-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
As the market evolves, so do we. Learn about our strategic shift to match the needs of enterprise security teams today.
Our shift to exposure risk management was inevitable.
Vulcan Cyber started in a world where customers used one or two scanners for largely on-premise infrastructures. The challenges they faced were mainly focused on the operational side of things, with data issues not yet presenting a major hurdle.
But even back then, as we were developing the initial concepts of “remediation operations,” or RemOps as it’s known today, we recognized that data would emerge as a significant challenge, hindering effective risk management and remediation.
Traditional vulnerability management may have been well-suited for traditional environments. But, for our customers, those environments are long gone, replaced by a mutating threat landscape across cloud, SaaS, IoT, AI, and other emerging technologies.
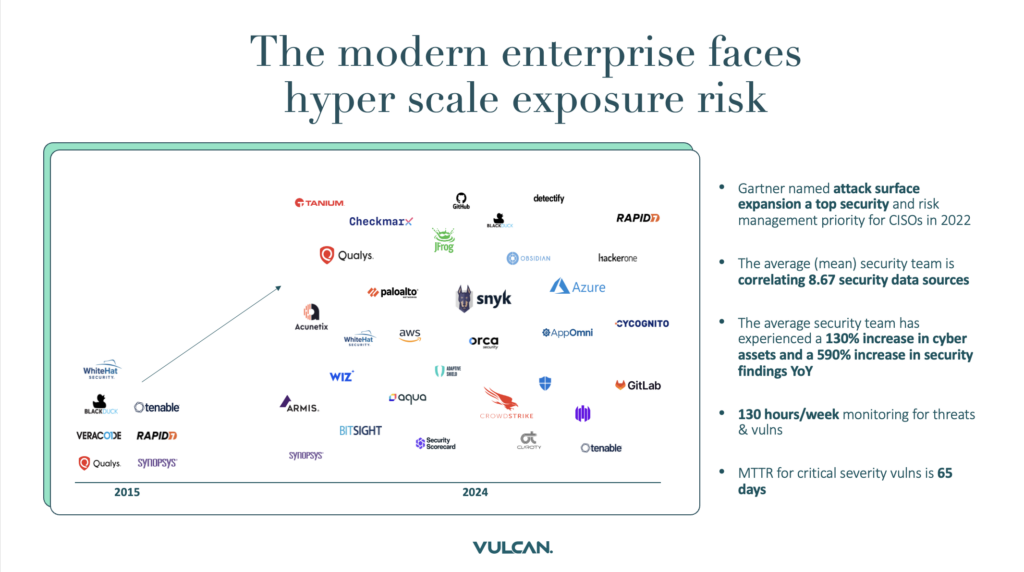
Enterprise cyber security teams use multiple vulnerability scanners to identify risks to the business. However, the sheer volume of scan data overwhelms these teams, causing inaccurate and time-consuming prioritization and misdirected remediation efforts.
Security teams must manage all attack surfaces and prioritize critical risks while collaborating efficiently with remediation stakeholders.
The exposure is high, the impact substantial, and the cost skyrocketing:
And as the market evolves, so do we.
The previous time we strategically evolved to the needs of the market, it was around understanding risk level, and educating the market that there is a connection between business risk and vulnerabilities.
Today, the market is well-versed in this connection. And recognition by the likes of Omdia and Forrester reflects that we at Vulcan Cyber are at the heart of this paradigm. It also presents us with an opportunity to think bigger.
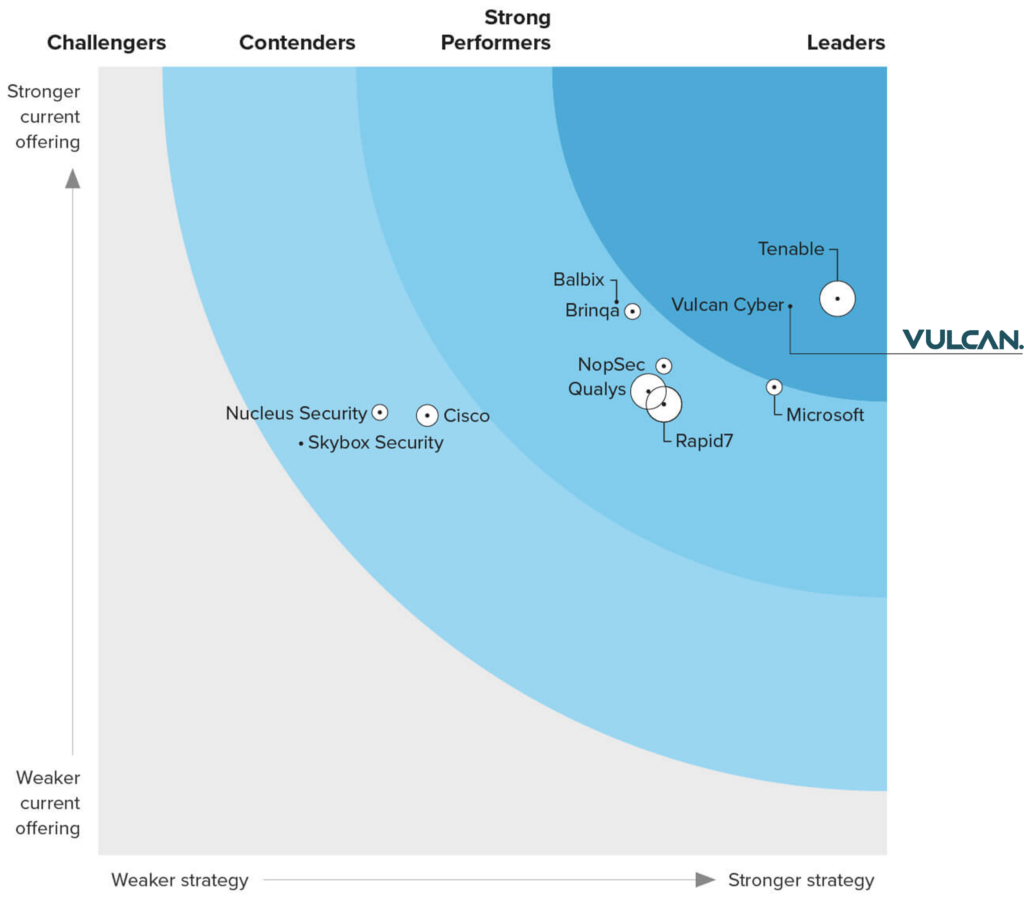
The next step is putting everything in context. And this is where the idea of exposure enters the frame.
Put plainly, exposure encompasses any vulnerability that leaves the organization open to attack or exploitation. This includes common cyber security exposures like CVEs, as well as misconfigurations, data security issues, compliance lapses, and any other potential risk factors.
It also covers emerging threats and new technologies that could potentially expose the organization to future risks.
Today, there is more to the world of exposure than there was before. And this is at the heart of what we want to communicate to the market: The landscape of cyber security exposures is wider than it was, and is always growing.
We’ve seen this scenario before, with the evolution of the SIEM and SOAR markets. The leading tools in this space have been built on robust and scalable data processing capabilities with operational functionality on top to address all current and future post-breach use cases.
And just as these tools are built to allow effective response against even unprecedented threats, we’re encountering the same need in the pre-breach world today.
What’s more, we believe that there is no technological need or monetary justification to create multiple exposure aggregation platforms with single use cases, especially as the number of use cases continues to climb.
We’ve felt this throughout discussions with our customers, at RSA this year – where data overload was a primary concern among many attendees – and even discussed it in detail at our most recent CyberRisk Summit:
The solution IT security teams deserve needs to be built not only for today’s exposure risk challenges, but also for tomorrow’s. Moreover, it must consolidate datasets, including inventory across the attack surface, various types of exposures, ownership information, and workflow signals, into one comprehensive platform.
Over time, we expect to see this become pronounced in the market, with more and more teams looking for one operating system for exposure risk management.
Our mission is to provide a single platform that enables teams to manage, communicate, and mitigate risks from one place. Our solution, grounded in the principles of contextualized data, clear ownership, and streamlined, automatable processes, empowers enterprise security practitioners to do their jobs in the most efficient way possible.
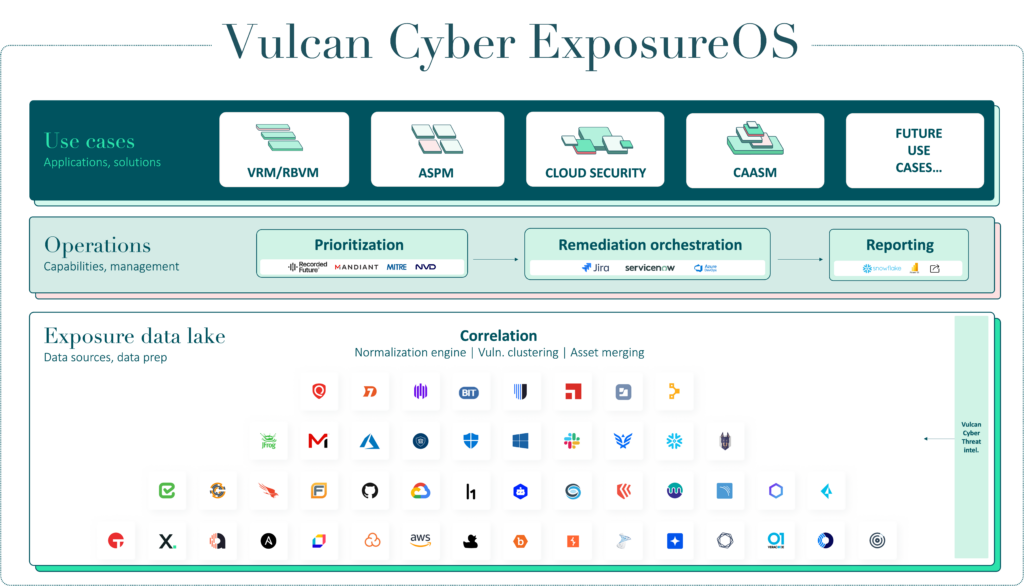
Most importantly, the Vulcan Cyber ExposureOS provides the foundation atop which any current or future exposure management use cases can be built. Just plug in your data, and Vulcan Cyber will give you the context and workflows you need to take action against the most critical exposure risk – wherever it may be in your organization
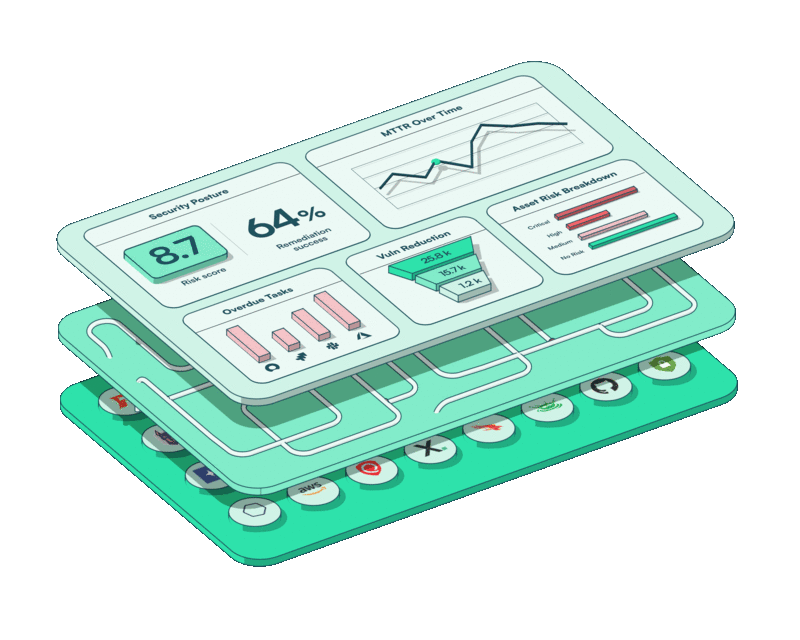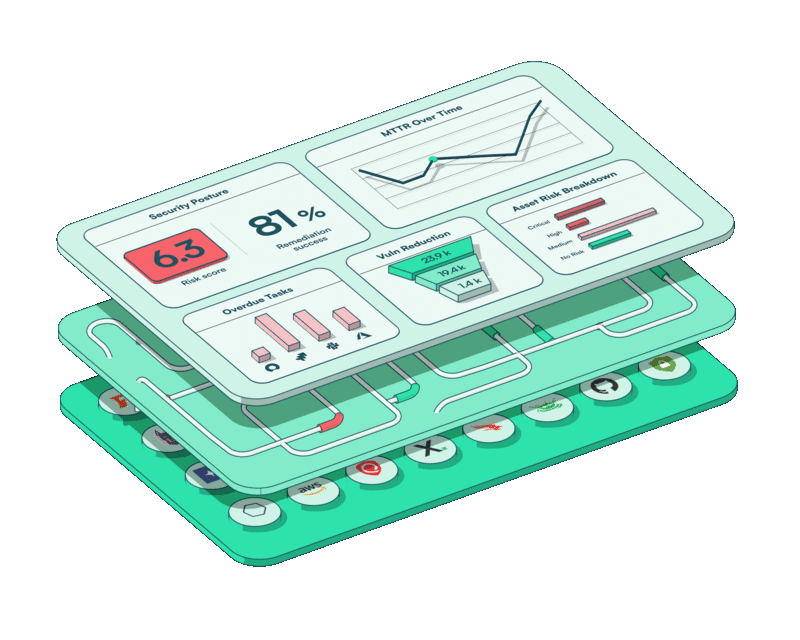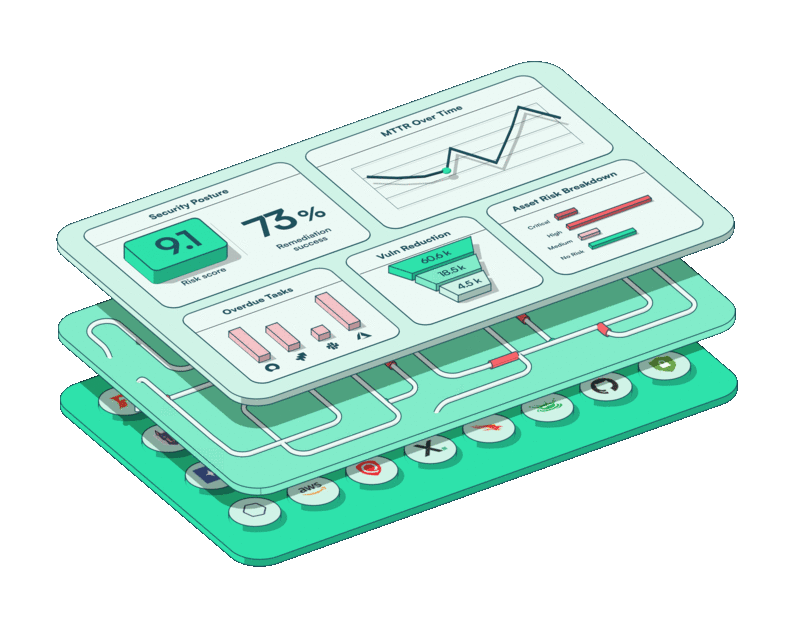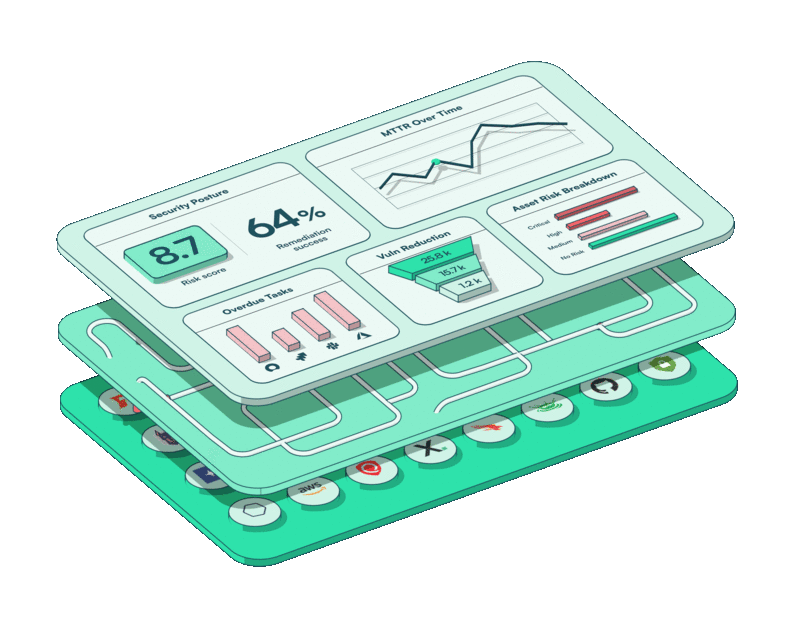
It’s in this context that our recent brand refresh isn’t simply a cosmetic one. It marks a strategic step forward to engage a broader market through a mature, single-minded design.

Our now-unified logo reiterates our message of “one” platform, while the accordion-style layered design you’ll find on our home page drives home the complexity running under the hood of a streamlined and user-friendly interface.
Meanwhile, more mature fonts and a sophisticated color palette augment a rebranding that is built to reflect a fast-approaching future – and where we see ourselves in it.
All of the design and messaging decisions we have taken underscore our promise: To provide an operating system that becomes second nature to security teams – one they can lean on, swear by, and put to the test against their biggest exposure risk challenges.