First Officer’s log, Terrestrial date, 202200706. Officer of the Deck reporting. The pace of recent activity has diminished very slightly, but we expect that it is just part of the natural ebb and flow of hostile activity in our sector. In spite of the brief lull, the crew remains vigilant.
Our next log entry may be delayed, as the ship will be docked at a ground facility in San Francisco, Northern Hemisphere, Earth, Sol system, for a conference. Interested parties are encouraged to visit our temporary ground station if they are in the region. I will be delivering live updates during the engagement through the planetary “Twitter” network using the communications handle @mike_at_vulcan.
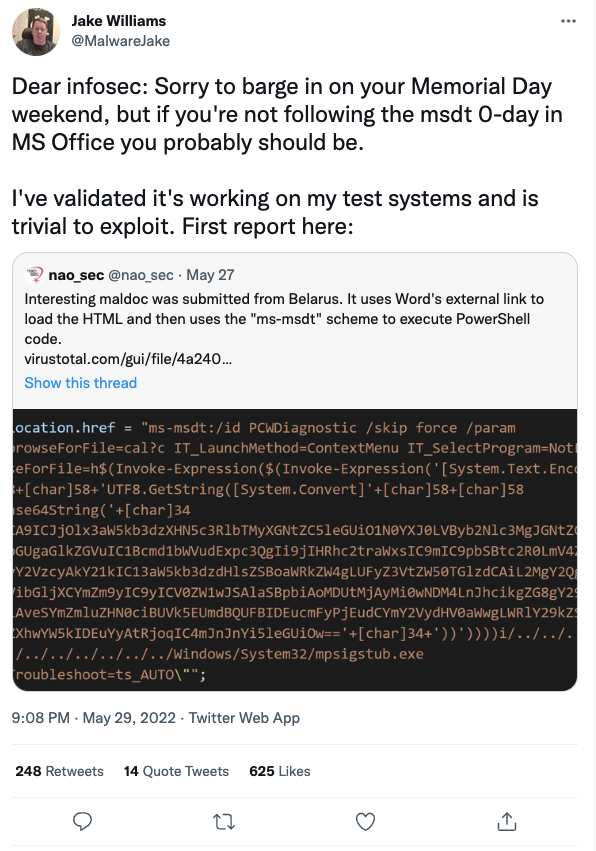
And then they found a new way to abuse Office – a new Microsoft zero day vulnerability
What happened
Threat actors have discovered another attack vector using Microsoft Office documents, leveraging the Microsoft Support Diagnostic Tool (MSDT) mechanism to exploit the latest Microsoft zero day vulnerability Follina. This is functionally similar to the hundreds of MS Office Macro vulnerabilities we have seen.
Why it matters
Attackers are always looking for new and unusual ways to leverage existing functionality in unintended ways to further their agenda. With MS Office, the tools that enable extraordinary flexibility and functionality are a prime candidate for abuse. That’s what we are seeing here. Until Microsoft releases a patch, it’s possible to disable the MSDT functionality which will thwart this attack.
What they said
People had a Word or two about the latest Microsoft zero day vulnerability.
What could possibly go wrong?
What happened
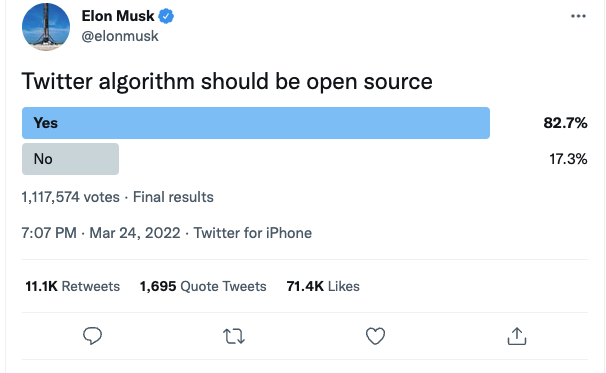
As part of his plan to purchase Twitter, Elon Musk said he would open the algorithms the platform uses to generate its recommendations. Whether the deal is eventually finalized or not is secondary to the idea of opening up an important part of Twitter’s internal structure.
Why it matters
Providing visibility into the inner workings of Twitter’s recommendation algorithms is a two-edged sword. While increasing transparency is laudable, and could shut down claims of bias, it would also open the door to careful manipulation by parties interested in furthering a specific agenda. Knowing how the algorithms work could invite people to try and game the system.
In the bigger picture, this applies to any social media recommendation algorithm.
What they said
As ever with Elon Musk, people had plenty to say.
What’s old is new again.
What happened
Threat actors dropping the ChromeLoader malware have found a new attack vector to get the payload on their targets. Or old attack vector, depending on your perspective. Using .ISO files described as cracked or otherwise unofficial versions of games or other applications, they coax a target to download the .ISO and run it on their system. The ISO may actually have the cracked software the victim wants, but it also leverages PowerShell and drops the malware on their system.
Why it matters
We don’t need to remind you that downloading cracked software is generally a bad idea, right? Good. Sketchy downloads have been an attack vector for decades. Literally, decades. Some of the earliest “malware” attacks appeared in the 80s on dialup BBSs with files that promised to be games but were really .bat files that would delete your C: drive. It has not gotten better. The fact that threat actors are still finding success with this attack vector speaks to our user communities not learning the lesson.
What they said
Enough to make sure this story doesn’t fall through the cracks. Read more.
Want to get ahead of the stories? Join the conversations as they happen with the Vulcan Cyber community Slack channel.