Executive summary
Efficient risk-based vulnerability management is still the best defense against cyber threats at scale. Most cyber security organizations know this and invest time, money and resources in an attempt to keep up with the proliferation of vulnerability risk. Yet these investments are often misguided, unnecessarily costly and ultimately don’t reduce meaningful risk to the business.
Organizations spend hundreds of hours per week on manual vulnerability management tasks. This takes into account the time spent on vulnerability detection and mitigation, together with documentation, reporting, and coordination across teams—resulting in millions of dollars in direct costs.
Yet risk mitigation efforts are less efficient and effective than they could be due to:
- Attack surface complexity: Today’s IT environments are increasingly complex with threat actors actively exploiting diverse attack paths. From cloud to endpoint and everything in between, the risk profile of all digital assets and their dependencies needs to be mapped and managed.
- Tedious, time-consuming tasks: Many organizations still don’t automate the thousands of daily tasks associated with vulnerability prioritization and remediation. These processes are tedious, time-consuming, and get in the way of risk mitigation.
- Conflicting mandates: Security teams defend and protect while operations teams work to deliver business productivity and availability. The tension between these goals creates inevitable conflict, which can hinder efficient cyber risk mitigation.
- Disjointed workflows: Siloed security, operations and development teams struggle to coordinate risk-based vulnerability management efforts, leading to delays and inefficiencies in risk reduction. Protracted attack windows is a gift to the threat actor looking for systems with known, unaddressed vulnerabilities.
- Constrained resources: In fast-moving digital environments, businesses often lack the resources (e.g., staff and budget) to effectively keep up with a never-ending crush of vulnerabilities. And with the number of vulnerabilities increasing rapidly each year, chronically understaffed security departments must become more strategic and focus on the vulnerabilities that pose the most risk to the organization.
By identifying and addressing these common points of friction, which all serve to undermine vulnerability mitigation efforts, organizations can streamline their risk-based vulnerability management processes, reduce costs, and strengthen their overall security posture.
Today’s threat landscape is evolving rapidly, with a nearly 100% rise in state-sponsored cyber attacks between 2019 and 2022. The nature of the threat is changing as well; more attacks are being carried out with the goal of data destruction and financial theft. Cyber crime is also being professionalized, with many threat actors providing ransomware-as-a- service products aimed at making attacks easier and more lucrative than ever.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) reported that “we must introduce greater automation into risk-based vulnerability management.” And in its Cost of a Data Breach Report 2023, IBM reported that “organizations with fully deployed security AI and automation” were able to reduce the cost of a data breach to around $3.6m.
The hidden costs of ineffective risk-based vulnerability management (RBVM)
It’s clear the stakes are high. Cybersecurity Ventures3 anticipates that the global cost of cybercrime to grow by 15% per year over the next three years, reaching $8 trillion USD globally this year and $10.5 trillion USD annually by 2025, up from $3 trillion USD in 2015.
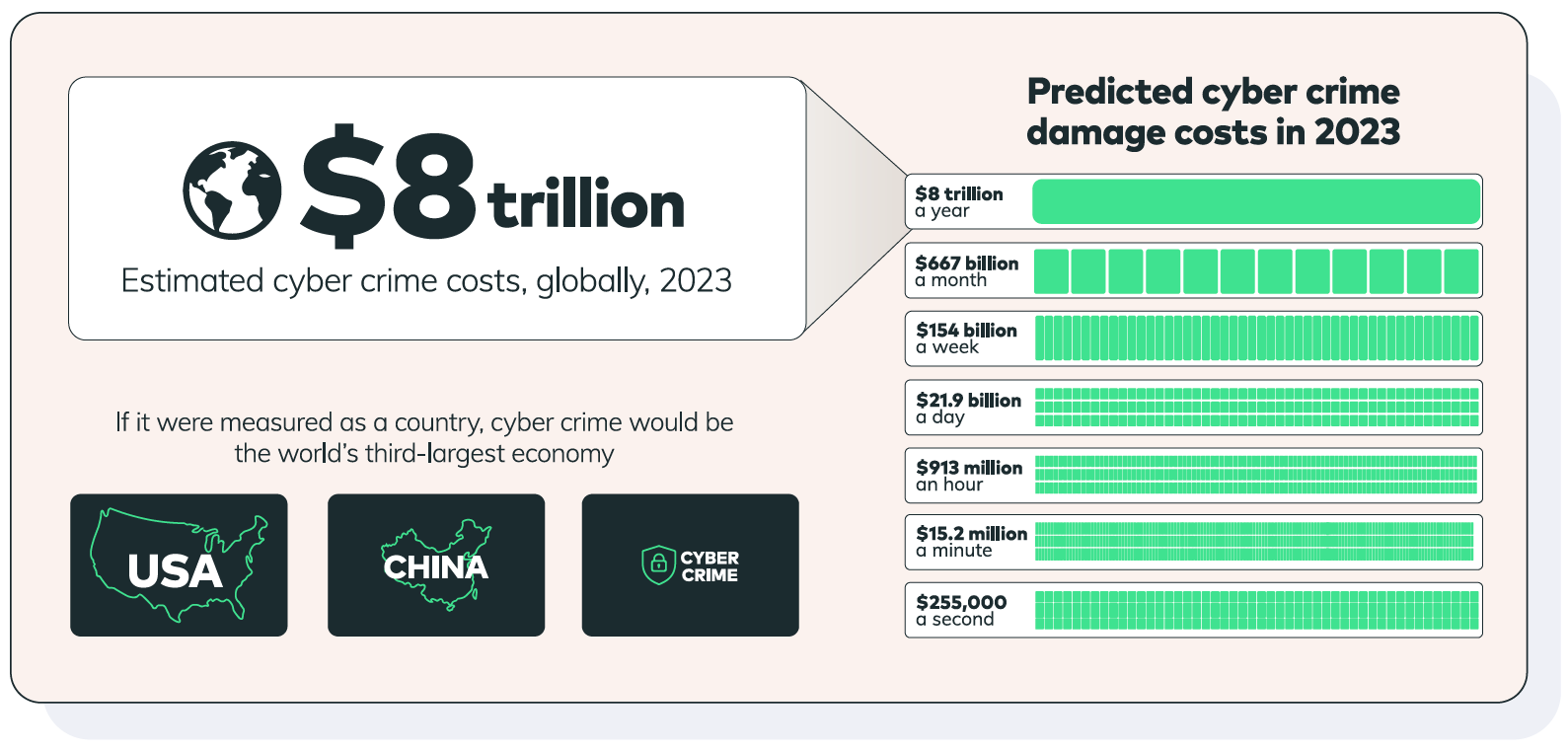
But beyond the direct cost of attacks and the increasing risk that vulnerabilities create for organizations, ineffective and inefficient vulnerability remediation takes a toll in other ways that we’ll reveal in this report.
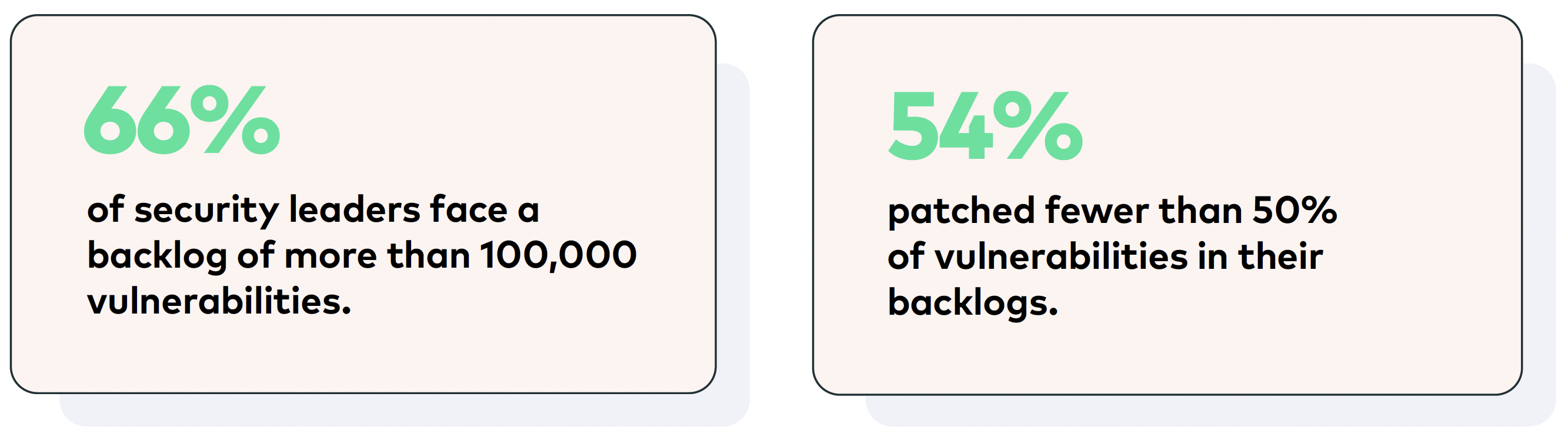
Meanwhile, experts with cyber security insurer Coalition were predicting that the number of vulnerabilities in 2023 would rise by 13% to 1,900 new CVEs per month. The flood of vulnerabilities coming in daily easily overwhelms IT resources. In a Ponemon survey of security leaders, 66% reported a backlog of more than 100,000 vulnerabilities. And 54% reported that they had managed to patch fewer than 50% of vulnerabilities in the backlog.
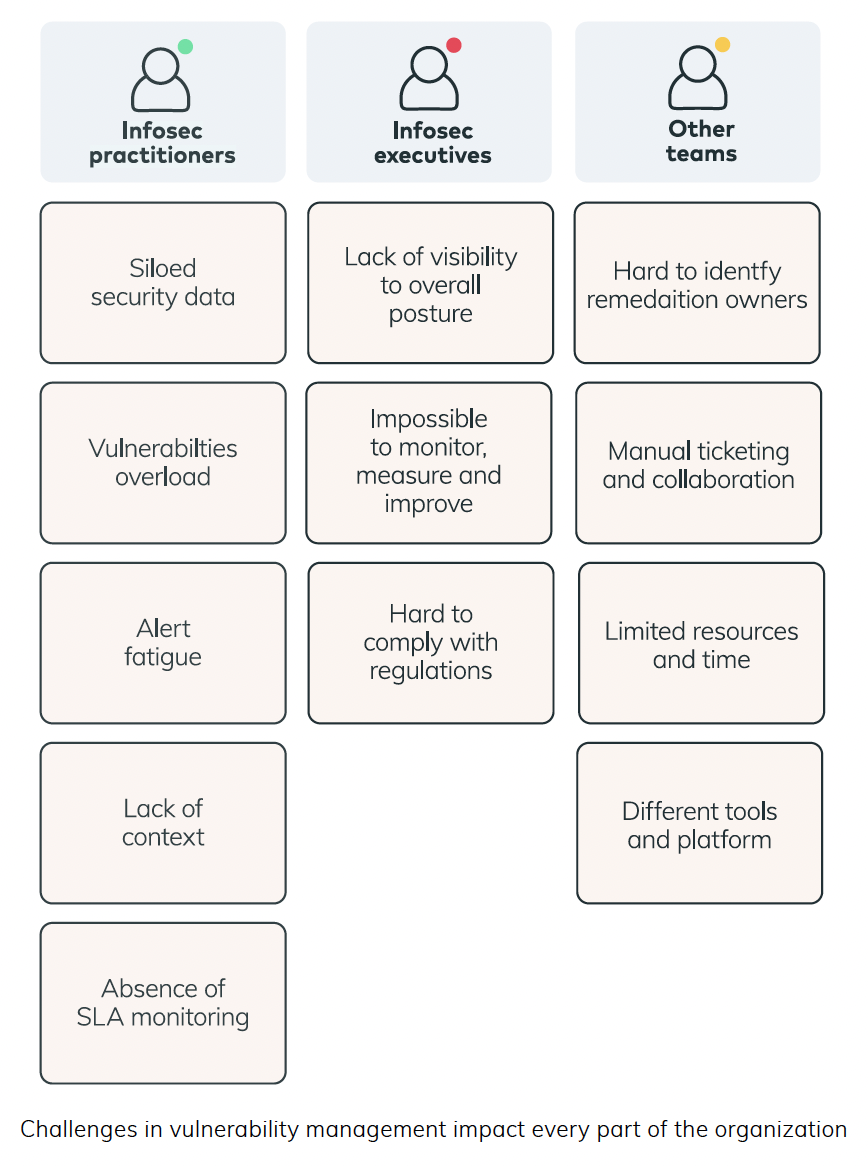
Security teams are drowning in asset and vulnerability risk data—and have too little visibility into the risk that matters to their organization. Deafening risk noise makes finding important signals harder to identify, making vulnerability prioritization with any amount of confidence nearly impossible. In other words, the number of vulnerabilities isn’t the problem. Prioritizing and efficiently mitigating the risk that might actually impact the organization is the problem.
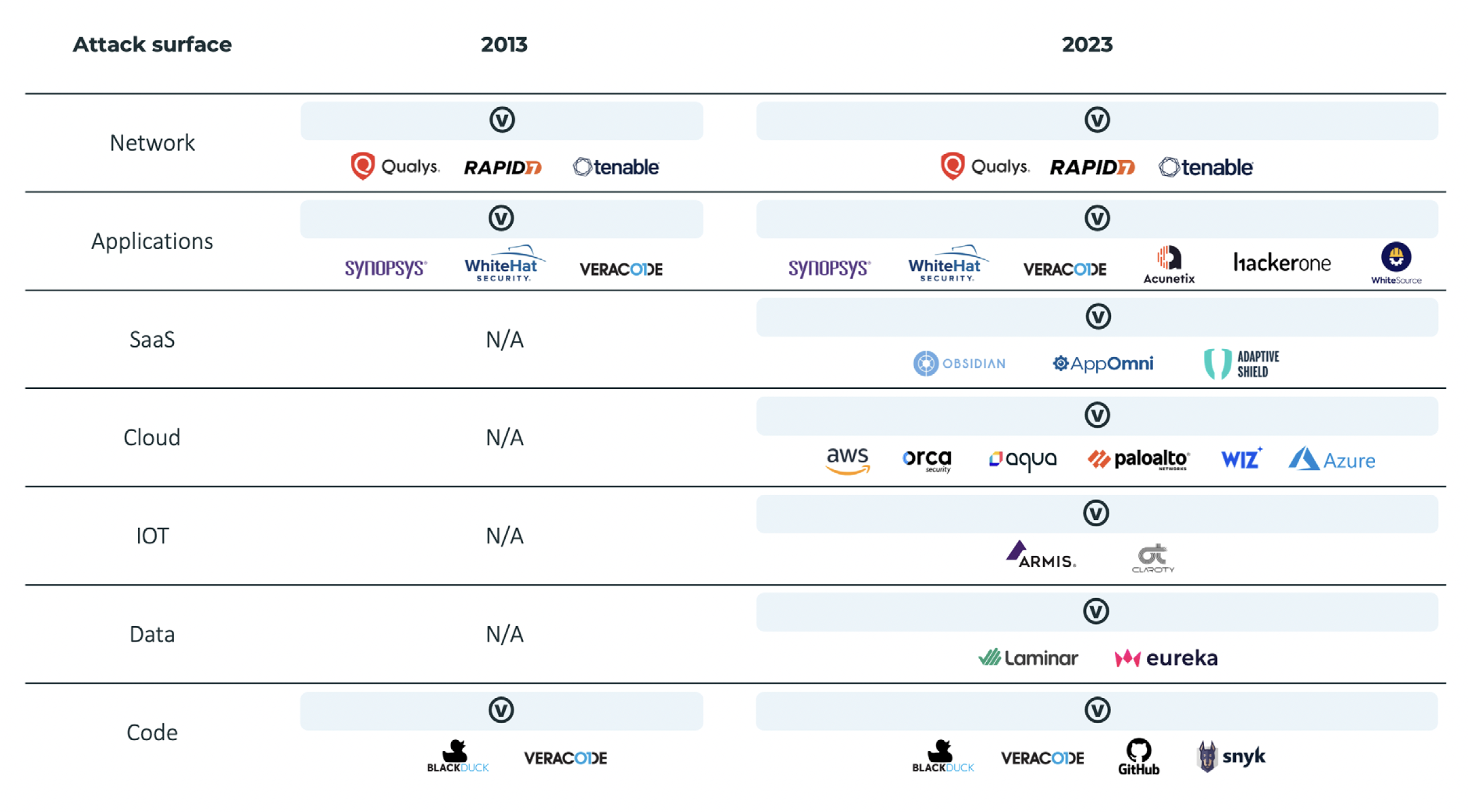
In addition, many existing security tools don’t adapt to the cloud-native environments that are increasingly part of most business workflows. As vulnerabilities spread across different environments and technologies, and become more-and-more intertwined, impactful risk mitigation at scale becomes impossible. With vulnerability management and SecOps teams at a breaking point, something has to give.
Time spent reactively “putting out fires” is time that can’t be spent on proactive security and thoughtful defense, or on IT responsibilities like user support or providing competitive advantage.
The pillars of ROI for risk-based vulnerability management
Based on data from the Vulcan Cyber platform, users save an average of 132,000 hours monthly on vulnerability deduplication, prioritization, orchestration, and reporting. These savings are built on four key pillars of RBVM:
- Prioritization with context: Leveraging robust threat intelligence and contextual analysis, effective RBVM means identifying the vulnerabilities that are uniquely critical to your organization, which should be much less than the generic industry benchmark of 15% of vulnerabilities identified as critical.
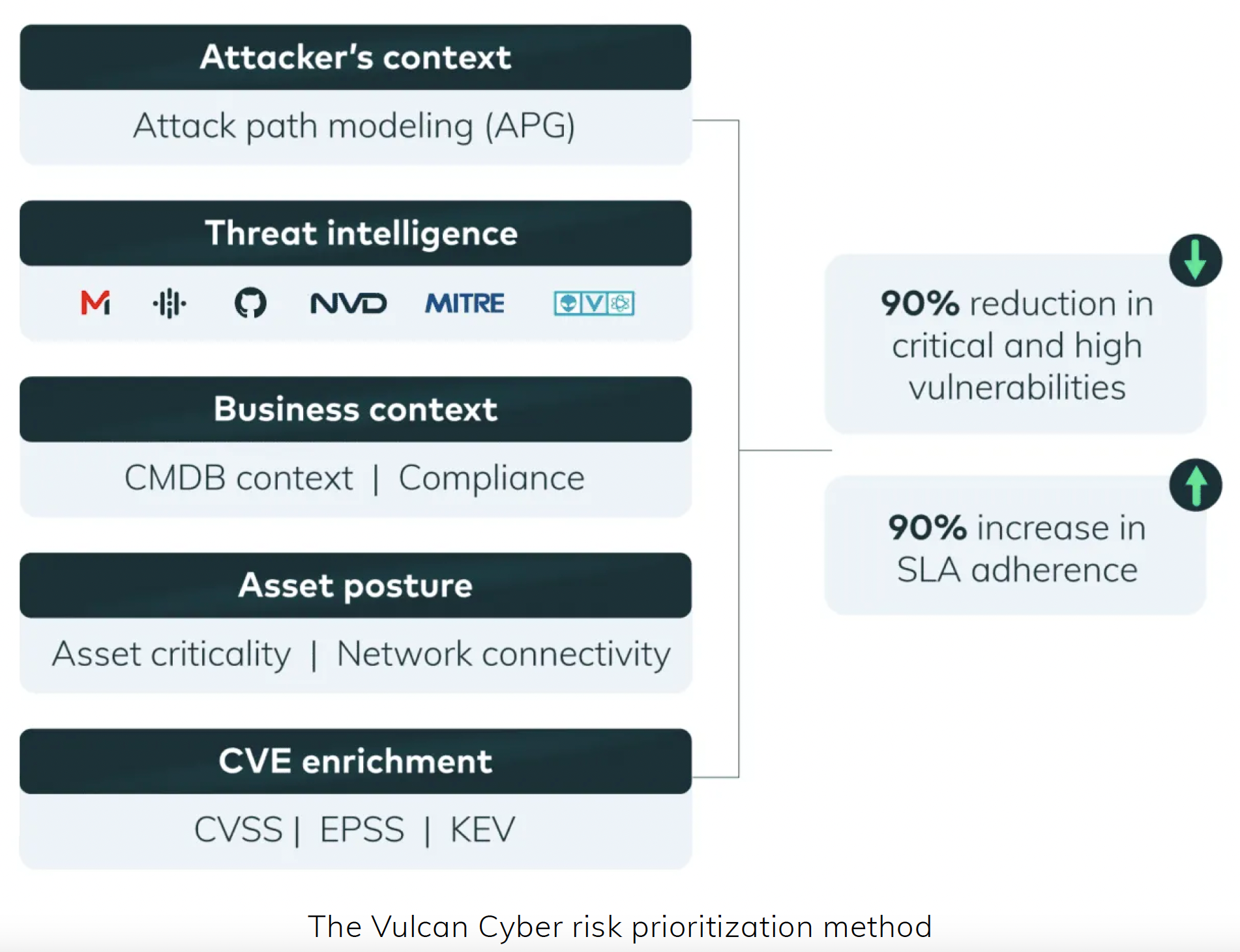
- Reduce the number of vulnerabilities: An RBVM tool should aggregate vulnerabilities from all attack surface scanners (e.g. traditional scanners, SAST, DAST, CSPM etc.), deduplicates them to deliver a single, consolidated view of asset and vulnerability risk posture based on clean and relevant data.
- Efficient, collaborative mitigation: Combining remediation intelligence data, orchestrated processes, and advanced analytics, RBVM must unifiy teams by suggesting the best mitigation approach and measuring the impact of the effort. IT security teams can work faster and more effectively to stay ahead of security windows and save time for other initiatives.
- Automated remediation tasks: Cut time to risk mitigation by up to 90% and improve cross-team collaboration with the Vulcan Cyber automated remediation playbooks and campaigns.
Methodology
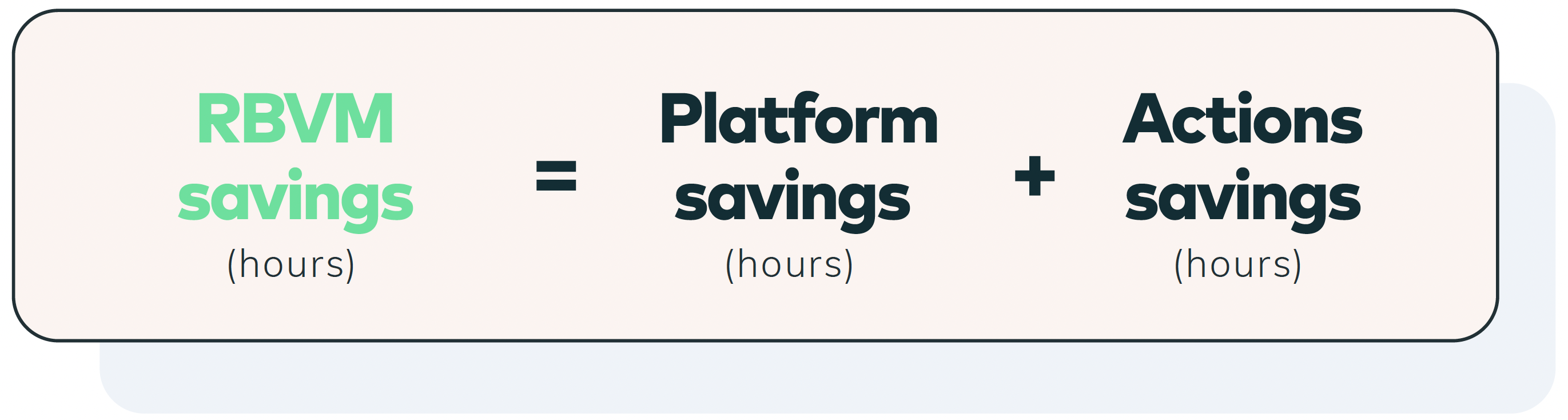
When utilizing a risk-based vulnerability management platform like Vulcan Cyber, the overall return on investment to an organization is a critical metric indicating the amount of person-hours saved. RBVM savings are calculated by the Vulcan Cyber platform based on two main components: Platform savings and Actions savings.
The RBVM savings formula
- RBVM savings
RBVM savings are derived by adding the platform savings and the Actions savings which represent the total person-hours saved by the organization through effective and efficient risk-based vulnerability management.
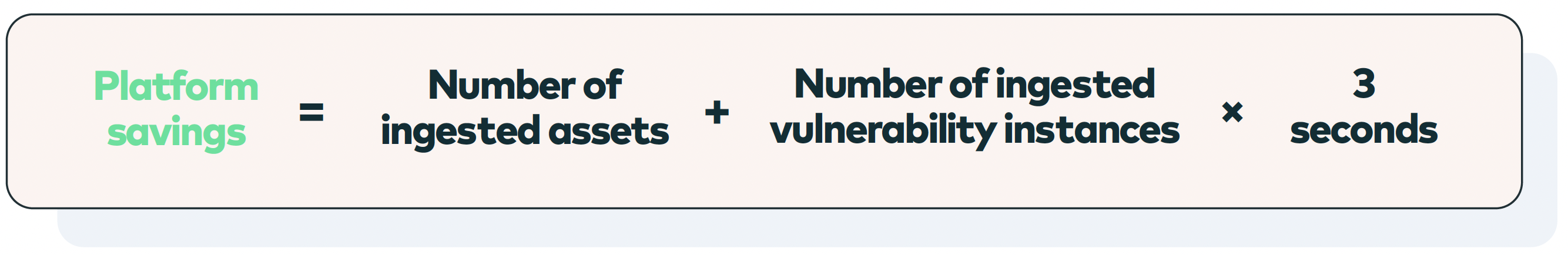
- Platform savings
Calculated at the beginning of each month, this metric evaluates how many hours a single person would have needed to manually gather, de-duplicate and validate all the vulnerability risk data retrieved from multiple, often dozens, of scanners. The data units comprise ingested assets and ingested vulnerability instances.
What RBVM ROI looks like in practice (case study)
When you’re able to focus exclusively on the highest-priority risks for your organization, you’ll see a number of immediate benefits, including:
- Reduced critical cyber risk.
- More-efficient teams and time savings.
- Doing more with less, and working smarter, not harder.
A modern, risk-based approach to vulnerability lifecycle management will help:
- Get security and operations teams on the same page.
- More easily Identify and collaborate with asset owners and business stakeholders.
- Build structure and drive alignment around good process to get the most out of your people and tool investments.
- Provide clear visibility into cyber risk posture and mitigation efficacy through holistic analytics and reporting for practitioners to the board.
A return on investment is a byproduct of vulnerability risk management success. It is difficult to demonstrate this success if you don’t have the ability to measure and show it. Make sure to continuously measure, mitigate and repeat, providing visibility to stakeholders along the way.
How Vulcan Cyber helps a travel and insurance company achieve 71% risk reduction while saving time and money
When a travel services and insurance provider with 2,000 endpoints to manage was experiencing a high degree of inefficiency in vulnerability remediation, including monthslong mean time to resolution (MTTR) for critical vulnerabilities, Vulcan Cyber helped them reduce risk and save on costs.
Challenges within the organization
Looking at a typical organization of this size and scope, a Ponemon study found that 78% of security leaders reported that high-risk vulnerabilities in their environment were taking longer than three weeks to patch.
There are many reasons that organizations like this one are failing to address vulnerability remediation effectively:
- Inability to prioritize: An overwhelming number of “urgent” fixes and time wasted fixing the wrong vulnerabilities.
- Lack of effective tools: E.g. outdated tools that don’t efficiently handle vulnerabilities for cloud-based resources.
- Tool fatigue: The burden of managing numerous security tools—which add to complexity, inefficiency, and increased risk.
- Lack of resources: Most security departments strained to the limit.
- Lack of collaboration and communication: IT, DevOps and application teams work in siloes and are often not aligned on security priorities and requirements.
In addition, with multiple teams taking part in vulnerability remediation, there was widespread confusion and disorganization. It was difficult to determine who owned each vulnerability or to track remediation progress. Security team members were burdened with multiple tools and conflicting priorities.
Without clear processes, there was no “buck stops here” point person taking responsibility for remediating any particular vulnerability. And when that happens, vulnerabilities often become “someone else’s problem”—driving up MTTR significantly.
Rolling out a solution
This organization decided to revamp their approach to risk-based vulnerability management. After considering a number of vendor solutions, they quickly realized that Vulcan Cyber would bring them closer to maturity, including the use of automation.
Vulcan Cyber offered this organization immediate savings in a few key areas:
- Focused remediation efforts: Rather than chasing vulnerabilities based on generic CVSS ratings, customized results allowed the organization to focus on the highestpriority vulnerabilities based on their business needs and risk appetite.
- Holistic risk-based vulnerability management: With a single source of truth when it came to managing vulnerabilities across all assets, the organization was able to realize significant time savings and collaboration.
- Automated remediation task assignment: The organization could delegate responsibility based on asset ownership, and track progress with risk-based SLAs and realtime analytics. They were thus able to reduce manual tasks and simplify processes.
Thanks to these efficiencies, this organization managed to achieve a number of concrete benefits within six months:
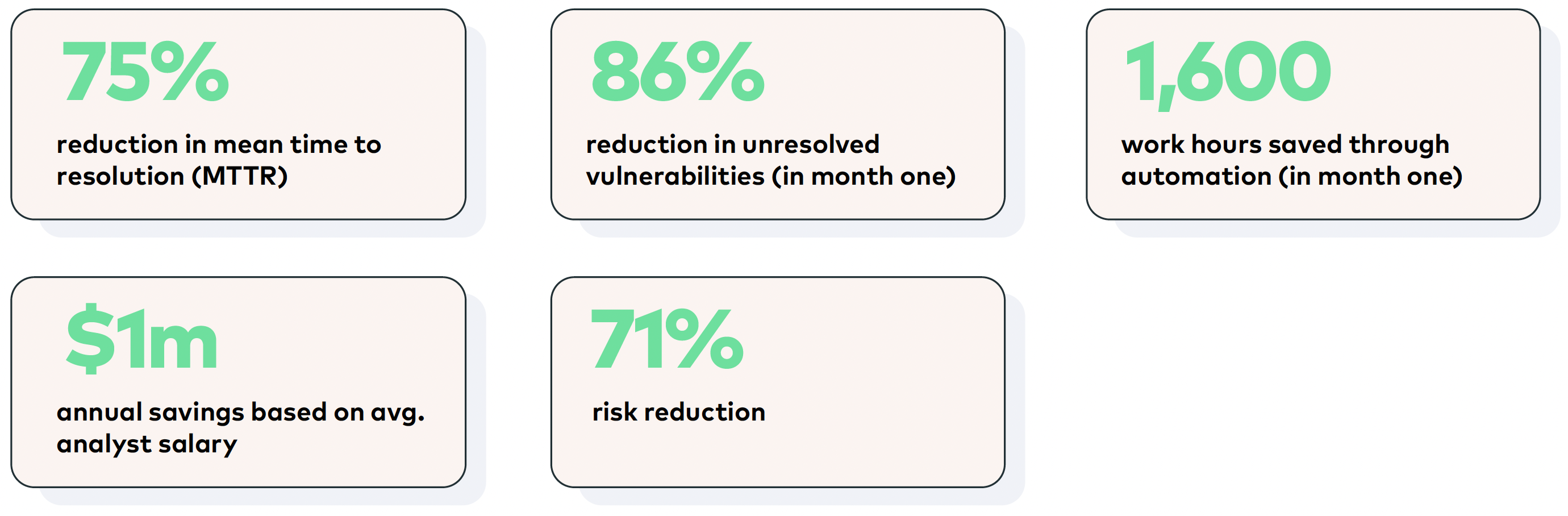
Thanks to these efficiencies, this organization managed to achieve a number of concrete benefits within six months:
#1 Increased operational efficiency
Inefficient vulnerability management costs money.
First, old vulnerabilities leave an organization open to attack for the entire lifetime of the endpoint—including many legacy systems. As many as 76% of vulnerabilities exploited by ransomware in 2022 were actually discovered between 2010 and 2019 and many had patches or workarounds available.
But inefficiencies cost money in other ways as well, including keeping IT and security teams away from other urgent tasks.
No organization has infinite resources; this means every organization—no matter what scale—needs to work as efficiently as possible, prioritizing vulnerabilities based on severity and relevance to the business so they can focus on the most critical issues.
Vulcan Cyber has helped this organization automate vulnerability risk management, immediately saving time and resources, including staff hours for reporting as well as time for remediation:
- Process orchestration and automation took manual tasks off security and IT teams’ shoulders, cutting the vulnerability remediation workload so they could focus on other responsibilities.
- A unified console helps them customize and understand priorities, combining data from CVSS scores, internal asset inventories and CMDBs, and external threat intelligence to offer big-picture insights.
By streamlining vulnerability data, Vulcan Cyber helps this organization zoom in on the ~2% of new vulnerabilities that are absolutely mission-critical and ensure that these are remediated as quickly as possible, leading to an annual savings of $1M per year.
#2 Faster time to remediation
When it comes to resolving vulnerabilities, speed matters. At a time when MTTR can soar into the months—or even 246 days8, as one study reported—every possible source of inefficiency needs to be weeded out, including:
- Multiple teams and handoffs; lack of clear ownership
- Siloed information and data; no single source of truth
- Poor end-to-end visibility and control
Unfortunately, many traditional vulnerability solutions lack the ability to resolve these issues. Many organizations also simply fail to track time to remediation, despite this being a key metric in staying safe from attack.
For this organization, Vulcan Cyber has introduced the following efficiencies to bring down overall MTTR:
Simple integration with existing security and IT tools
- Proprietary remediation intelligence database
- Single-console format provides source of truth
- Predefined playbooks create a faster automated response
- Automatic identification of the remediation owner
- Built-in orchestration, including automated ticket creation within the organization’s existing workflow
With Vulcan Cyber, when a vulnerability is discovered, the organization’s team can quickly pinpoint affected assets and follow steps to achieve effective remediation much faster, leading to an overall improvement in MTTR of 75%.
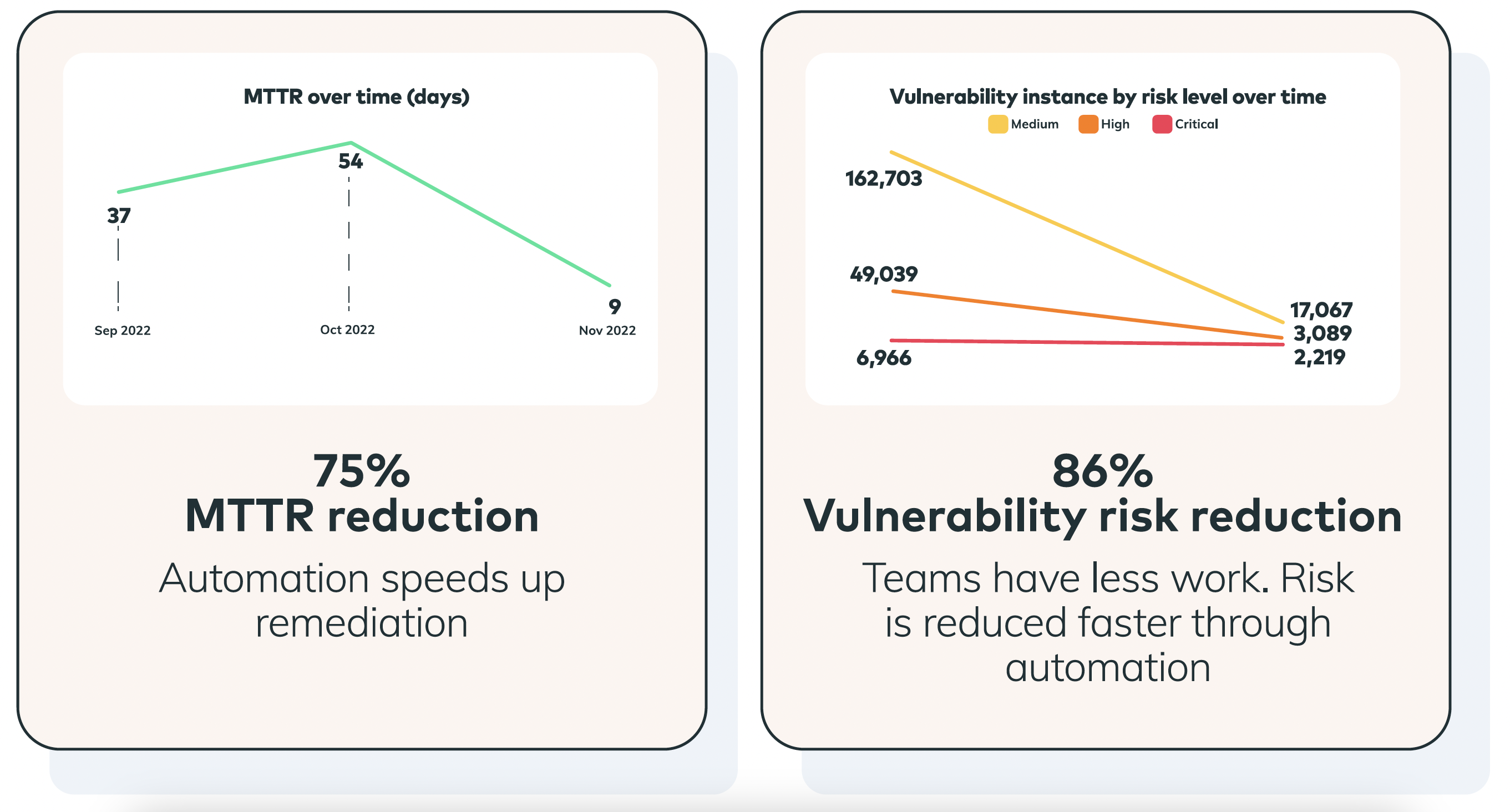
#3 Cutting overall cyber risk
Every organization will probably find itself targeted sooner or later. It’s not a matter of “if” but of “when.” It’s easy to lose sight of the primary goal, but when it comes to risk-based vulnerability management, that goal is clear: reducing the risk of a successful exploit.
In its cost of a data breach report 2023, IBM reported the average total cost of a data breach as $4.45M. And the software supply chain is a growing part of that, with third-party software comprising 13% of the sources of the vulnerabilities that were exploited.
By keeping up with today’s biggest threats and trends in the cyber security world, Vulcan Cyber is able to keep the organization safer from this and other threats:
-
priorities and attack path graph, understaffed remediation teams stay laser-focused on the vulnerabilities that are most critical to the organization.
-
Executives gained visibility into the organization’s cyber risk, allowing better strategy and budgeting when it came to cybersecurity.
Vulcan Cyber helps this organization drive improved processes for asset risk visibility, cyber risk lifecycle management, and administrative controls, leading to a 71% reduction in overall risk.

Efficient RBVM benefits business
Vulcan Cyber has given this organization a powerful platform that provides comprehensive cyber risk management services. With a single view of risk across all assets—including on-premises, cloud, and hybrid environments, along with automated vulnerability remediation and reporting—Vulcan Cyber is used to:
- Reducing risk: Vulcan Cyber risk-based vulnerability management helps organizations prioritize vulnerabilities, reduce MTTR and the risk of security incidents that will harm the business.
- Saving time and money: Vulcan Cyber saves security and operations teams time and money by automating tedious remediation tasks at scale.
- Measure compliance: Vulcan Cyber offers detailed, customizable reports and analytics to ensure real cyber security and compliance with standards like PCI-DSS, HIPAA, and GDPR and many more. Vulcan Cyber integrated reports and risk analytics reduce exposure to regulators and the risk of penalties and costly audit costs.
- Security posture confidence: Vulcan Cyber helps customers understand their unique security posture to direct risk mitigating actions that ensure long-term security posture across the attack surface.
About Vulcan Cyber
Vulcan Cyber enables security teams to effectively manage and reduce vulnerability risk across IT and cloud-native surfaces. The platform consolidates vulnerability scan and threat intelligence data from all attack surfaces and provides asset risk context, recommendations for the best fixes, and automated remediation workflows to streamline tedious mitigation tasks. Our commitment to innovation has earned recognition as a Forrester Wave Leader in the Q3 2023 Vulnerability Risk Management, a 2019 Gartner Cool Vendor and as a 2020 RSA Conference Innovation Sandbox finalist. Prominent security teams, such as those at Mandiant, Deloitte, and Skechers, trust Vulcan Cyber to help them own their risk.