-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
Move beyond the limitations of siloed tools. Discover how Vulcan Cyber unifies and enhances your security ecosystem, providing holistic visibility, risk-based prioritization, and end-to-end remediation orchestration across all environments to deliver measurable risk reduction.
Combine your existing security scanners with Vulcan Cyber for a unified and holistic approach to exposure management.
Traditional Scanners

Elevate your vulnerability management strategy by transitioning from cloud-specific CSPM to the Vulcan Cyber full exposure management platform.
CSPM

Elevate your vulnerability management strategy by transitioning from application-specific ASPM to the Vulcan Cyber full exposure management platform.
ASPM

Establish an efficient cybersecurity program by transitioning from asset-focused CAASM to the Vulcan Cyber full exposure management platform.
CAASM

Developing an internal exposure management tool offers customization but requires significant resources. Vulcan Cyber provides immediate ROI with the flexibility to adapt to your unique needs.
Build your own

Traditional Scanners

CSPM

ASPM

CAASM

Build your own

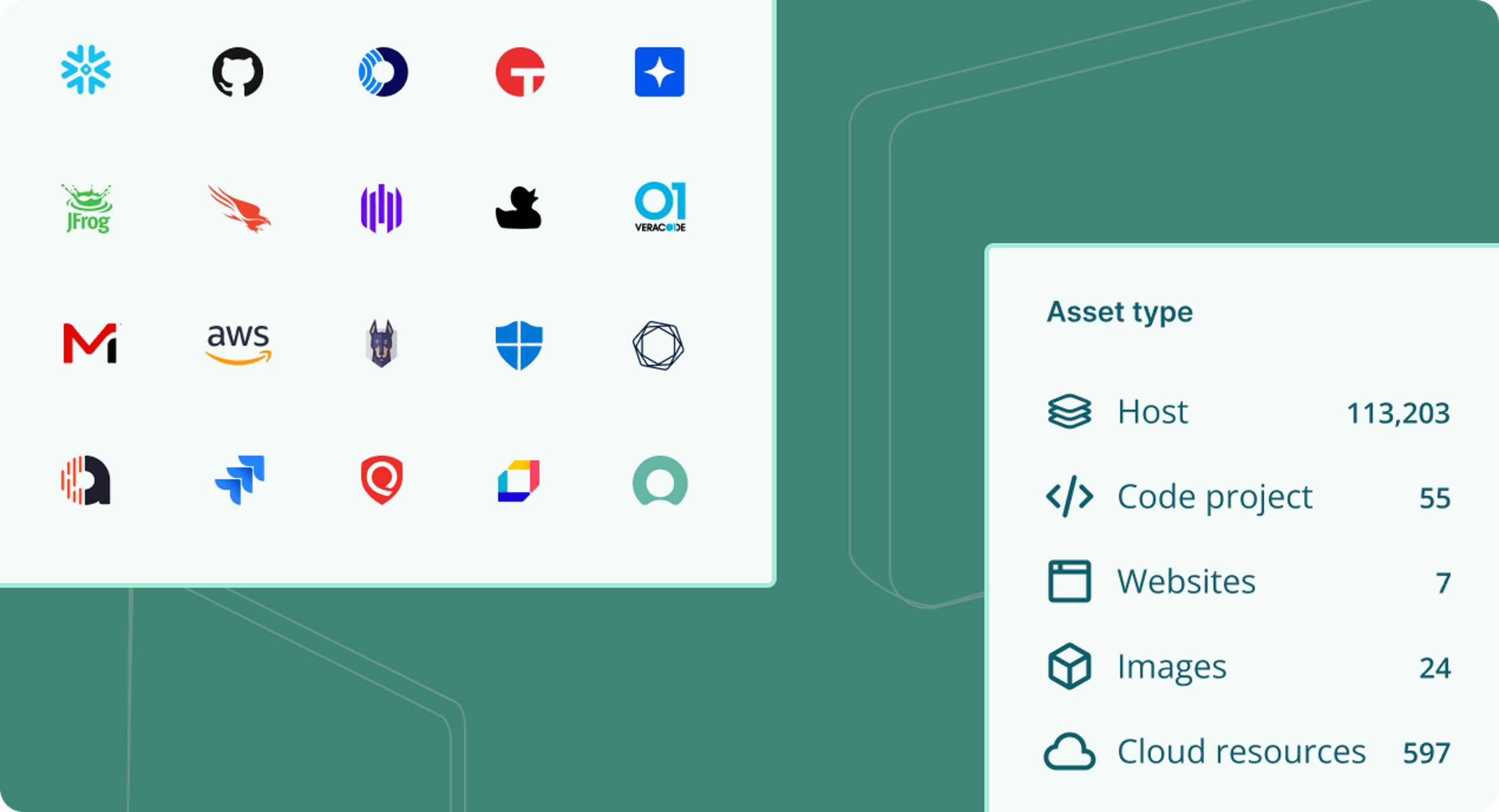
Gain a comprehensive view of vulnerabilities and assets across all environments. The Vulcan Cyber ExposureOS consolidates scanner data, deduplicates, correlates and normalizes it, providing a unified understanding of your organization’s risk landscape.
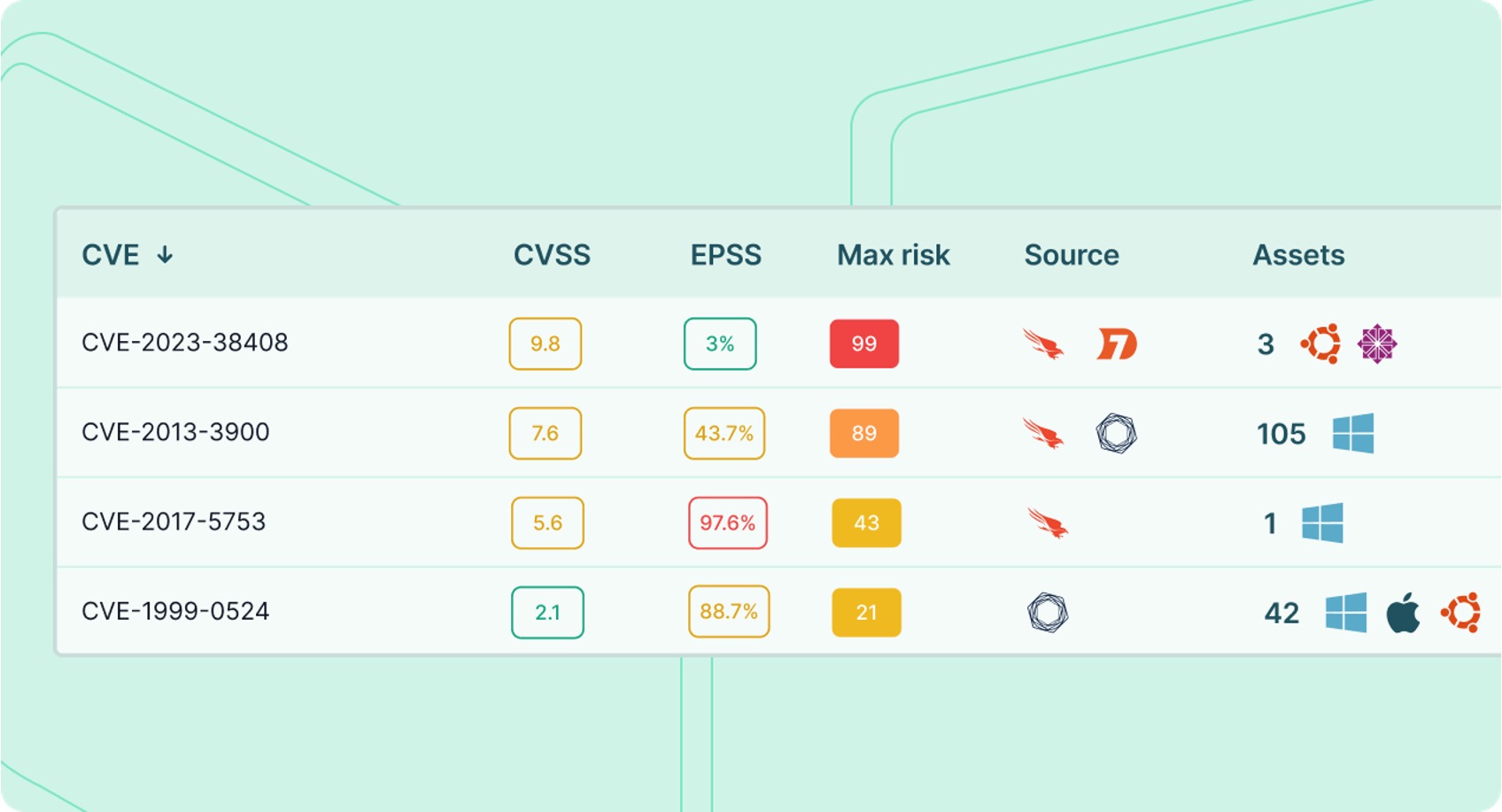
As organizations and technologies scale, vulnerability management must scale accordingly. Vulcan Cyber helps you build and automate remediation workflows to help security teams maintain efficient mitigation of cyber risk, while keeping their most critical assets safe.
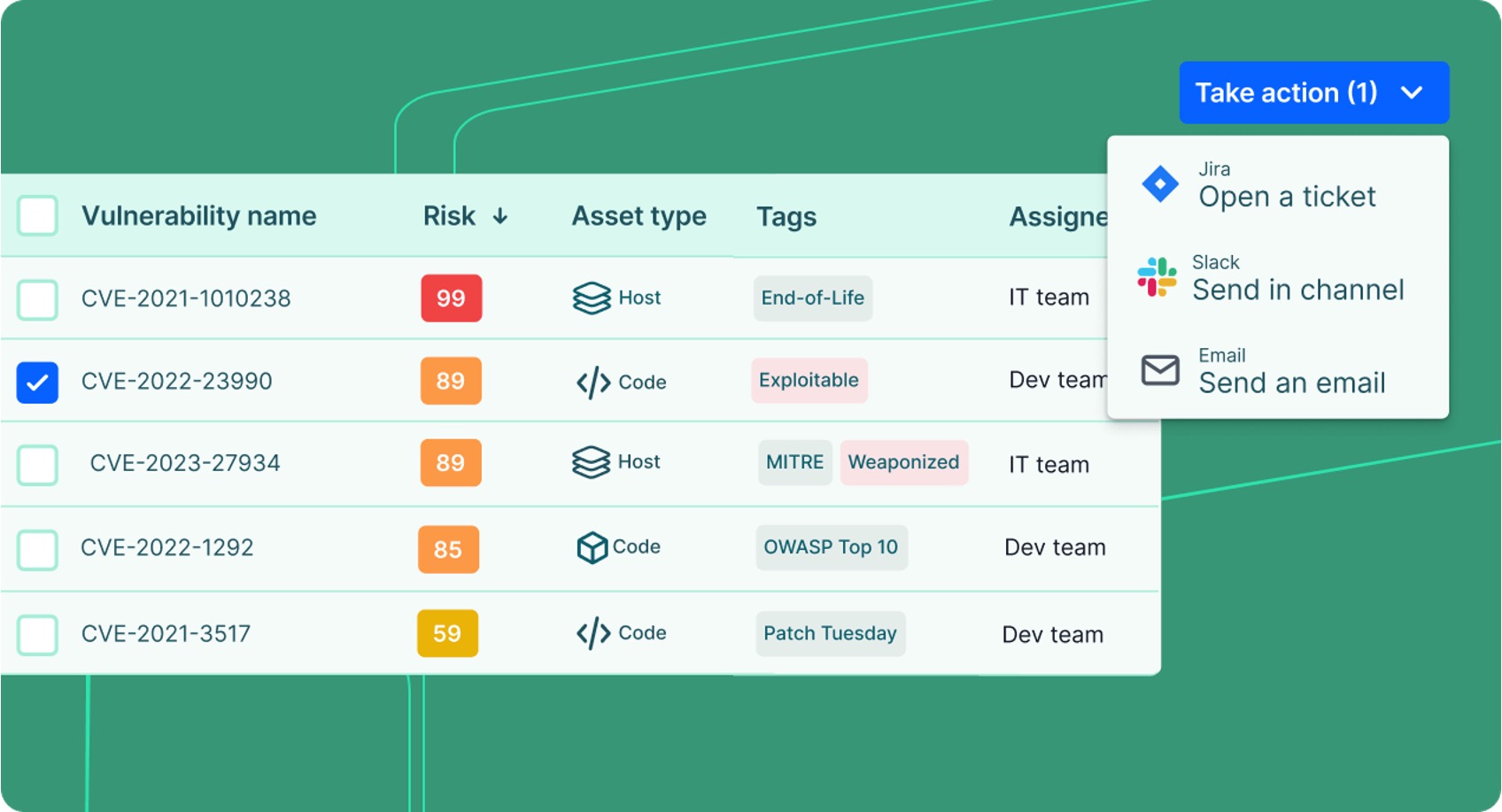
Close the loop from detection to resolution. The Vulcan Cyber ExposureOS empowers security teams with end-to-end remediation orchestration, supported by actionable, AI-driven insights, and seamless integrations into existing messaging and ITSM tools.
 Test you exposure risk management maturity
Test you exposure risk management maturity  Is it time for an exposure management platform?
Is it time for an exposure management platform? 
Set up in minutes to aggregate and prioritize cyber risk across all your assets
and attack vectors.