-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
Cyber risk quantification has emerged as a vital way for organizations to measure risk. Here's everything you need to know.
Cyber risk quantification (CRQ) has been gaining traction as a strategy for uncovering vulnerabilities hidden across your system. It helps organizations evaluate possible threat scenarios and calculate their financial implications. Quantifying risks allows organizations to get real about the monetary losses they could bear in case of an attack.
Cyber risk quantification is about assessing your organization’s risk exposure and estimating the financial loss caused by a security attack.
By quantifying the responsibility of each stakeholder in financial terms, cyber risk quantification sends out a clear message that the onus of avoiding cyber risks is on everyone.
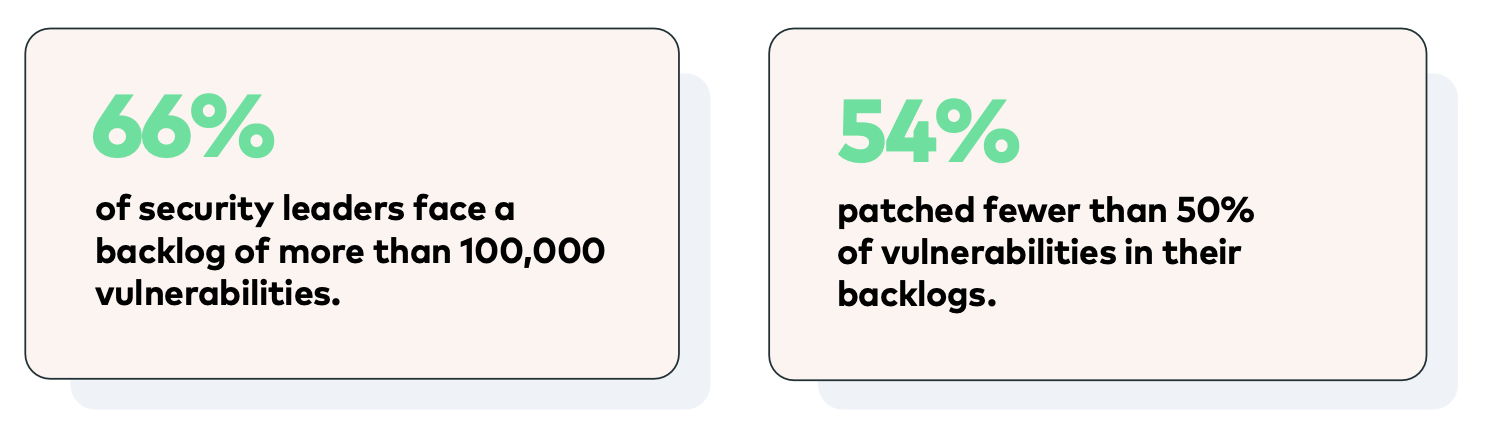
Cyber risk quantification involves applying advanced modeling techniques to assess the more hidden risks, the likelihood of them being exposed, and how to cope with the disruption.
This information is then used to calculate financial risk to come up with an estimated loss. By building an effective model to score and prioritize risks, you can refine your risk management approach to strengthen your security both as a good practice and as a tactic to manage breaches quickly.
It helps organizations clarify which security leaks to plug first, which controls must be secured tightly, and which investments to make for better cyber security.
Cyber risk quantification gives a tangible and monetary measure of cyber security readiness, allowing decision-makers and executives to articulate risks in business-relevant language. Additionally, they can plan better cyber security investments and resource allocation to reduce risks.
Cyber risk quantification brings all the business stakeholders and the security team on the same page concerning the risk canvas. In this way, necessary security investments can be made without delays or the need to convince decision-makers later.
Before initiating the quantification of cyber risk, you must choose a framework that will allow you to conduct a proper risk analysis. There are several models to achieve this, including:
Cyber risk quantification has a number of applications besides the security of your applications, including:
Internally within an organization many roles benefit from cyber risk quantification:
Chief risk officers (CROs) are tasked with improving security through efficient risk management. This includes monitoring and identifying risks proactively. Cyber risk quantification empowers CROs in tracking and prioritizing IT risks allowing you to plan remediation strategically.
Chief information and security officers (CISOs) are accountable for protecting the organization’s IT infrastructure, information, and systems from cyberattacks. The quantification of cyber risk allows them to threat-proof their ecosystem. It gives them insights to uncover vulnerabilities and mitigate them before they can be used to weaken the cyber security posture of the organization.
Given the financial repercussions of cyber threats, the involvement of the chief financial officer (CFO) becomes essential.
Although cyber risk quantification is a fairly new concept in cyber security, CFOs have been conducting financial risk analysis—albeit for products and services—for many decades now.
The financial heads of organizations must work closely with the CRO and CISO in allocating resources for risk management.
By calculating the financial effects of risks, you can fast-track investments, planning, and tracking. Since cyber risk quantification gives you a ballpark estimated loss, it becomes an important security metric. However, it needs to be calculated properly.
Quantifying cyber risk is about gauging breach risk for every asset and vulnerability. It can be done using the below formula:
Breach risk = Breach likelihood x breach impact
Here, “breach risk” has a dollar value ($), “breach likelihood” is the probability of an attack evaluated in percentage (%), and “breach impact” is monetary loss calculated in dollar value ($).
When calculating breach risk, five factors are essential:
See how Vulcan Cyber helps you calculate your breach risk >>
Organizations typically use several tools and platforms to generate and capture data, which is then distributed across teams. Most of the time, these solutions are not interoperable, which creates data silos.
Going through each tool and analyzing the data is time-consuming and labor-intensive. If any platform is overlooked, it will create an incomplete picture of your security posture.
With data, assets, and resources spread across the organization, it will limit the capability of your security team to assess cyber risk properly.
Your quantification will lack data points like the type of threat, severity of the vulnerability, and the effectiveness of security tools.
Bad actors are looking for any vulnerability or security gap to be able to break into your system. This makes cyber security a constant and continuous process.
However, your security strategy will be crippled if your team lacks real-time visibility into key security data. Since threats crop up consistently at a rapid rate, your risk management team must be able to tackle them in real time.
If the security team has restricted access to siloed data, they will fail to identify threats and implement remediation practices properly.
One of the first tasks in assessing your risk landscape is understanding the origin of cyber threats.
This includes internal and external sources like employees, vendors, and third-party entities. Once you build potential risk profiles, you can easily identify security risks like documented CVEs and the probability of attacks.
Sometimes, we use the same term to define two types of cyber threats, such as calling both ransomware and actors executing ransomware as cyber threats. In cyber risk quantification, only ransomware is a threat, as it can have financial repercussions.
Your security team must standardize the nomenclature for all the relevant risk terms to ensure more streamlined communication among stakeholders.
Every asset, both internal and external, that you are associated with must be assigned a critical rating using quantification models like FAIR and DREAD. The rating will represent the potential threat and impact it may have.
This information will help you identify assets that must be included when calculating cyber risk quantification. Besides reducing your time in data processing for quantification, it will also show how your vulnerabilities are distributed.
Make note of everything you are doing and the rationale behind it. Having your risk assessment strategy and practices documented will leave a record of your decision-making pattern and act as supporting evidence.
This will also help you build a strong case to demonstrate your cyber security and risk management exercises. Additionally, these records will work as guidelines for your team in the future.
When initiating a remediation strategy to plug the security gaps, teams may attempt to cover a lot of ground as quickly as possible. This is not only impractical but leads to ineffective remedies.
Instead of covering all cyber threats simultaneously, prioritize the risks based on severity and damage potential. You can add them to a priority list that includes a security rating, or use risk analysis techniques like cyber risk quantification.
Given the damage cyber attacks can do to an organization’s reputation, all stakeholders must be aware of cyber security performance.
Regular updates on risk impact projections should be shared with the teams to give them a fair idea of the organization’s risk management plans.
Efficient cyber risk quantification is necessary to run the right risk management strategy. But it’s just one part of the larger cyber security canvas.
Managing and minimizing vulnerabilities to improve security posture requires efforts from the entire organization, with the security team leading from the front.
Own and mitigate risk across your entire attack surface with a unified solution. Get a demo of the Vulcan Cyber® ExposureOS today.