This post provides all the information you need to ensure that your organization does not fall victim to one of the most devastating vulnerabilities to emerge in recent years: The Microsoft Exchange Server remote code execution vulnerability. This has been one of the most popular searches on Remedy Cloud in March and April 2021 due to the vast number of organizations potentially affected and the devastating impact it has already had.
To find out about vulnerabilities affecting you and get quick solutions that you can implement right away to keep your organization safe, Vulcan Remedy Cloud is here for you, offering the largest database of remedies and fixes for today’s most searched vulnerabilities.
Read on to discover whether your organization is at risk due to the Microsoft Exchange Server remote code execution vulnerability, how to respond, and how to avoid future exploits.
What is the Microsoft Exchange Server remote code execution vulnerability?
When a remote code execution (RCE) vulnerability is exploited, malicious intruders gain access to your organization’s servers without valid credentials. This gives them the ability to perform any number of unauthorized and malicious actions.
Hackers exploiting the Microsoft Exchange Server remote code execution vulnerability can penetrate your mail servers, gaining access to potentially sensitive internal and user data. They can then profit either by selling any data with commercial value—like personally identifying information (PII) or intellectual property (IP)—or use it against your organization to demand ransom.
The Microsoft Exchange Server remote code execution vulnerability actually includes numerous common vulnerabilities and exposures (CVEs):
Does the Microsoft Exchange Server remote code execution vulnerability apply to me?
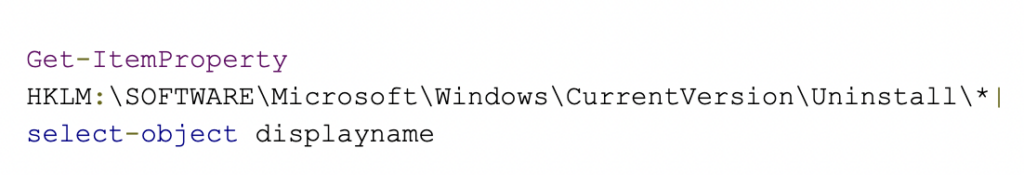
If your organization is using Microsoft Exchange Servers 2013, 2016, and 2019, then these vulnerabilities potentially apply to you. To determine the version number that your organization is currently running, as well as its patch status, follow these instructions, provided by Microsoft.
Alternatively, from the PowerShell, run the following:
Has the vulnerability been actively exploited in the wild?
Yes, Exchange (email) servers of at least 30,000 U.S. organizations and hundreds of thousands worldwide had been attacked through these vulnerabilities. Many attacks are attributed to HAFNIUM, a state-sponsored group operating out of China.
While initial HAFNIUM attacks, beginning in January 2021, were closely targeted, the group later took on a more scattershot methodology, indiscriminately attacking Exchange Servers found on scans.
Since mid-March 2021, this vulnerability has also been connected with the DearCry/DoejoCrypt ransomware attacks. Attacks encrypt information on the server’s hard drive and leave contact information to send the ransom payment.
The DearCry ransomware emerged after a proof-of-concept for the original exploit was posted to GitHub (which itself is owned by Microsoft), in violation of GitHub policies. It was later removed, but potentially available to malware actors during that time.
How do I remediate the Microsoft Exchange Server remote code execution vulnerability?
There are multiple approaches to remediate this vulnerability, but the first is the one recommended by Microsoft and will provide the highest degree of security.
Recommended method:
This approach will completely protect your organization against this RCE attack:
- Deploy cumulative updates to all affected Exchange Servers. This is Microsoft’s top-priority recommendation.
- Investigate for exploitation or indicators of persistence—Microsoft has created a script to check for HAFNIUM indicators of compromise (IOCs).
- Remediate any identified exploitation or persistence and analyze your environment for signs of lateral movement or additional compromise.
Secondary method (not recommended):
If affected Exchange servers can’t be updated immediately, Microsoft has released mitigation instructions. However, these are not a substitute for a full update. Mitigations provided by the MSRC site include:
- Implement an IIS Re-Write Rule to filter malicious https requests
- Disable Unified Messaging (UM)
- Disable Exchange Control Panel (ECP) VDir
- Disable Offline Address Book (OAB) VDir
Small-to-Medium-Sized Business/Single Install method (not recommended):
Microsoft has also issued a one-click mitigation and remediation tool for small- and medium-sized businesses which can’t yet implement the recommended solution.
Keep up with emerging vulnerabilities. Get free access to thousands of vulnerabilities and get fix done with Remedy Cloud.