On a more personal note
This news marks a significant milestone for Vulcan Cyber as we officially conclude a $55 million Series B round, led by trusted investors Maor Investments and Ten Eleven Ventures. For an Israeli-founded company, this achievement is all the more momentous, especially considering the recent tragic events in Israel over the last month. In the midst of darkness, there’s a glimmer of light.
Over the past year and a half, I’ve discussed extensively the expansion of attack surfaces and its impact on already siloed security programs. CISOs are grappling with the challenges posed by growing threats from applications, cloud environments, networks, and IoT. To manage and secure this complexity, they often add an increasing number of security tools to their stack. In fact, our survey at the end of 2022 revealed that 95% of organizations were using at least two vulnerability scanners. This number has likely doubled since then.
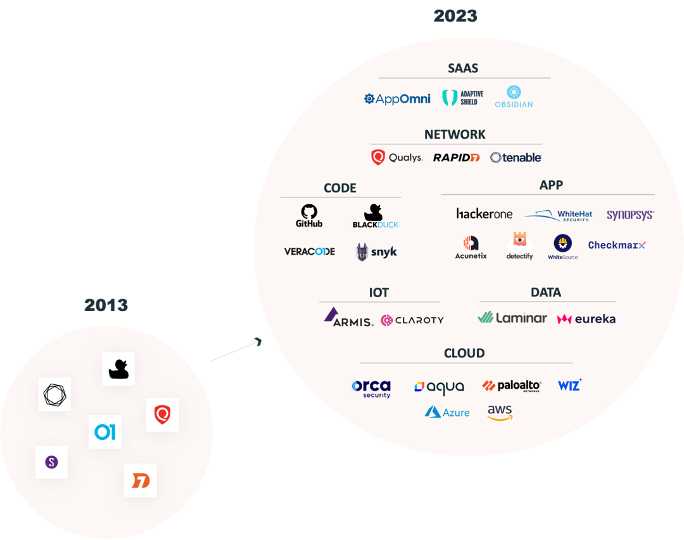
The expanding attack surface over the last decade
But the problem is that adding more tools creates even more problems: 100 times more noise and alerts, siloed scan data, different risk types, and different platforms to monitor them, a significant operational burden, and of course, growing risk. It’s a vicious cycle of risk, with an overwhelming number of tools to manage it.
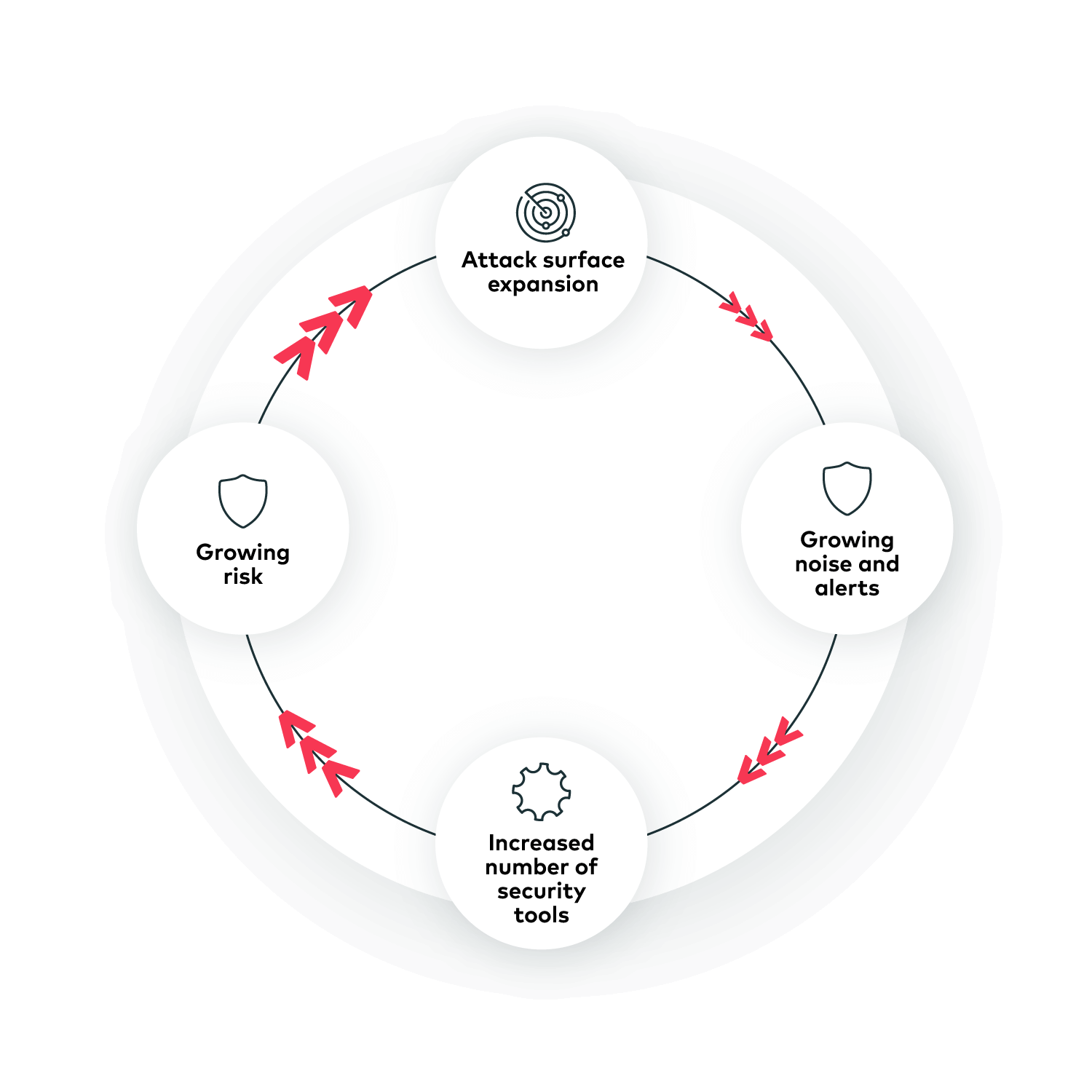 The growing attack surface poses significant challenges — more tools to manage, adding to the complexity of handling increased risk
The growing attack surface poses significant challenges — more tools to manage, adding to the complexity of handling increased risk
The decentralized vulnerability management market
Beyond the growing number of scanners organizations use, CISOs have, in recent years, adopted various iterations and approaches to vulnerability management to help them manage and orchestrate accumulating vulnerability risk:
- CAASM – Cyber Asset and Attack Surface Management oriented platform data that instrument and unify cyber inventory and asset data across infrastructure and cloud.
- ASPM – Application Security Posture Management platforms aggregate AppSec findings and integrate this data with software development lifecycle (SDLC) and DevSecOps processes.
- RBVM – Risk-Based Vulnerability Management platforms aggregate vulnerability and asset data and prioritize vulnerability risk.
Each of these approaches offers great capability in managing risk, but only for the specific type of risk it’s configured to handle in the first place – ASPM for apps, CAASM for IT assets, RBVM for vulnerability management teams working to secure traditional network infrastructure. According to Gartner, “It is forecasted that by 2024, about 50% of the overall attack surface management market will be owned by large vendors with more than $1 billion in revenue, and by 2026, more than 40% of organizations developing proprietary applications will adopt ASPM.”
But once again… we are left with endless scanners, and disparate approaches and platforms to manage them.
A unified posture and attack surface management platform
The future of this market lies in the unification and convergence of cyber risk management platforms. The umbrella category to encompass these capabilities is exposure management (sometimes referred to as CTEM, or Continuous Threat Exposure Management). According to Gartner, by 2026, organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer a breach. A unified exposure management platform ensures the visibility of the entire attack surface including cloud, application, network, SaaS, Mobile IoT, and more.
This is precisely the mission of Vulcan Cyber. We are here to deliver the one platform for exposure management to the cyber security market — from the aggregation of vulnerability and asset scans and contextualized prioritization, to remediation orchestration, mitigation, and reporting across all attack surfaces.
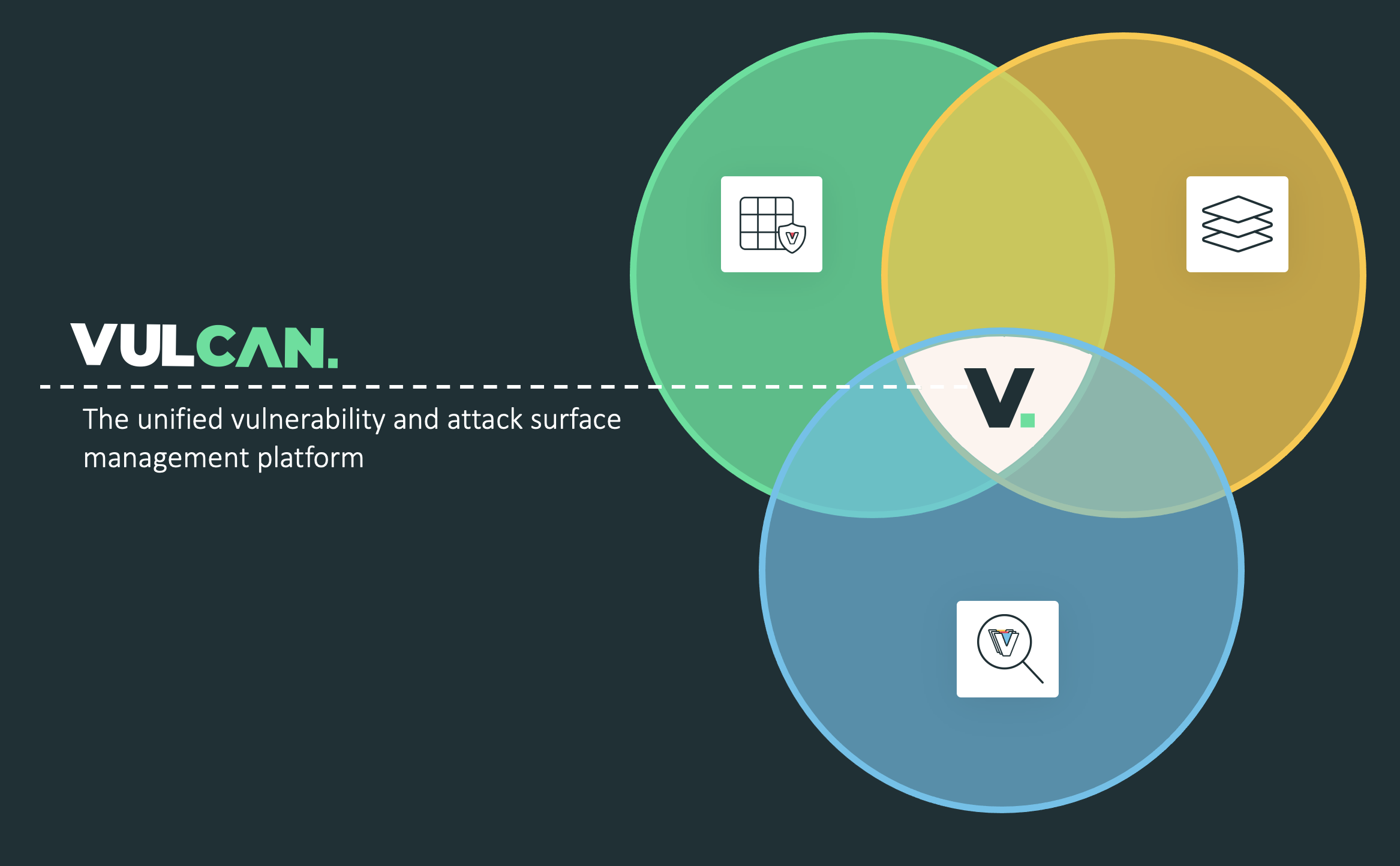
The Vulcan Cyber approach to a converged cyber risk management solution
This ‘convergence’ is at the heart of our Series B round of funding. It’s our vision and strategy. We believe in the market potential, and so do our investors. Recent industry validation signals that we are on the right path. We’ve been on hundreds of calls with our customers, prospects, and valued security professionals, and we’ve heard it from them, too. The demand is there, and now we will deliver the platform to own and mitigate cyber risk across the entire attack surface — in unified solution.
To hear more about this unified approach to cyber risk and exposure management, attend my session at the CyberRisk Summit on December 5, 2023. Registration is open, and it’s completely free. You can also schedule a demo with one of our experts to learn more about how exposure management can help you effectively manage risk.










