MITRE recently unveiled this year’s lineup of the top 25 most perilous weaknesses that have been afflicting software over the past two years.
The term “software weaknesses” encompasses a broad spectrum of issues which include flaws, bugs, vulnerabilities, and errors present in the code, architecture, implementation, or design of software solutions. These weaknesses pose a substantial threat to the security of systems where the software is installed and operational. They can function as entry points for nefarious actors aiming to seize control of the compromised devices, access confidential data, or induce denial-of-service states.
Overview & methodology
To compile this list, MITRE scrutinized and rated each weakness based on its gravity and commonality, following an analysis of 43,996 CVE entries listed in the NIST’s National Vulnerability Database (NVD). The analysis covered vulnerabilities identified and documented throughout 2021 and 2022, with particular emphasis on CVE records incorporated into CISA’s Known Exploited Vulnerabilities (KEV) catalog.
MITRE explained, “After the collection, scoping, and remapping process, a scoring formula was used to calculate a rank order of weaknesses that combines the frequency (the number of times that a CWE is the root cause of a vulnerability), with the average severity of each of those vulnerabilities when they are exploited (as measured by the CVSS score). “In both cases, the frequency and severity are normalized relative to the minimum and maximum values observed in the dataset.”
The 2023 top 25 weaknesses identified by MITRE are hazardous owing to their substantial impact and their pervasive presence in software launched in the previous two years.
Successful manipulations could permit attackers to usurp full control over the targeted systems, extract and leak confidential data, or initiate a denial-of-service (DoS) condition.
Through the dissemination of this list, MITRE aims to equip the larger community with pivotal insights concerning the gravest software security weaknesses warranting urgent focus.
CWE Top 25 software weaknesses 2023
|
Rank |
ID |
Name |
Score |
CVEs in KEV |
Rank Change |
|
1 |
Out-of-bounds Write |
63.72 |
70 |
0 |
|
|
2 |
Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) |
45.54 |
4 |
0 |
|
|
3 |
Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) |
34.27 |
6 |
0 |
|
|
4 |
Use After Free |
16.71 |
44 |
+3 |
|
|
5 |
Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) |
15.65 |
23 |
+1 |
|
|
6 |
Improper Input Validation |
15.50 |
35 |
-2 |
|
|
7 |
Out-of-bounds Read |
14.60 |
2 |
-2 |
|
|
8 |
Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) |
14.11 |
16 |
0 |
|
|
9 |
Cross-Site Request Forgery (CSRF) |
11.73 |
0 |
0 |
|
|
10 |
Unrestricted Upload of File with Dangerous Type |
10.41 |
5 |
0 |
|
|
11 |
Missing Authorization |
6.90 |
0 |
+5 |
|
|
12 |
NULL Pointer Dereference |
6.59 |
0 |
-1 |
|
|
13 |
Improper Authentication |
6.39 |
10 |
+1 |
|
|
14 |
Integer Overflow or Wraparound |
5.89 |
4 |
-1 |
|
|
15 |
Deserialization of Untrusted Data |
5.56 |
14 |
-3 |
|
|
16 |
Improper Neutralization of Special Elements used in a Command (‘Command Injection’) |
4.95 |
4 |
+1 |
|
|
17 |
Improper Restriction of Operations within the Bounds of a Memory Buffer |
4.75 |
7 |
+2 |
|
|
18 |
Use of Hard-coded Credentials |
4.57 |
2 |
-3 |
|
|
19 |
Server-Side Request Forgery (SSRF) |
4.56 |
16 |
+2 |
|
|
20 |
Missing Authentication for Critical Function |
3.78 |
8 |
-2 |
|
|
21 |
Concurrent Execution using Shared Resource with Improper Synchronization (‘Race Condition’) |
3.53 |
8 |
+1 |
|
|
22 |
Improper Privilege Management |
3.31 |
5 |
+7 |
|
|
23 |
Improper Control of Generation of Code (‘Code Injection’) |
3.30 |
6 |
+2 |
|
|
24 |
Incorrect Authorization |
3.16 |
0 |
+4 |
|
|
25 |
Incorrect Default Permissions |
3.16 |
0 |
-5 |
Analysis
Numerous significant changes have been observed in the ranking of weakness types compared to last year’s list, encompassing weaknesses that have either fallen off the list or are debuting in the Top 25.
Starting with the good news, Uncontrolled Resource Consumption(CWE-400) and Improper Restriction of XML External Entity Reference(CWE-611) are no longer on the top 25 as remediation owners are getting better in preventing these vulnerabilities from occurring in the wild. Presumably, this also has to do with the declining use of XML and the increasing use of managed code to better control resource allocation.
The newcomers on the list are Improper Privilege Management(CWE-269) and Incorrect Authorization(CWE-863), both relating to access control. This would indicate that this is an increasing challenge for application developers as systems and permission handling are becoming more complex.
The biggest movers up the list are:
- CWE-269: Improper Privilege Management from #29 to #22
- CWE-863: Incorrect Authorization from #28 to #24
The biggest downward movers are:
- CWE-502: Deserialization of Untrusted Data from #12 to #15
- CWE-798: Use of Hardcoded Credentials from #15 to #18
- CWE-276: Incorrect Default Permissions from #20 to #25
New entries in the Top 25 are:
- CWE-269: Improper Privilege Management from #29 to #22
- CWE-863: Incorrect Authorization from #28 to #24
Entries that fell off the Top 25 are:
- CWE-400: Uncontrolled Resource Consumption from #23 to #37
- CWE-611: Improper Restriction of XML External Entity Reference from #24 to #28
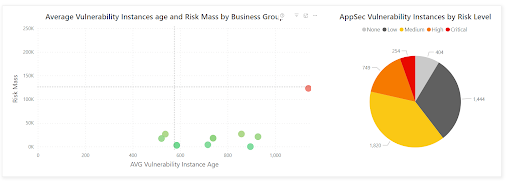
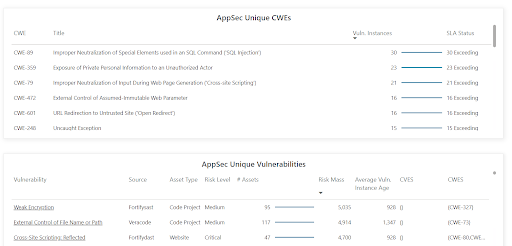
Manage CWE risk with Vulcan Cyber
Track your top CWEs with the Vulcan Cyber platform using reports and automation to expedite remediation where it matters most.
And finally…
Each new vulnerability is a reminder of where we stand, and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors: