First Officer’s log, Terrestrial date, 20221031. Officer of the Deck reporting.
Leaving Starbase 42, the captain authorized maximum sustainable warp to reach [REDACTED] to pick up Lieutenant [REDACTED] and her team. By the time we arrived, the vendors they had been working with had long since departed for their home worlds, and the local security team had gotten comfortable enough with our solution that they really didn’t need any additional help. The successful deployment is largely attributable to the Lieutenant’s work, but the ongoing success and ease of use are mostly because the equipment she and the team installed worked as intended.
The team was eager to get back to work and, as we set course for Frontier Station [REDACTED] for repositioning and resupply before going to our next assignment, a communication came in from Starfleet Command relaying that the subspace communications system was going to be receiving an update in a few days and we should be prepared to deploy it.
Apparently, the [REDACTED], who designed the subsystem adopted by most worlds in this part of the galaxy for anything short of military-grade communications, and sometimes as part of those too, was sending out an update because they’d discovered a security issue. The update corrected it. But they hadn’t actually released any information on the problem, at least not to people at our pay grade.
The challenge was the chatter we were hearing from people who weren’t sure whether this was a cataclysmic event that would compromise all communications and destroy the federation, or just another break-fix that should be handled like any other.
For us, it was quickly becoming a matter of being able to fulfill our role as a support ship. We knew just as little as anyone else. It was fairly certain that historical adversaries like the [REDACTED] and [REDACTED] would try and identify and exploit the issue before the update was disseminated across the subspace communication network, but from what anyone knew that hadn’t happened. Yet.
Whether it did or not was, at this point, irrelevant. What mattered was being able to help affected worlds get the fix in place when it arrived and keep people from panicking based on what might happen, rather than what was.
Would it get messy?
Maybe.
Either way, we would be ready.
Watch out for this typosquatting campaign
What happened
A recently revealed typosquatting campaign involves over 200 domains impersonating almost 30 brands. The campaign is notable for its sheer scale and reach and has been targeting a mix of platforms, though it is largely focused on deploying malicious mobile applications.
Why it matters
Typosquatting is an old-school technique, and, in that, this isn’t anything new. But the scale is unusually large. Several browsers offer some level of protection built-in against typosquatting, and there is a range of 3rd party applications that can help protect users from malicious domains, the fact remains that small mobile screens give the attackers an advantage. Even for those who regularly check the URLs they visit; the limited screen real estate can make it easier to slip a malicious domain past a cursory eye-grep.
In any case, in order to prevent themselves from falling prey to typosquatting campaigns, users should always double-check the source of any application they install. If it’s not from a known and expected source, then don’t install it.
What they said
A typosquatting campaign this large certainly got some heads turning and people talking. Read more.
That makes how many this year?
What happened
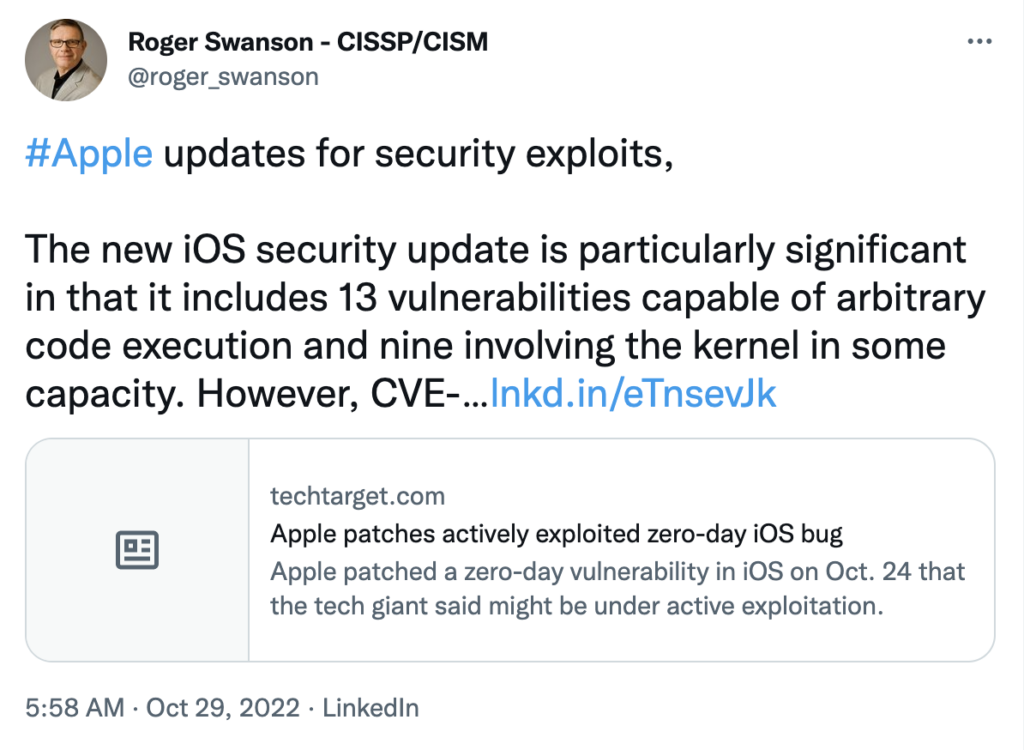
Apple has released security fixes for iOS and iPadOS that addresses multiple security vulnerabilities, including some Zero-Day vulns that could lead to remote code execution on targeted devices. There is evidence that several of the vulnerabilities have been exploited in the wild, though Apple declined to provide more details before the patches were released.
Why it matters
Even well-supported software products can suffer from bugs. While Apple has a reputation for security and privacy, they are still susceptible to buggy code that can lead to an exploit. Fortunately, most Apple products are deployed with automatic updates activated and Apple tends to be quite responsive when it comes to addressing vulnerabilities in their products. Anyone with an affected device should update sooner rather than later, especially if they use it for both their personal and professional needs.
What they said
As always with Apple vulnerabilities, the industry was quick to take note.
Oh look, this belongs to me now.
What happened
A vulnerability in GitHub could let an attacker potentially gain control of existing repositories under specific circumstances. Researchers have said that up to ten thousand existing repos could have been vulnerable. GitHub has subsequently corrected the issue.
Why it matters
There are literally thousands of projects that rely on GitHub repositories, which means taking control of an existing repo could be gold for a threat actor. The RepoJacking vulnerability existed due to the way GitHub handed account renaming, and this newly corrected issue was a new way for attackers to bypass the original fix.
One of the advantages of using repositories like GitHub is they simplify development and allow automatic updates to libraries and such. One of the disadvantages is that users don’t often take the time to verify the code they’re importing hasn’t been tampered with. While it’s rarely an issue with an active code base, projects that aren’t necessarily getting as many eyes on them can fall victim to hijacks like this without anyone noticing until it’s too late.
What they said
With GitHub so important to many, this one had plenty of people talking.
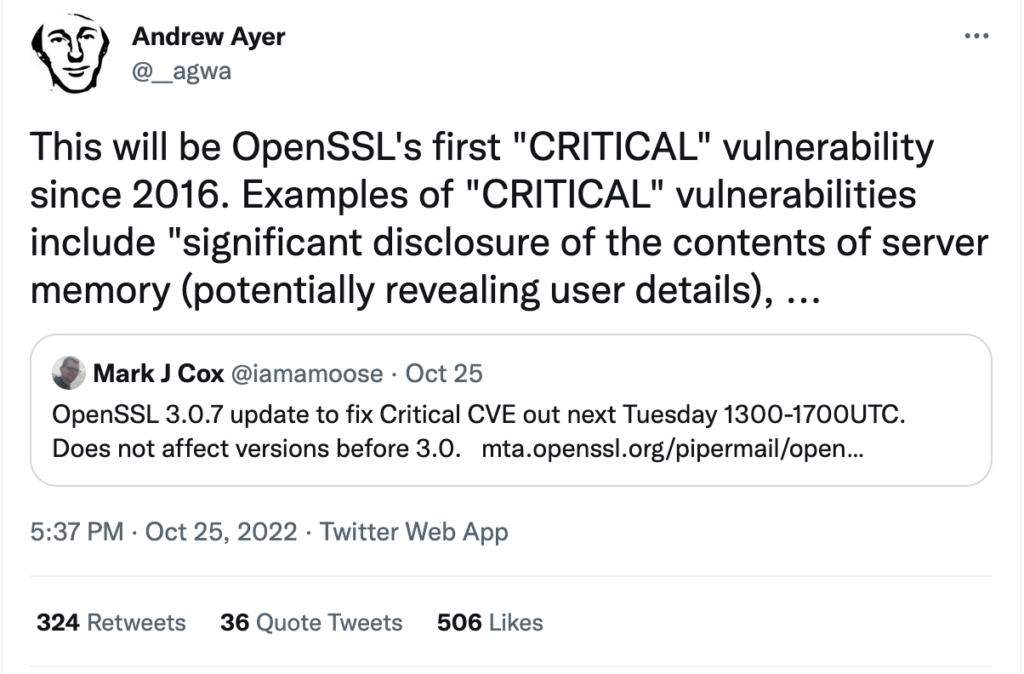
The fix will be here on Tuesday.
What happened
The OpenSSL project has announced the release of version 3.0.7 on 1 November 2022. The release will correct an unspecified “Critical” level vulnerability in OpenSSL 3. Users are advised to update to the new version as soon as practical.
As of this writing, there are no details on the vulnerability or any indication that it has been exploited in the wild.
Why it matters
OpenSSL is used widely across the internet, so anything that could compromise its security and integrity is a Bad Thing™ and needs to be dealt with quickly. Here, they’ve only stated that a problem exists without giving any details. Security professionals may wish we knew more, but by being vague they are making it more difficult for potential attackers to identify and exploit the issue before the new version drops on the 1st.
The catchphrase from a certain travel guide comes to mind here. Namely: Don’t Panic.
But do be ready to upgrade when the upgrade is available. With OpenSSL being part of a lot of other products, it could be a very busy patch cycle.
What they said
This one got plenty of attention.
Aside from press coverage, we also detailed everything we know so far. We’ll update this post as the information comes in – stay tuned.
Diving deeper, I explored the patch and what we know of the vulnerability in my latest video:
___________________________________________________________________________________________________________________________
Want to get ahead of the stories? Join the conversations as they happen with the Vulcan Cyber community Slack channel