First Officer’s log, Terrestrial date, 20221104. Officer of the Deck reporting.
With the impending release of the communications system update by [REDACTED] to the subspace communications network, we repositioned the ship to be ready to render assistance wherever needed. As expected, the update was distributed on time. At least, as expected when dealing with the [REDACTED] who take their role in securing subspace communications seriously.
In our communications leading up to the broad-scale update, we had tried to reassure the worlds we support that there was no reason to panic. We agreed that it was possible that one of the Federation’s adversaries would manage to find and exploit the then-unknown vulnerability, analysis indicated that it was unlikely. There was simply not enough time, and anyone who was paying attention was already prepared to address an attack if it came.
What hadn’t been expected was that when the [REDACTED] revealed the vulnerabilities they were correcting, they would also downgrade the threat. It seemed that not only had they gotten the update out before a hostile force could exploit it, but the threat itself wasn’t actually that severe.
On some levels, it appeared we had dodged a photon torpedo. A vulnerability that could have compromised communications across the Federation and beyond turned out to be the common break-fix situation we dealt with on a daily basis.
After the release, we resumed the course for Frontier Station [REDACTED] and updated our protocols to be able to handle any requests for assistance with the subspace network. It was no longer considered a critical threat, but it was still a high priority and not every world, station, or outpost, would be able to deploy it cleanly on its own.
We were also aware of the fact that other threats might emerge from this. Though, to be fair, new threats were emerging all the time. As a support ship, we weren’t in the position of finding them of course, but we were in the position of reacting and helping correct them when they came to light.
For the time being, we would keep on top of the situation while shifting our primary focus to the situation on Frontier Station [REDACTED].
We’ve heard this story before
What happened
Recent reports of multiple media outlets suffering cybersecurity breaches have focused attention on the media industry as a whole. While their assets are not always tangible, media organizations can be an inviting target for cyber-attack. Customer and employee information can be very valuable to attackers, as is intellectual property. That is not even considering the implications of a threat actor being positioned to potentially manipulate the media directly.
Why it matters
The specific attacks here were an insider threat and a configuration that left data exposed to the open internet. Internal threats are always a challenge, regardless of industry, but they can be especially vexing in the media world where things move quickly and not everyone can be expected to maintain security awareness.
There are security tools that can help in each case, and risk management can tie it all together. But with rogue users especially, it can be hard to anticipate when a threat will emerge. Though even with the rogue user scenario, there are ways to mitigate the risk and contain the potential damage.
What they said
It’s no surprise to see media outlets draw considerable attention to this story.
We did say not to panic, after all.
What happened
Tension over the OpenSSL vulnerability remained high until the update was released, and the developers lowered the threat level from Critical to High after additional review. Even with the release of the update and reduced threat analysis, updating where necessary remains a priority.
Why it matters
Up until the day before the update was released, there was some serious concern that this could become another Heartbleed, even though there was no indication that threat actors knew what the vulnerabilities were or how to exploit them. The subsequent reduction from Critical to High was a Good Thing™ but doesn’t mean there’s no cause for concern. We’ve seen enough examples of new vulnerabilities appearing after a patch to stay alert.
For now, our advice holds. Apply the updates as soon as possible and stay alert. Because, you know, the world needs more Lerts.
What they said
Even if it didn’t out to be quite as serious as was feared, “critical” vulnerabilities will always get people talking.
PoS terminal security – threat actors make mistakes too
What happened
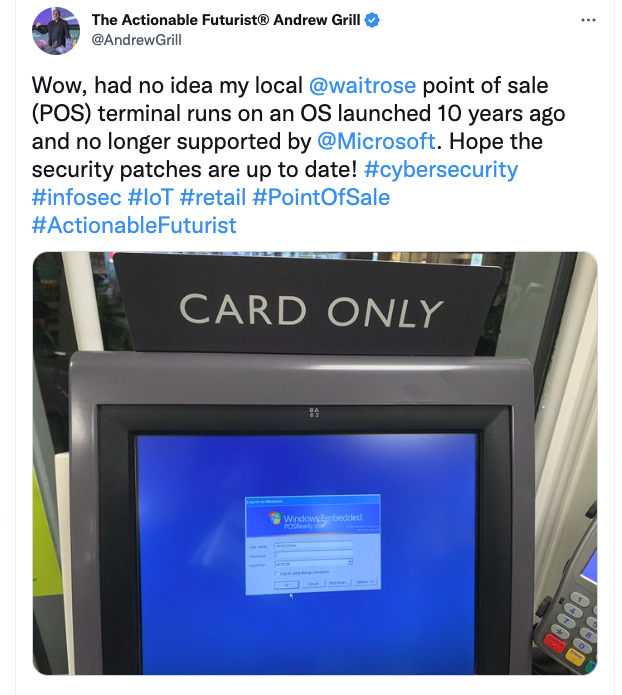
A recent report by a threat intelligence organization has revealed that threat actors are still actively compromising point of sale (PoS) terminals to steal credit card information, even as they shift to other techniques in the face of improved defenses. It’s notable that they discovered the threat actor’s command and control network because of poor configurations on the threat’s part.
Why it matters
There are two notable takeaways from this. The first is that threat actors can make the same mistakes their targets do, which can sometimes be used against them. While we’re legally and ethically not allowed to “return fire” so to speak, no matter how much we might like to, those mistakes can give the appropriate authorities the tools they need to act. Because unlike us, Law Enforcement can often return fire against cybercriminal gangs.
The second takeaway is that even though PoS terminal security has improved, they’re still not entirely safe. While the US lagged Europe and Asia in adopting chip-enabled cards, which are considerably more secure than the magstripe cards that are still in use, the situation has been changing. Unfortunately, as the number of attacks on PoS terminals appears to have dropped, credit card thieves have shifted tactics and are still able to steal a billion dollars’ worth of cards annually.
What they said
With so much at stake when it comes to PoS terminal security, it’s no surprise this one is getting plenty of attention.
___________________________________________________________________________________________________________________________
Want to get ahead of the stories? Join the conversations as they happen with the Vulcan Cyber community Slack channel









