-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
Vulnerability prioritization
Intelligent vulnerability prioritization for application, cloud and infrastructure assets based on the real risk to your organization.






01
When it comes to identifying and analyzing thousands or millions of vulnerabilities and mitigating proactively, too many organizations are still dependent on slow, manual processes.
02
Trying to manage vulnerabilities without understanding your actual risk is a losing battle. Security teams prioritize based on risk ratings that lack the relevant context and business-specific impact to accurately focus on the risk that matters most.
03
Different scanners use different risk scoring models. Without having a common risk score that helps you navigate your next steps of remediation, risk prioritization will forever be inefficient.
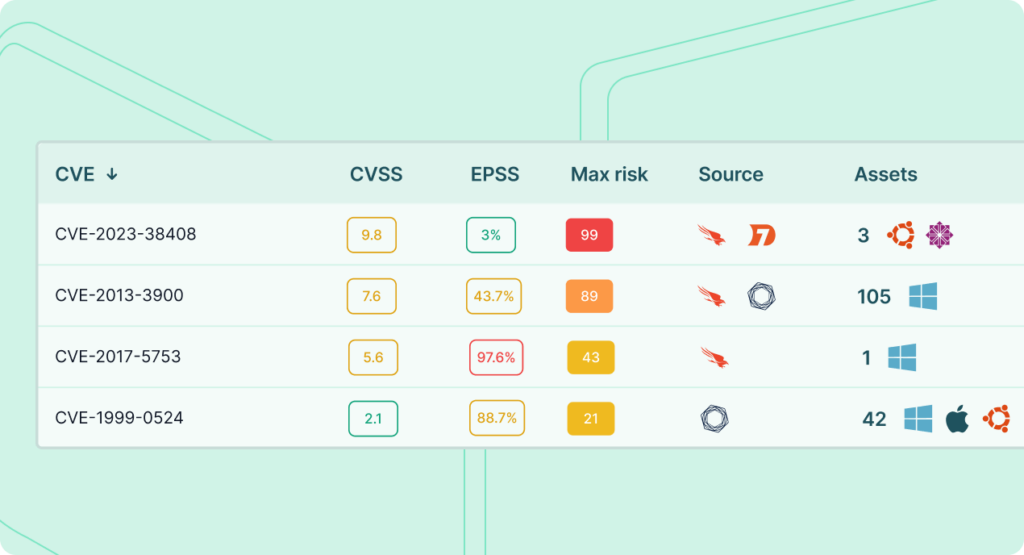
By contextualizing and enriching vulnerabilities with environmental and threat intelligence, the platform surfaces the critical and high vulnerabilities based on actual business risk.
Use attack path modeling to gain a graphical representation of the route threat actors could take across your environment.
Deliver intelligent vulnerability prioritization technology (VPT) that automatically analyzes risk from application, cloud and infrastructure assets and correlates it against extensive organization-specific context, threat intelligence and exploit probability.
Prioritize risk based on customizable logical groups like business unit, network segment, application and/or asset type, compliance requirements or any other grouping relevant to your environment.








you are here
Collaborate
you are here
Report
We use cookies to personalise content and ads, to provide social media features and to analyse our traffic. We also share information about your use of our site with our social media, advertising and analytics partners.
View more