First Officer’s log, Terrestrial date, 20220804. Officer of the Deck reporting.
The Captain has authorized liberty call for much of the crew to take part in a local Independence Day celebration. Apparently, the world separated from their colonial power after a disagreement over some beverage imports. It is quite a big deal for the locals and the crew is looking forward to sharing the experience. However, as a fleet support element, we remain at a normal alert level. The reality is that hostile forces often use the distraction of local celebrations as a cover for their activities. As always, we remain positioned to provide support to deal with hostile actions. Did anyone say LockBit?!
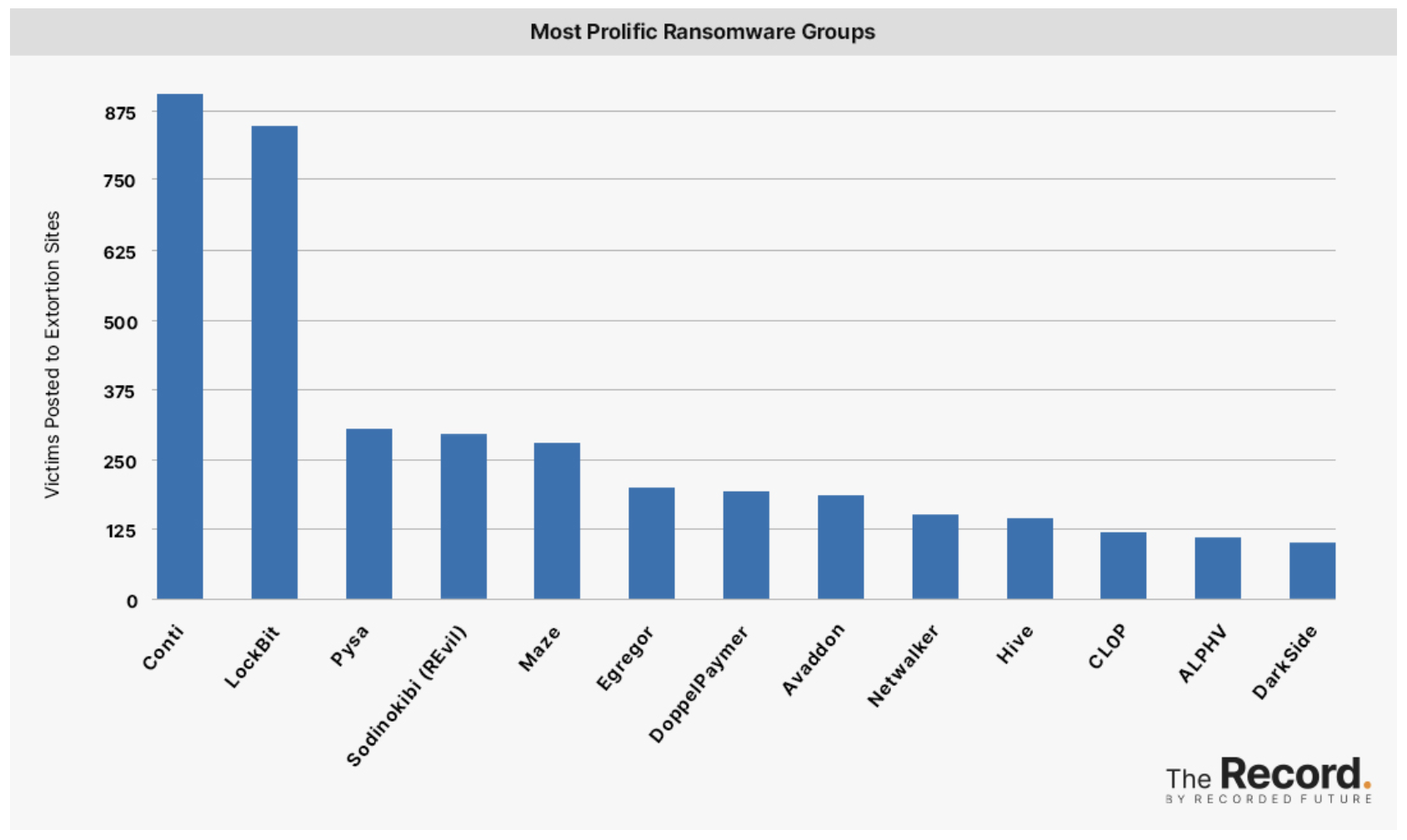
If there was any doubt that LockBit had turned pro
What happened
The LockBit malware gang has announced a bug bounty for anyone who finds flaws in their attack applications. This is a page taken straight from several major developer’s playbook, such as Microsoft, Apple, Google, and quite a few others.
Why it matters
Malware gangs are well past the point of being “gangs” and are run more like professional development organizations and organized crime syndicates. We’ve been seeing their capabilities evolve for quite a few years and, as they mature, they become more and more like a regular business. Albeit one that’s focused on criminal activities and operating without any regard to the damage they do in the name of profit. It’s worse when we recognize that there is quite a bit of overlap between purely criminal organizations and the State and State Sponsored ones that use the same tactics and techniques in support of a national agenda.
What they said
“LockBit adds a bug bounty program in its revamped ransomware-as-a-service operation…” Read more here.
They never seem to stay gone
What happened
The Advanced Persistent Threat (APT) group known as Bahamut has resurfaced with a new version of their malware targeting android devices. They’re going after targets in Asia and the Middle East with phishing campaigns that use very convincing web sites to deliver their malware payload.
Why it matters
Bahamut here is putting the Persistent in Advanced Persistent Threat. They are also showing how good a job threat actors can do in creating inviting “bait” websites. The site they created for this malware campaign looks professional and convincing. Though given how many tools are available, it’s really not hard to create a site that looks like it was created by a legitimate organization in support of a legitimate application.
While we, as an industry, have done a lot to improve user awareness this shows that there can still be a long way to go. It also points to a need for more effective anti-malware tools for mobile devices, and in some cases, more visibility for organizations that let their employees use their personal devices for work.
What they said
A new variant of the Bahamut malware calls for specific attention from the news.
Still in the news
What happened
A couple of weeks ago the Hermit spyware framework made a splash, as a new strain of professionally developed spyware marketed to Law Enforcement, Intelligence, and other agencies. We’re still seeing ripples from the revelation, which is probably a good thing™.
Why it matters
Tools like Hermit could be subject to a lot of abuse if there is not sufficient oversight, or they’re hired out to organizations that probably shouldn’t have legal access in the first place. National policies on personal privacy can vary widely from country to country, where some would have strict rules on deploying something like this and others would…
NOT.
What they said
Directly from the team that discovered Hermit, read what they had to say.
Want to get ahead of the stories? Join the conversations as they happen with the Vulcan Cyber community Slack channel