SolarWinds, known for the significant security breach of its Orion platform in 2020, has recently addressed five vulnerabilities in its Access Rights Manager (ARM) solution. This proactive measure aims to secure the platform against similar threats and safeguard user data across various agencies and corporations.
Here’s what you need to know about the latest SolarWinds vulnerabilities:
What are the SolarWinds vulnerabilities?
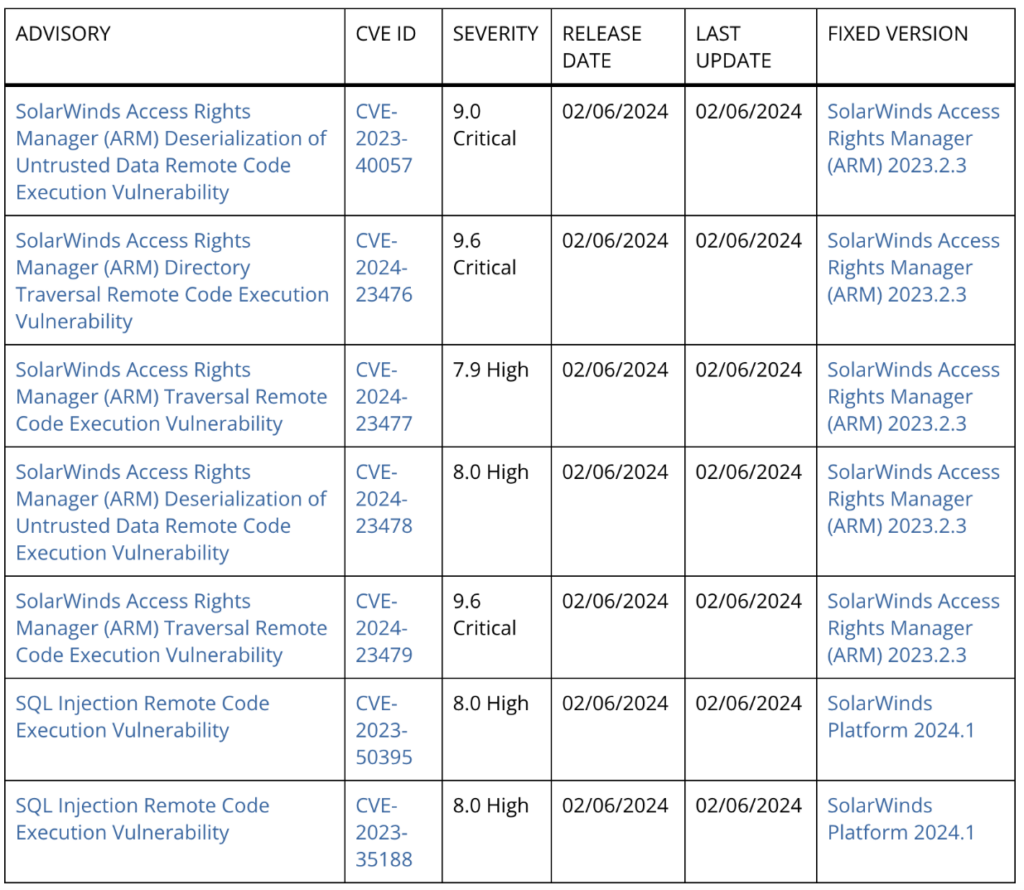
Five RCE vulnerabilities, including three critical ones, in SolarWinds’ Access Rights Manager have been patched after discovery by Trend Micro’s Zero Day Initiative. These flaws could potentially allow unauthorized remote code execution in software integral for managing user permissions across various services.
The critical vulnerabilities, CVE-2024-23476 and CVE-2024-23479, highlighted in a SolarWinds’ advisory, pose a significant risk of unauthenticated remote code execution, while another, CVE-2023-40057, could be exploited by authenticated users. Two other vulnerabilities were deemed “high” severity.
Do they affect me?
Many organizations utilize SolarWinds Access Rights Manager (ARM) for overseeing and auditing permissions throughout their IT networks, ensuring secure and efficient access management.
The vulnerabilities affect SolarWinds ARM versions 2023.2 and earlier. It is recommended to check your versions of ARM and ensure you are not exposed.
Have the SolarWinds vulnerabilities been actively exploited in the wild?
There is currently no mention of them being exploited by attackers.
Fixing the SolarWinds vulnerabilities
In its advisory, SolarWinds recommends updating instances of ARM to version 2023.2.3, which fixes the vulnerabilities.
Next steps
Each new vulnerability is a reminder of where we stand and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors:










