Ideally, teams leverage threat intelligence frameworks to more efficiently uncover blind spots, gain visibility, and improve their security posture. And, with threats proliferating every day, even a slight increase in efficiency could be the difference that prevents a data breach.
The key goal, when faced with so many vulnerabilities all at once, is to identify and mitigate the cyber risk that represents the biggest impact on your organization. And when used correctly, threat intelligence provides the critical support needed in this area.
Vulcan Cyber and Gartner Peer Insights surveyed 100 IT security, vulnerability management professionals, and threat intelligence practitioners to understand how they use threat intelligence in their organizations. Here are some of the key takeaways:
Dedicated teams for threat intelligence, but budget doesn’t necessarily follow
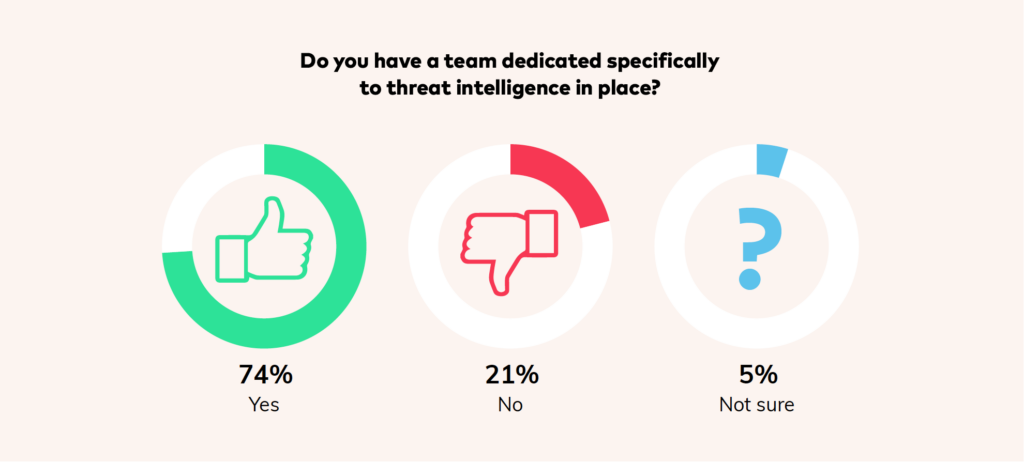
Most of the organizations surveyed have a dedicated threat intelligence team, with 75% indicating that they have an in-house department to make sense of vulnerability data.
But while the teams may be in place, only two-thirds of organizations say that they are backed up with a budget specifically to address threat intelligence needs.
Information is only as powerful as the action it prompts. And – if teams have greater visibility of vulnerability data but not the resources to do anything about it – organizations are continuing to leave themselves exposed to attackers – only with a front-row seat to the action.
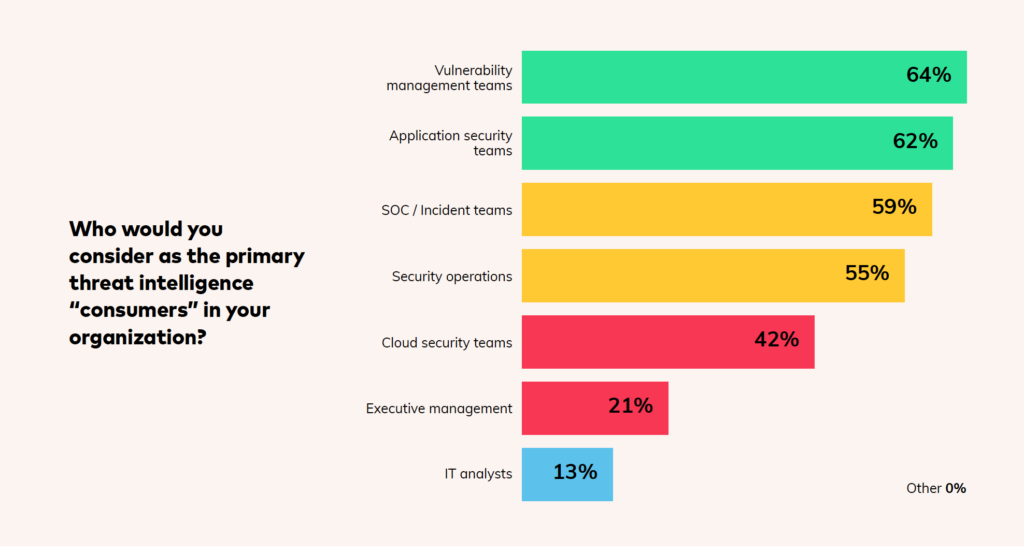
Familiar faces the biggest “consumers” of threat intelligence
Vulnerability management (64%), application security (62%) and SOC/incident (59%) teams are the main threat intelligence consumers within the surveyed organizations.
The relative immaturity of cloud security might explain why it’s lagging behind slightly in terms of focus, but this should grow as cloud security becomes more standardized within organizations.
When it comes to use cases, blocking bad IPs (64%), integrating threat intelligence feeds with other security products (63%), and root cause analysis to determine scope (54%) were cited by respondents as the main applications of threat intelligence within their organizations.
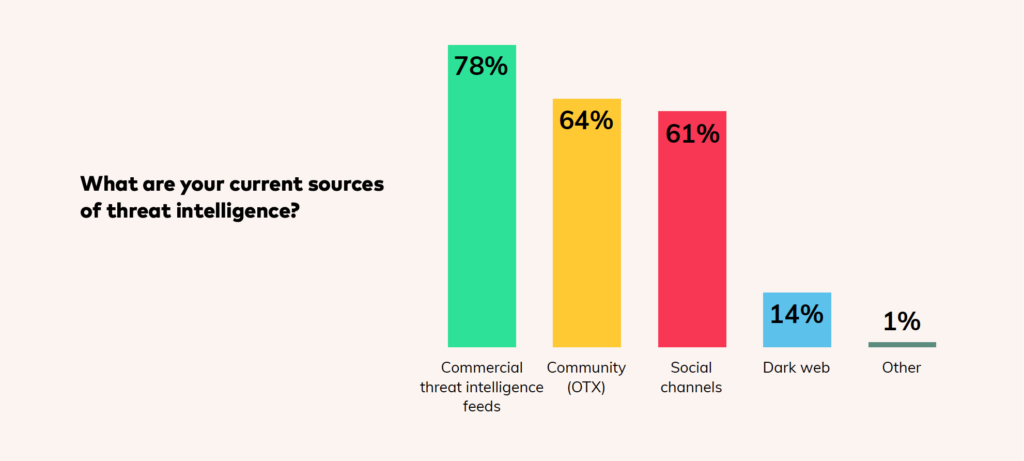
Multiple threat feeds, but a lack of skills
While threat intelligence frameworks are being incorporated more and more into organizations’ security efforts, there remains a lack of the skills needed to leverage the data to the fullest extent. As a result, most respondents are relying on multiple 3rd party threat feeds for their data, including commercial feeds, and community and social channels.
Security teams need to identify any emerging threats and apply them specifically to their organizations. This is challenging, and requires dedicated attention and expertise to parse the data effectively. The reality is that some teams simply do not have the skillset to successfully do this, and the use of multiple feeds may indicate a dependence on external channels to fill in any information/skills gaps that they might be facing.
More automation?
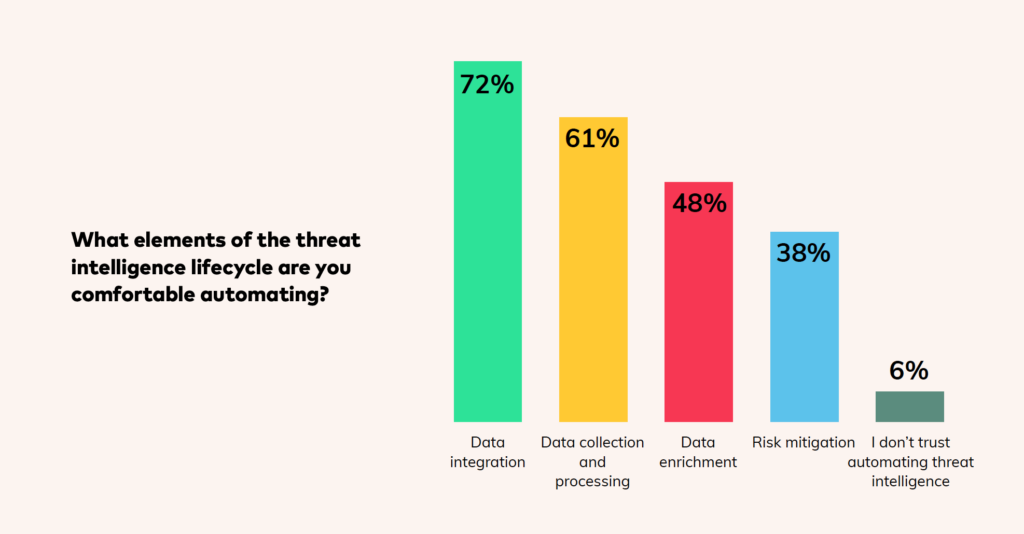
Teams are already automating some elements of threat intelligence, with the vast majority of respondents turning to automation in some capacity.
Only a small number indicated that they are not comfortable automating any part of threat intelligence. Most decision-makers will turn to automation for data integration and processing, but fewer will rely on it for the risk mitigation stages.
Leaving these responsibilities to automation can be a dubious proposition for teams looking to make sure no mistakes are made when it comes to securing environments. Nonetheless, as automation technology grows more sophisticated, we expect people to feel more comfortable depending on it for the crucial aspects of risk mitigation.
The next stages of threat intelligence frameworks
Threat intelligence is increasingly used by IT security teams to help them uncover and prioritize threats to their organizations. But with greater resources and investment in talent, it can be utilized even more. As this technology improves, the only hurdle for security professionals is for them to put their trust in it.
Read more from our survey with Gartner Peer Insights here.