Security, productivity, and performance don’t necessarily go hand in hand. Cloud computing has proliferated, remote work is ubiquitous, and many companies now look to the cloud as their primary platform for application use, collaboration, and data storage. Growth and modernization bring larger markets, higher revenue, and business agility. At the same time, organizations relying on cloud services and applications for their day-to-day operations. face new challenges when it comes to public cloud security.
These include increased risk of data loss, theft, and fraud; higher operational costs and performance issues due to more frequent maintenance and support; reduced control over access to sensitive content; and decreased ability to enforce security policies due to lack of visibility into user activity. Security is critical, but “secure” shouldn’t mean slower or costly.
Public cloud migration and usage offer many benefits, including increased flexibility, scalability, and reduced cost. However, as organizations adopt more applications and workloads in the public cloud, they face challenges in ensuring their sensitive information remains private and protected while avoiding potential loss of intellectual property (IP) assets. IBM’s Cost of a Data Breach report for 2023 showcases this, revealing that migration to the cloud remains one of the biggest amplifiers of data breach cost:
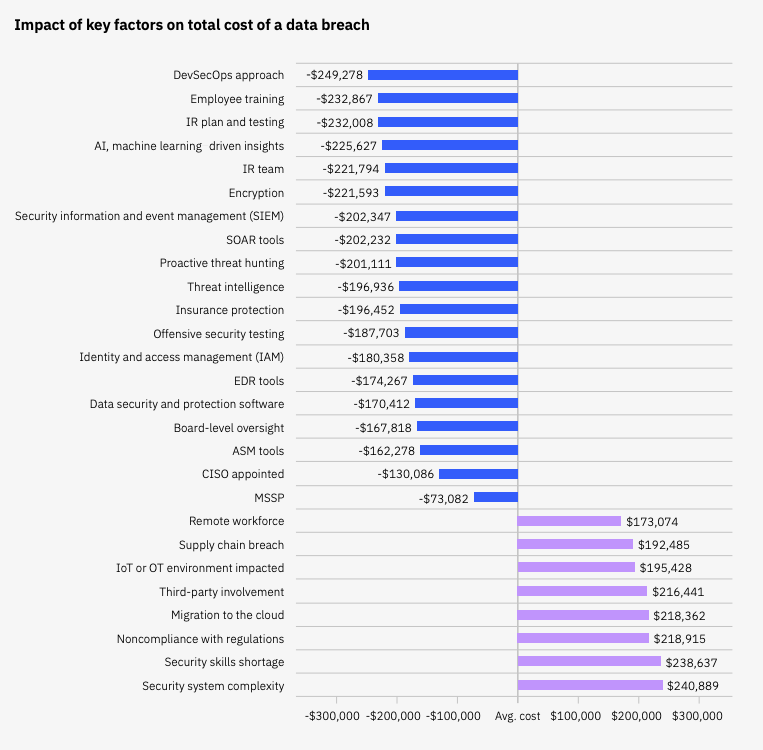
To achieve optimal results, IT leaders must understand how to balance the risks associated with moving to the cloud while maximizing the benefits offered by the technology.
Security is not free
Security is one of the most challenging yet necessary business aspects for any organization. It is crucial to maintain it, but quantifying the value is difficult even with the most advanced tools. Unfortunately, it’s easy to show its direct and sometimes negative impacts on performance and measure the added demands on staff.
Don’t compromise on security
For applications in the cloud, meeting privacy and security challenges is a complex problem. Engineers skilled in securing on-premises applications and infrastructure are rarely adept in the differences in the cloud, resulting in poor optimization and accidental exposures. Even existing security toolsets tailored for on-premises security may need to be more cloud-friendly, leading to issues with licensing, failing to scale, and the inability to detect or prevent critical flaws.
Organizations can take the ostrich approach to this problem and not even bother focusing on security. While this eliminates the upfront costs of implementation, it creates a more significant issue down the road when a breach or an incident occurs—which is far more likely when an application is an easy target.
Incident costs are far too significant to ignore, with IBM estimating the cost of a data breach in 2023 at $4.35 Million. This amount includes everything that goes into remediation, from engineering to closing the exposures to costs to address legal and compliance failures. Waiting for a breach to happen only moves the time a payment happens and multiplies it far beyond what it would have cost to prevent it in the first place.
In 2022, Crypto.com learned a lesson about securing its application the hard way. Attackers bypassed their multifactor authentication to steal $18 million in bitcoin and $14 million in ethereum. Crypto.com was able to reimburse users who had suffered losses. Even after they restored users, there were still additional costs to correct the exposure, resulting in a self-insurance program to protect users who have currency stolen via unauthorized withdrawals.
Impacts on application performance
While necessary, protecting your application can come with challenges when security controls are added. One of the primary areas where security controls directly impact applications is performance. Even the best controls add some overhead, while those that are a poor fit can drag performance to a crawl.
There are many reasons for decreasing performance, such as legacy tools not always being cloud friendly. Tools must be designed to leverage the cloud’s functionality and features, such as scaling. Solutions that require manual configuration add friction to operations and may stop working with licensing that adapts well to the dynamic environment.
Applications also are impacted by identity and access controls that are necessary for restricting access yet slowing down a cloud application. These controls also come with additional overhead for managing and maintaining the proper access rights. Failing to stay on top of this maintenance leaves lingering permissions and overexposed data.
Data security controls such as encryption come with processing overhead to calculate encrypted values and decrypt. This overhead multiplies for heavily used data stores or databases when fields are constantly being altered or accessed, degrading overall application performance.
Impact on staff
Maintaining security tools comes with dedicated time for staff for every additional solution added. There is time invested into the unique configuration of each product and the daily operations, including monitoring and managing the solution. Many tools come with simple monitoring interfaces, but these only tell the part of the story that tool has visibility into. Time and skill are required to draw actionable security insights across multiple solutions, diverting time away from investments in other initiatives.
Must dos of cloud security
That security brings challenges in implementation and management does not mean there is no relief. Implementing security purposefully across your cloud environment will help to streamline and simplify processes.
1. Implementing broad-reaching controls
Every additional security solution in the cloud adds extra complexity and overhead to manage. Eliminating one-off fixes in favor of unified solutions and multitaskers reduces this. Unified solutions simplify operations by bringing multiple functionalities under one roof.
By combining information into single dashboards, staff can generate more insightful insights on the fly, without having to do additional legwork. With a unified solution, configuration changes and management are no longer spread across multiple tools and interfaces. Instead, it resides in one location. This reduces the time staff requires to make a change and streamlines the training process for new team members learning the environment.
Identity access management (IAM) and identity governance administration (IGA) also help to streamline and simplify operations. Using IAM or IGA to manage identity access across the cloud eliminates handling one-off access processes. They allow changes to be made in one place, such as removing access to propagate throughout the environment. When users are added, removed, or change roles, there is no longer a need to access every cloud resource and update access rights accordingly. The changes made in one location permeate the environment.
2. Streamline and automate
Controls and solutions that affect multiple aspects of your cloud environment simultaneously simplify operations. Automating the tasks and processes that can reduce the impact on engineer time eliminates repetitive tasks. Automating jobs also ensures that steps are never missed, removing additional management and scheduling investment for team members. Automation also removes the roadblocks in waiting for someone to “do something,” which streamlines operations.
Improvements in configuration management can be made using baseline images that have already been hardened and patched to a recent point in time. Using baseline images removes configuration time and ensures new nodes are created in alignment with organizational policies. It creates a consistency of security across the cloud environment and eliminates the risk of a single instance being vulnerable due to missing a hardening step during configuration.
3. Built for the cloud
Only some security solutions have the functionality to integrate with cloud applications and technologies easily. Finding solutions built for the cloud improves performance and ensures that they scale with your environment. Cloud-first solutions already have flexible licensing that allows consistent tracking of active utilization rather than counting a license used every time a new node is created.
Cloud-first technology can also communicate and track the state of the ephemeral cloud environment. For example, a vulnerability management solution built for the cloud can track nodes, differentiating vulnerabilities and findings across them rather than creating redundant records when new nodes are created or destroyed.
4. Balancing performance and cost
Getting security for your cloud environment does not have to come at a tradeoff of cost or performance. You can find a balance between both. Utilizing open-source tools is one way to lower costs when used judiciously. They do not have upfront costs in purchasing, but additional overhead may lurk in added configuration, management, and troubleshooting to keep it operating at peak efficiency.
Finding comprehensive solutions to simplify the stack improves performance and bundles multiple functionalities under one platform, which may be more cost-effective. It streamlines operations by consolidating interfaces, saving engineering time in management and maintenance. Using a bundled solution, the incorporated tools are designed to work collectively, reducing conflicts across tools, which helps reduce the performance impact.
Public cloud security – the final word
Vulcan Cyber® helps organizations consolidate data in one place, focusing on vulnerability exposure risk that truly matters. The Vulcan Cyber platform integrates with your security stack, simplifying operations to allow organizations to more effectively manage their risk and vulnerability data across applications, cloud, and network assets. Vulcan empowers your organization to streamline its security program, reaping performance benefits in the application and reducing the impact on staff performance.
Schedule a live demo today to learn more about how Vulcan can improve your public cloud performance while maintaining top-tier security.








