-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
McAfee researchers have identified the exploitation of GitHub comments to spread malware. Here's the breakdown.

Cyber criminals are exploiting GitHub comments to distribute malware under the guise of Microsoft software downloads, deceiving users into unwittingly downloading malicious software.
The vulnerability in GitHub, potentially stemming from a design choice, is being exploited by malicious actors to disseminate malware through URLs linked to Microsoft repositories, thereby lending an air of credibility to the files.
This blog explores the methodology and mitigation steps for this vulnerability.
Cyber security researchers at McAfee have uncovered a malicious scheme exploiting GitHub’s comment section, wherein threat actors host malware and camouflage download links as authentic Microsoft repositories, making the files appear trustworthy.
Although most malware incidents have centered on URLs associated with Microsoft on GitHub, this flaw could be leveraged with any public repository on the platform, enabling threat actors to craft highly convincing bait.
Earlier this week, McAfee issued a report regarding a recently discovered LUA malware loader disseminated via what initially seemed to be authentic Microsoft GitHub repositories.
These repositories were associated with the “C++ Library Manager for Windows, Linux, and MacOS,” commonly referred to as vcpkg, and the STL library.
McAfee reports that since February 2024, hackers have been exploiting GitHub’s file upload mechanism to host and disseminate malware via automatically generated download links, incorporating the repository owner’s name and ownership details.
These repositories harbor malware designed to pilfer passwords, masquerading as seemingly benign files.
What’s more concerning is that the repositories also feature comments containing download links meticulously crafted to mimic official Microsoft software repository URLs.
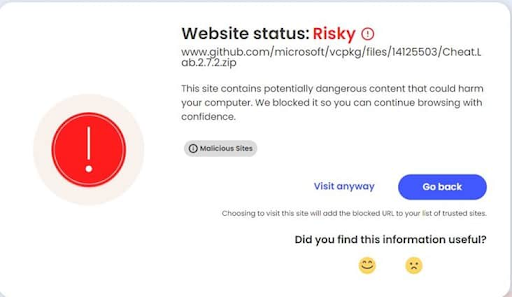
GitHub’s comment function stores files on its servers, generating instant access links to them. This deceptive tactic can mislead unsuspecting users into believing they are clicking on a link from a trusted developer.
Moreover, users need not submit comments or bug reports since the file is already uploaded and accessible.
This deceptive tactic leverages the trusted nature of both GitHub and Microsoft. Users visiting these repositories might be tricked into downloading malware, believing they are getting legitimate Microsoft software.
The potential repercussions are severe, as the downloaded malware could facilitate the theft of user credentials, compromise systems, pilfer browsing data and cryptocurrency funds, or even instigate additional cyberattacks.
According to Bleeping Computer, GitHub has removed the malware associated with Microsoft’s repositories but nevertheless, the malware associated with httprouter and Aimmy are still accessible.
The below URLs, provided for the malware installers, unmistakably suggest their association with the Microsoft repository. However, upon inspection, no references to these files were found within the project’s source code.
https://github[.]com/microsoft/vcpkg/files/14125503/Cheat.Lab.2.7.2.zip
https://github[.]com/microsoft/STL/files/14432565/Cheater.Pro.1.6.0.zip
Given the unexpected nature of Microsoft repositories distributing malware since February, a further investigation discovered that these files did not originate from vcpkg; instead, they were uploaded as part of a comment appended to a commit or issue within the project.
When leaving a comment on GitHub, users have the option to attach various file types (archives, documents, etc.), which are then uploaded to GitHub’s CDN and linked to the relevant project through a unique URL format, as follows: ‘https://www.github.com/{project_user}/{repo_name}/files/{file_id}/{file_name}.’
For multimedia content like videos and images, the files are stored under the /assets/ path.
Rather than generating the URL upon posting a comment, GitHub automatically creates the download link once a file is added to an unsaved comment, as illustrated below.
This functionality enables threat actors to append their malware to any repository without raising suspicion.
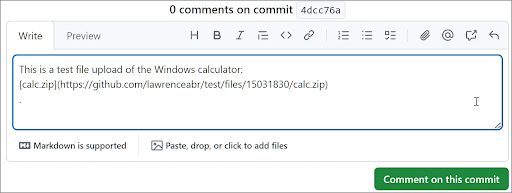
Even if you opt not to post the comment or delete it subsequently, the files remain unaffected on GitHub’s CDN, and the download URLs persist indefinitely.
Since the file’s URL includes the repository name where the comment originated, coupled with the widespread usage of GitHub across various software companies, this loophole enables threat actors to devise highly convincing and credible traps.
For instance, a threat actor could upload a malware executable within NVIDIA’s driver installer repository, posing as a new driver purportedly resolving issues in a popular game.
Alternatively, they could attach a file in a comment on the Google Chromium source code, feigning it as a new test version of the web browser.
Such URLs would seemingly belong to the respective company’s repositories, lending them an aura of trustworthiness.
Regrettably, even if a company becomes aware that its repositories are being exploited for malware distribution, no settings are available to manage files attached to their projects.
Moreover, the only recourse to safeguard a GitHub account from such abuse and safeguard its reputation is by disabling comments.
According to GitHub’s support documentation, comment disabling can only be done temporarily, for a maximum period of six months at a time. However, restricting comments in this manner can significantly impede a project’s development, as it hampers users’ ability to report bugs or offer suggestions.
Sergei Frankoff, from the automated malware analysis service UNPACME, conducted a live stream on Twitch just last month, where he highlighted the active exploitation of this vulnerability by threat actors.
Apart from httprouter, which was exploited for malware distribution in a similar fashion (evident in the ‘Cheater.Pro.1.6.0.zip’ file found in Microsoft’s URLs), Frankoff also mentioned another campaign discovered in March.
This campaign utilized the same LUA loader malware, known as SmartLoader, disguised as the Aimmy cheat software. SmartLoader is frequently deployed alongside other payloads, such as the RedLine information-stealing malware.
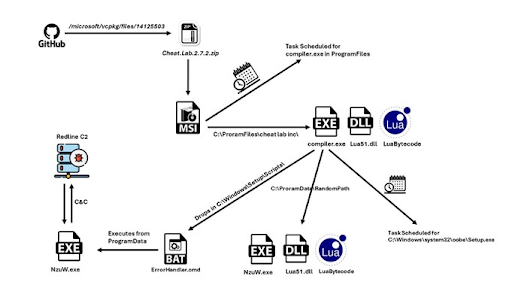
|
Cheat.Lab.2.7.2.zip |
5e37b3289054d5e774c02a6ec4915a60156d715f3a02aaceb7256cc3ebdc6610 |
|
Cheat.Lab.2.7.2.zip |
https[:]//github[.]com/microsoft/vcpkg/files/14125503/Cheat.Lab.2.7.2.zip
|
|
lua51.dll |
873aa2e88dbc2efa089e6efd1c8a5370e04c9f5749d7631f2912bcb640439997 |
|
readme.txt |
751f97824cd211ae710655e60a26885cd79974f0f0a5e4e582e3b635492b4cad |
|
compiler.exe |
dfbf23697cfd9d35f263af7a455351480920a95bfc642f3254ee8452ce20655a |
|
Redline C2 |
213[.]248[.]43[.]58 |
|
Trojanised Git Repo |
hxxps://github.com/microsoft/STL/files/14432565/Cheater.Pro.1.6.0.zip |
Even after comments are posted or removed, GitHub’s CDN files remain unaltered, and the associated download URLs persist.
This loophole enables threat actors to devise sophisticated traps, particularly since many software companies utilize GitHub, and the file URLs contain the repository name.
Regrettably, the sole available recourse is to disable comments. However, this solution presents further complications, as legitimate users frequently utilize comments to report bugs or provide valuable suggestions, and comments can only be disabled for a maximum of six months.
To safeguard oneself, it’s advisable to download software directly from the developer’s official website, refrain from clicking links in comments or on third-party sites, verify file hashes, and employ robust security software with real-time malware detection.
When uncertain about a download link, it’s prudent to visit the official Microsoft website to ensure system safety.
Max Gannon, Cyber Intelligence Team Manager at Cofense, remarked on this issue, stating, “This tactic is remarkably cunning for threat actors to exploit, especially considering GitHub has offered no means for companies to mitigate the risk.
The best course of action is for individuals to exercise caution when clicking any link, regardless of its apparent destination or sender… For instance, upon reflection, it’s improbable for a .zip file containing cheat software to be directly hosted on a Microsoft repository.” Max elaborated.
Each new vulnerability is a reminder of where we stand and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors: