All aspects of the financial services industry—from banking to securities, and from insurance to pensions—are highly regulated at multiple levels. These regulations have two primary objectives: to protect customers from fraudulent or negligent behavior, and to safeguard transactions and data.
One regulation created specifically for the financial sector is the Dodd-Frank Wall Street Reform and Consumer Protection Act of 2010. It was enacted in response to the market failures that underlay the financial crisis of 2008. In addition to financial system reforms called for by the act, Dodd-Frank specifically outlines cyber security compliance requirements intended to ensure data security, effective change management, and application integrity.
In addition, non-sectoral data privacy laws such as the European Union’s General Data Protection Regulation (GDPR), single out the finance vertical for the highest levels of data privacy controls, including rigorous vulnerability management.
This blog post outlines how Vulcan Cyber®, a vulnerability remediation orchestration platform, can help finance companies stay compliant with these and other regulatory frameworks.
Start With Risk-Based Prioritization
Enterprises in all sectors, including finance, deploy a variety of vulnerability scanners across their complex digital environments, each generating outputs at scale. With different scanners working within different time frames and urgency frameworks, centralized security teams are often challenged to achieve clear risk-based vulnerability prioritization across organizations.
The Vulcan Cyber risk-based prioritization approach addresses this challenge by normalizing and analyzing vulnerability scanner outputs within the context of an organization’s specific ecosystem. To help finance companies identify the vulnerabilities that are most critical to their business, Vulcan Cyber cross-references external vulnerability and threat information with data from internal systems, such as asset management and change management.
Vulcan Cyber contextualizes risk in the environment, allowing security teams and their allies (operations, development, lines of business, etc.) to think in terms of vulnerability instances, i.e., the number of assets throughout the organization that are potentially impacted by a given vulnerability. This approach quickly pinpoints truly high-risk vulnerabilities that have the greatest impact on the organization’s security posture.
The Vulcan platform vulnerabilities dashboard, as shown in the screenshot below, provides a total risk score for the company [1] and a filterable [2] view of existing vulnerabilities categorized by criticality [3]. For each vulnerability, the dashboard displays its risk score (specific to the business), the external sources in which it is described, when it was discovered, its status, how many and which type of assets it affects, whether it breaches SLA(s) (see Working Together to Meet SLAs below), and the type of threat it poses.
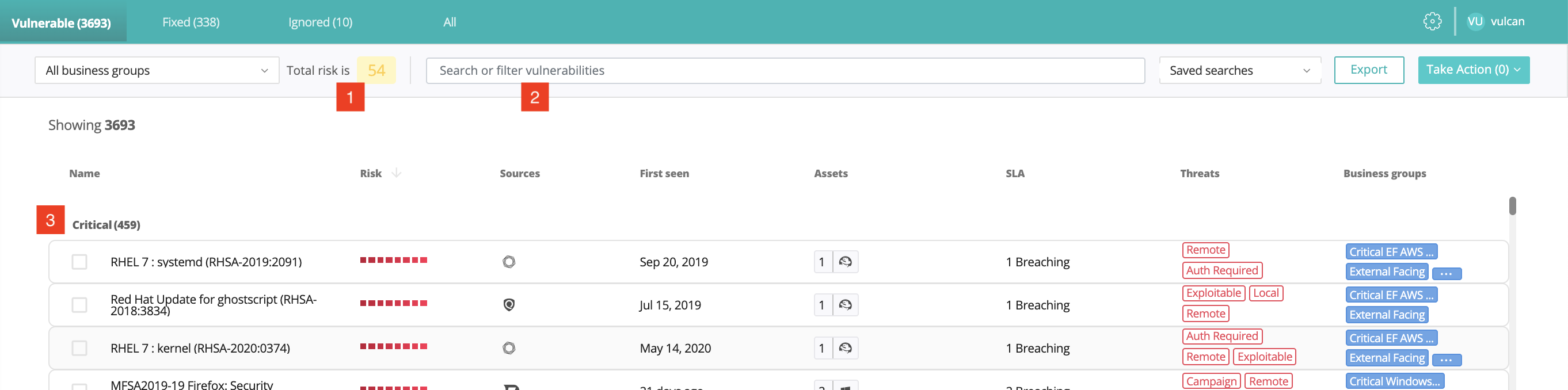
A section of the Vulcan platform Vulnerabilities Dashboard
Vulcan also provides visibility into vulnerabilities that were excluded and explains why they were excluded. This allows for effective management of vulnerability exceptions and can be useful for audits as well.
Working Together to Meet SLAs
Vulnerability remediation is an inherently cross-functional process. Security teams identify and prioritize vulnerabilities while operations, development, and line-of-business teams carry out actual remediation measures—from configuration changes and compensating controls to testing and deploying patches. It is important, therefore, that financial services companies establish clear internal SLAs for vulnerability remediation workflows. They need to determine who does what, in which sequence, and within what time frame.
Vulcan Cyber allows finserv companies to customize these SLAs according to risk-based vulnerability criticality while also providing a collaborative platform within which teams can work together to meet the SLAs. As shown in the screenshot below, Vulcan Cyber provides all remediation stakeholders with a single source of truth for SLA compliance.
In addition to the total unique vulnerabilities currently breaching SLA, the report clearly shows what percentage of vulnerability instances (i.e., unique vulnerabilities multiplied by the number of assets affected) are in breach. The vulnerability instances are then broken down by risk category. For each category, it is made clear what percentage of all vulnerability instances in that risk category are in breach, how many unique assets are affected, and what the longest breach duration in that category is.
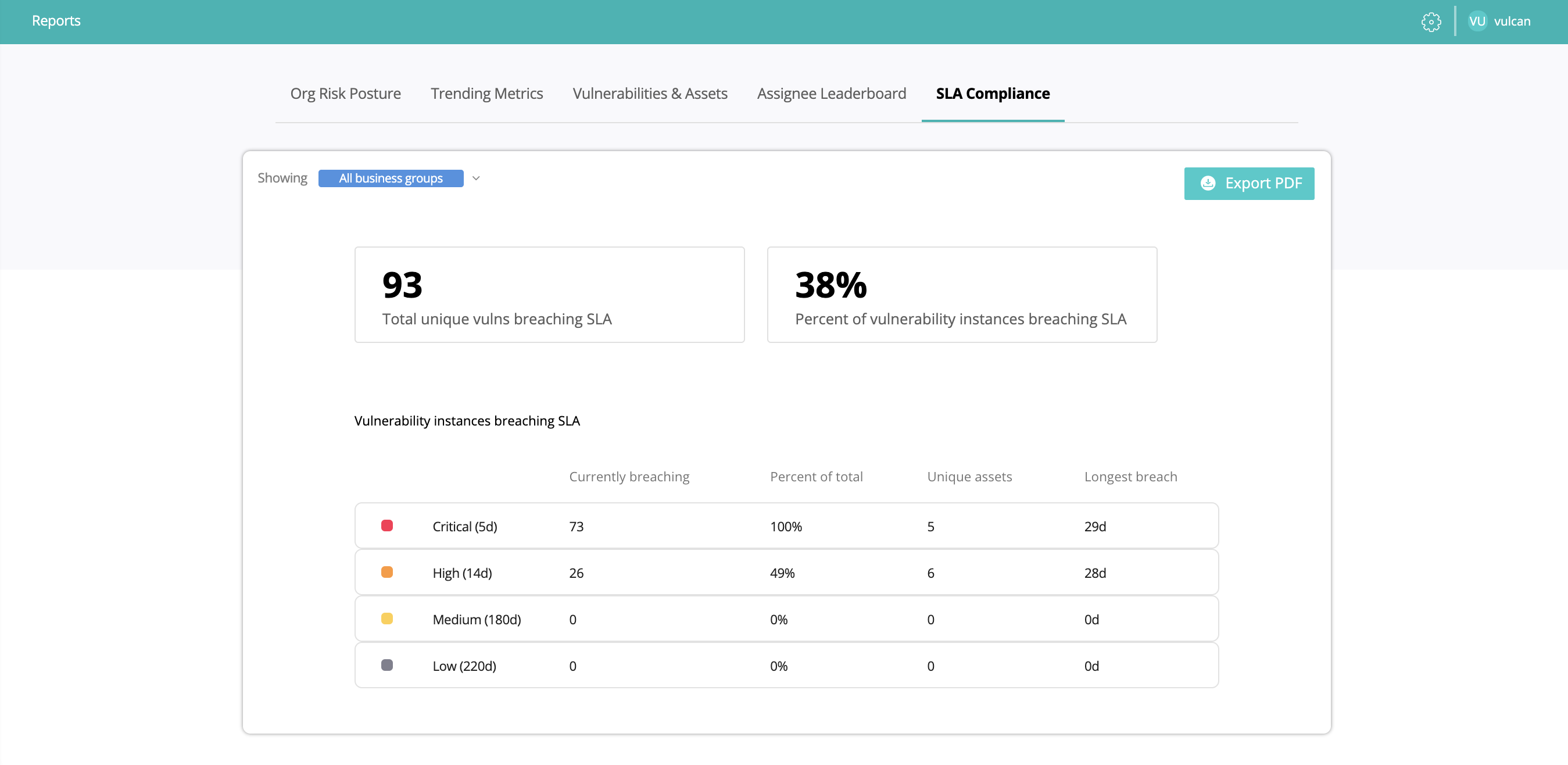
A section of the Vulcan platform SLA Compliance Report
This business-data-driven approach to monitoring SLA compliance is important when working to keep a financial services company’s remediation program on track and aligned with compliance metrics.
Enhanced Vulnerability Scan Coverage
By integrating with vulnerability assessment and penetration test tools, CMDBs, and cloud inventories Vulcan provides clear visibility into all assets in the environment and highlights those that are being scanned ineffectively or not at all.
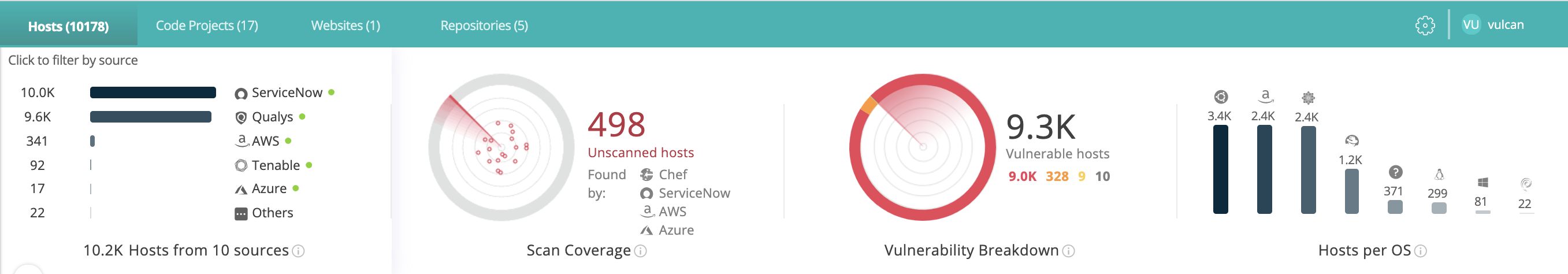
The Vulcan platform assets monitoring interface showing how many hosts have been discovered across the environment, how many of those are currently unscanned, and breaking down the vulnerabilities found
Automated Alerts and Playbooks
Vulcan Cyber delivers automated and actionable alerts to reduce the time to detecting and remediating vulnerabilities, ensuring financial services companies can meet their required breach notification and remediation SLAs and time frames.
Teams can also create remediation playbooks that are triggered by alerts, such as the detection of a high-severity vulnerability or the breach of a vulnerability remediation SLA. These automated procedures reduce manual work and mundane tasks while providing consistent, error-free remediation workflows. The Vulcan platform also facilitates information sharing across entire teams.
The screenshot below shows how easy it is to define an alert for critical vulnerabilities [2] on external facing [4] AWS [1] hosts [3], with the ability to add conditions [5] that make the alert even more granular.
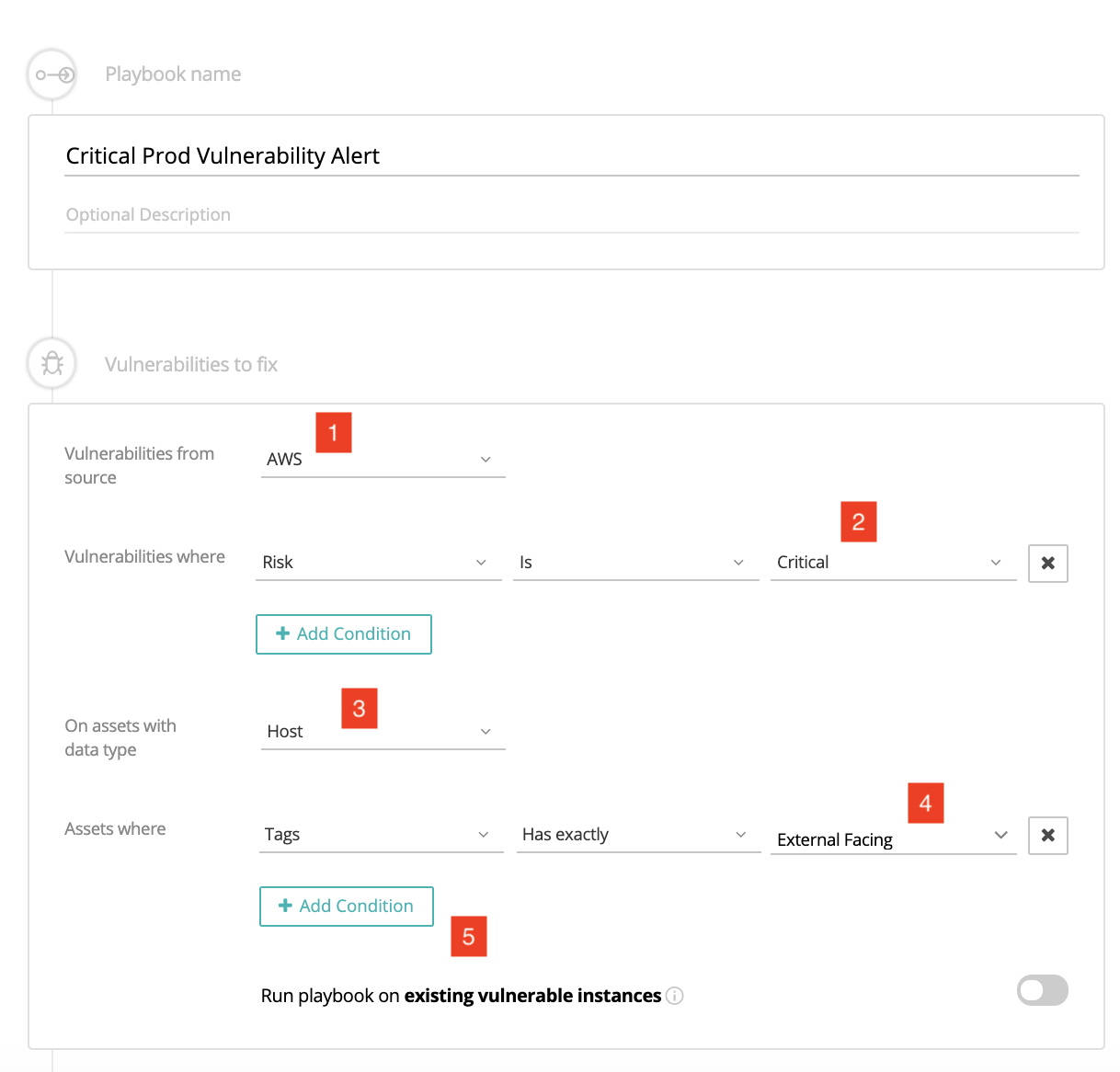
A section of the alert definition interface in the Vulcan platform Playbook Editor
The next screenshot shows the two categories of actions triggered by the alert:
- Remediation actions [6] such as opening a service ticket on an IT service management platform (e.g. Jira, ServiceNow), assigning the vulnerability via email or posting it on Slack, and generating remediation scripts for all relevant platforms (e.g. Chef, Ansible).
- SLA breach actions [7] such as assigning the breach alert to the relevant team member(s) via email.
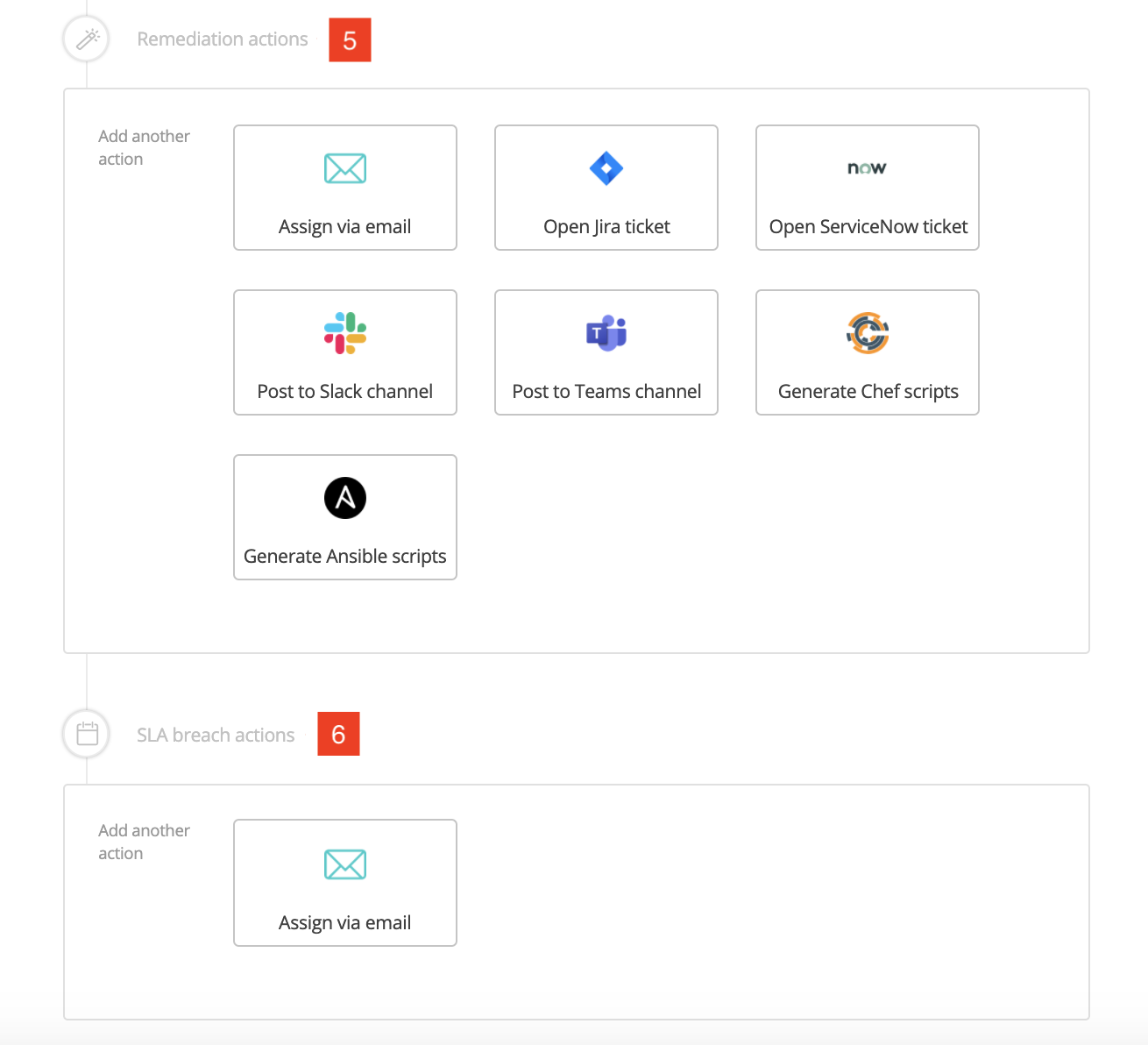
A section of the remediation and SLA breach actions interface in the Vulcan platform Playbook Editor
Automated Reporting
Regulatory auditors expect financial services companies to be able to demonstrate vulnerability detection and response capabilities. Vulnerability management reporting is often a manual, tedious, and time-consuming task. Vulcan Cyber comprehensive and automated reports, such as the vulnerabilities & assets report shown in the screenshot below, fully meet regulatory audit requirements while allowing security and IT operations teams to focus on vulnerability remediation rather than reporting.
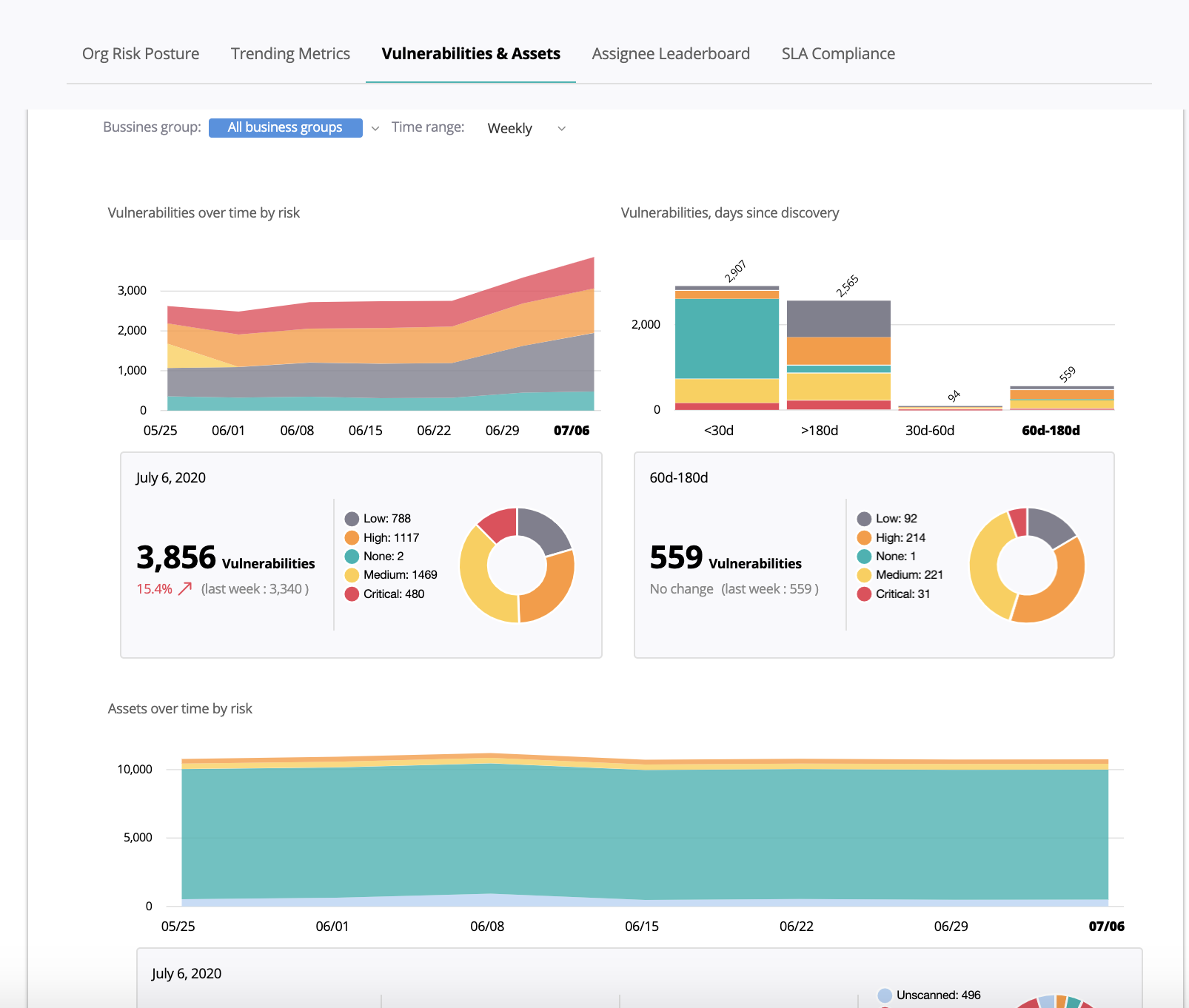
A clear view of vulnerabilities and vulnerability instances over time, categorized by risk. The bottom section shows the SLA status of the highest risk vulnerabilities currently under remediation.
Centralized Security Posture Management
The Vulcan platform provides easy-to-use dashboards that anyone in the company (including executives and line-of-business managers) can use to understand the current status of its security posture without the need for advanced cybersecurity or compliance expertise.
The boardroom dashboard in shown below clearly provide the C-suite with:
- The company’s overall risk score [1]
- Total assets [2] and scan coverage [3]
- Risk distribution across the environment [4]
- An asset matrix based on technical complexity versus business impact [5]
- Vulnerability instances and risk profile over time [6]
- Risk breakdown by criticality [7]
- Remediation KPIs such as velocity [8] and throughput [9]
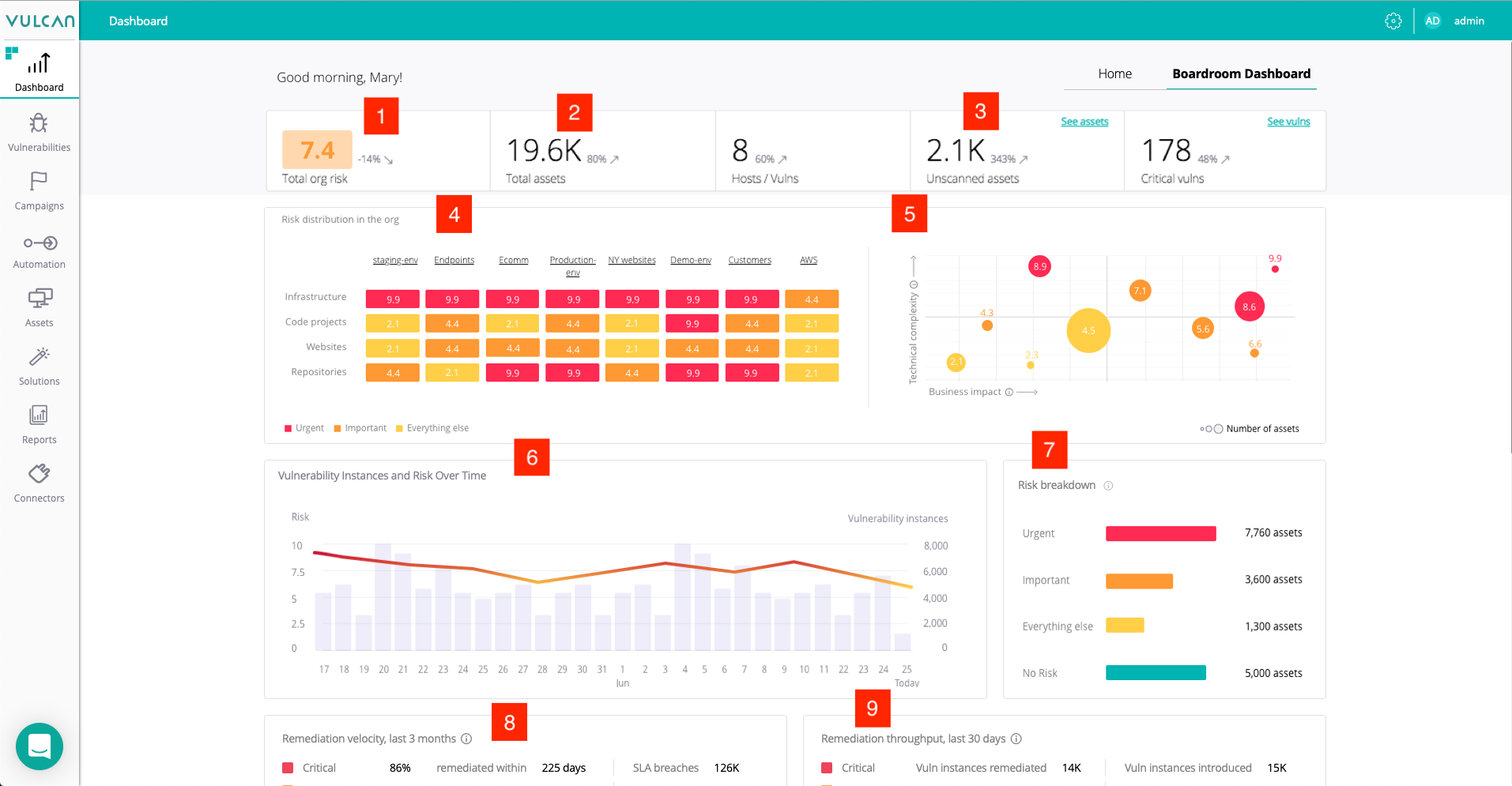
The Vulcan Cyber Boardroom Dashboard
Conclusion
Regulatory frameworks established for the financial services industry set clear security risk management guidelines, covering issues like risk monitoring and identification, analysis and measurement, management, reporting, and more. Financial institutions are expected to map their business functions, roles, and processes in terms of their criticality so that they can apply risk-appropriate mitigation measures and SLAs for vulnerability scanning and remediation—all in compliance with external and internal requirements.
With Vulcan, financial organizations can quickly identify the business-critical vulnerabilities that undermine their security posture. They can meet their time-to-remediation SLAs through streamlined, automated, and collaborative remediation workflows. Sophisticated visualizations give compliance officers a real-time view of the organization’s vulnerability risk score and the progress of its remediation activities. For regulatory reporting and auditing purposes, all vulnerability remediation actions are logged and retained over time, while compliance reports can be generated at the click of a button.
The Vulcan Cyber vulnerability remediation orchestration platform provides risk-aligned intelligence to help businesses meet regulatory compliance requirements. This isn’t easy in any industry, but the challenge is particularly acute in the extremely regulated financial services industry. Considering the stakes, with valuable customer data, trillions of dollars in assets, and a reputation that means everything in an industry built on trust, Vulcan Cyber is designed to make the work of vulnerability remediation efficient and effective.
Request a demo to see how Vulcan Cyber can support your company’s vulnerability remediation requirements and SLAs.









