Barracuda Networks has disclosed CVE-2023-2868 – a zero-day vulnerability in its Email Security Gateway (ESG) appliances that has been exploited for the past eight months, with the earliest identified evidence of exploitation back in October 2022.
CVE-2023-2868 was identified on May 19, one day after Barracuda were alerted to suspicious traffic from ESG appliances. In response, Barracuda engaged the services of the cyber security firm Mandiant to assist with the investigation.
On August 23, 2023, the FBI confirmed that, while Barracuda’s patch can mitigate the risk for so-far unaffected appliances,
“All exploited ESG appliances, even those with patches pushed out by Barracuda, remain at risk for continued computer network compromise from suspected PRC cyber actors exploiting this vulnerability.”
Here’s everything we know about CVE-2023-2868.
What is CVE-2023-2868?
Barracuda recently discovered an incident caused by a previously unidentified vulnerability in their ESG (Email Security Gateway). ESG manages and filters all inbound and outbound email traffic to protect organizations from email-borne threats and data leaks.
The investigation into this flaw led to the detection of unauthorized access that affected a small portion of the appliances.
On May 24, Barracuda issued a warning to their customers, notifying them that their ESG appliances may have been compromised by a zero-day bug, which has since been patched. They advised customers to thoroughly examine their environments to ensure that the attackers did not move laterally to other devices on their network.
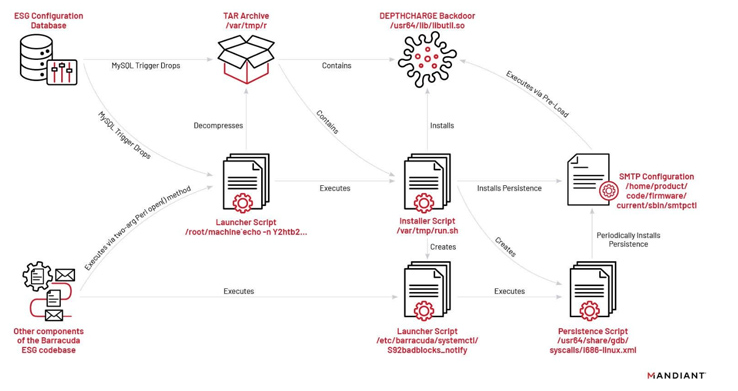
Referred to as “Saltwater,” the first malware strain discovered during the investigation is a trojanized module called the Barracuda SMTP daemon (bsmtpd). It grants attackers backdoor access to infected appliances, allowing them to execute commands, transfer files, and proxy/tunnel their malicious traffic, aiding in evading detection.
Another malware strain utilized in this campaign, known as “SeaSpy,” provides persistence and can be activated using “magic packets.” SeaSpy is designed to monitor port 25 (SMTP) traffic and shares some code similarities with the publicly available passive backdoor named “cd00r.”
Furthermore, the threat actors employed a malicious module called “SeaSide,” which targeted the bsmtpd component. It facilitated the establishment of reverse shells through SMTP HELO/EHLO commands sent via the malware’s command-and-control (C2) server.
Does CVE-2023-2868 affect me?
CVE-2023-2868 existed in a module that initially screens the attachments of incoming emails, Barracuda said in an incident report. No other Barracuda products, including its SaaS email security services, were subject to this vulnerability.
Our senior technical engineer at Vulcan Cyber, Mike Parkin, has recently said that while it’s concerning that the zero-day vulnerability in Barracuda’s ESG appliances went undetected as long as it did, it’s not entirely surprising given the nature of many security appliances.
“There are a lot of times when an appliance like the ESG is deployed and left in a ‘set it and forget it’ configuration after the initial tuning,” he said. “With automatic updates enabled, there’s often not a lot of interaction unless something goes wrong. Fortunately, Barracuda is responding appropriately now that the vulnerability has come to light. Also, compared to the number of organizations that rely entirely on cloud-based email solutions, such as Microsoft 365 and Google’s G Suite, relatively few organizations still run their own email services and rely on on-premises appliances.”
Has CVE-2023-2868 been actively exploited in the wild?
Barracuda has officially notified the public that evidence of exploitation of CVE-2023-2868 has been discovered, with indications of malware and data exfiltration found on a subset of appliances. In light of this, CISA (Cybersecurity and Infrastructure Security Agency) included the CVE-2023-2868 vulnerability on its list of known vulnerabilities that have been actively exploited. This action likely serves as a warning to federal agencies using ESG appliances, urging them to inspect their networks for signs of intrusion resulting from the compromise of these appliances.
In August 2023, Mandiant confirmed that a Chinese hacking group was observed to have exploited the vulnerability.
How to fix CVE-2023-2868
On May 20 a security patch to address the vulnerability was applied to all ESG appliances worldwide. On May 21, all appliances have received a second patch as a mitigating measure, addressing the indicators of potential compromise identified to date.
The issue was fixed as part of BNSF-36456 patch and was automatically applied to all customer appliances.
Barracuda said that users whose appliances were believed to be impacted have been notified via the ESG user interface about the actions they need to take, also mentioning it has reached out to these specific customers.
Customers are advised to perform the following actions:
- Check if their ESG appliances are up-to-date by ensuring they have received the necessary security patches.
- Cease using any appliances that were compromised and request a new virtual or hardware appliance from Barracuda.
- Rotate all credentials associated with the compromised appliances to prevent unauthorized access.
- Review network logs for any indicators of compromise (IOCs) shared by Barracuda and be vigilant for connections from unknown IP addresses.
By following these steps, customers can take appropriate measures to address and mitigate the impact of CVE-2023-2868 on their ESG appliances.
Next steps
Each new vulnerability is a reminder of where we stand, and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors:
- Can you trust ChatGPT’s package recommendations?
- MITRE ATTACK framework – Mapping techniques to CVEs
- Exploit maturity: an introduction
- OWASP Top 10 vulnerabilities 2022: what we learned
- How to fix CVE-2023-32784 in KeePass password manager
And finally…
Don’t get found out by new vulnerabilities. Vulcan Cyber gives you full visibility and oversight of your threat environment and lets you prioritize, remediate and communicate your cyber risk across your entire organization. Get a demo today.









