Junpier threat labs warned about exploitation in the wild and encouraged end users to take heed of the vendor advisory. In their blog, they presented an in the wild exploitation of CVE-2021-35394 by the same APT groups that attempted to exploit a past IoT device’s vulnerability.
Last week, Unit 42 of Palo Alto published a malware analysis report, about massive exploitation attempts of CVE-2021-35394 by many well-known malware families like Mirai, Gafgyt, and Mozi.
It is important to pay attention to the IoCs in the report, and ensure that none of your devices were compromised. In any event, it is strongly recommended to apply the appropriate patches to stay on the safe side.
Next steps
Each new vulnerability is a reminder of where we stand, and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors:
- Cyber risk in 2022- a 360° view report
- MITRE ATTACK framework – Mapping techniques to CVEs
- Exploit maturity: an introduction
- How to properly tackle zero-day threats
- Threat intelligence frameworks in 2022
And finally…
Don’t get found out by new vulnerabilities. Vulcan Cyber gives you full visibility and oversight of your threat environment and lets you prioritize, remediate and communicate your cyber risk across your entire organization. Get a demo today.