Sequence of events
It began in March 23, when our research team first started investigating the mysterious report of an emerging remote code execution (RCE) vulnerability in a VMware product, without much initial information to go by.
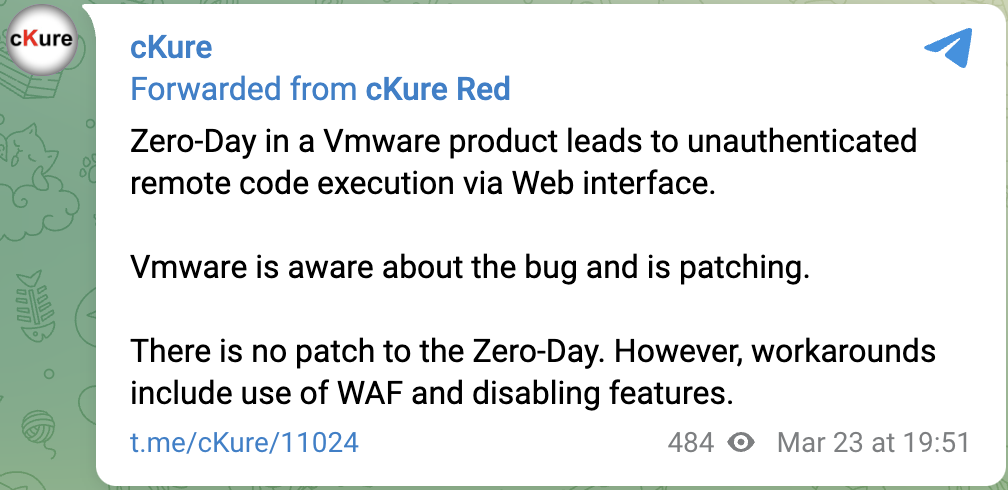
This tweet left us intrigued while the report did not reveal the potential vulnerable component, but did approve that this is in fact a different vulnerability than latest VMWare carbon OS Command Injection vulnerabilities addressed in VMSA-2022-0008 advisory.
Last week, on April 6, VMware announced their VMSA-2022-0011 advisory. The advisory refers to multiple vulnerabilities on various products and aims to address several remote code execution and authentication bypass vulnerabilities. It is here that they first published CVE-2022-22954 which affects Workspace ONE Access and Identity Manager product.
CVE-2022-22954 is categorized by VMWare’s security team as a critical Server-Side template injection vulnerability that could lead to remote code execution by an unauthenticated threat actor.
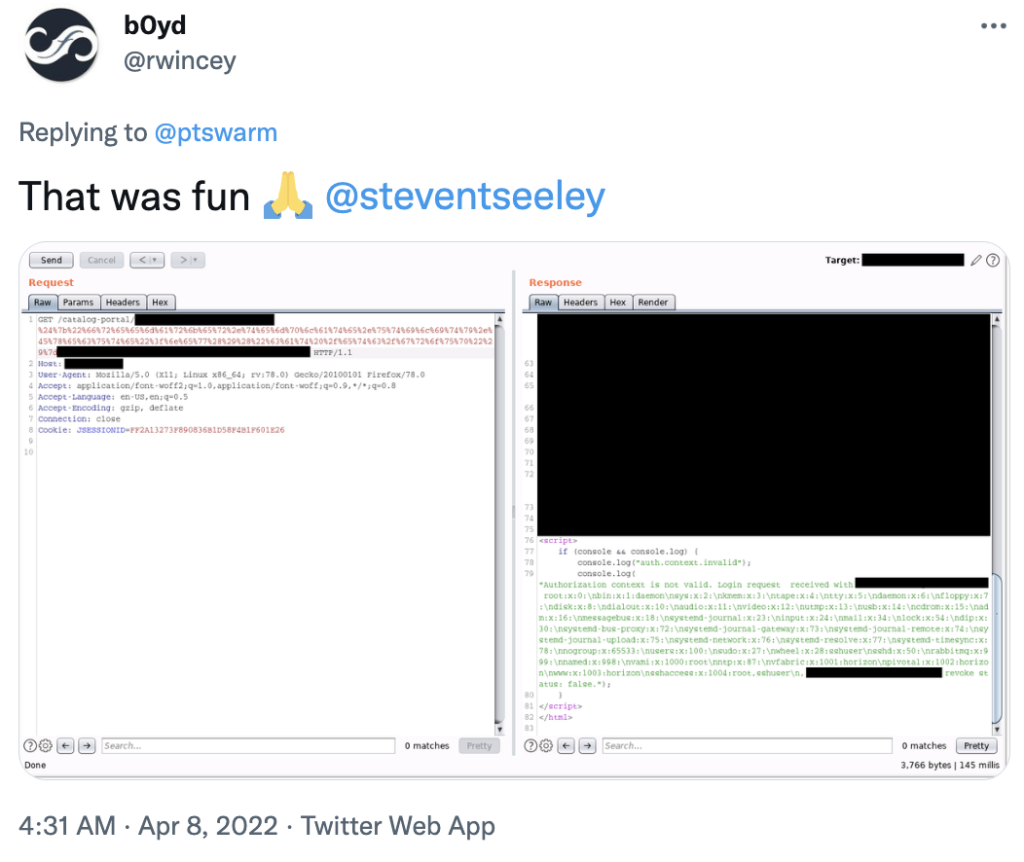
A day after, Positive Technologies’ offensive team claimed that they have succeeded in reproducing CVE-2022-22954 with a censored proof of concept screenshot.
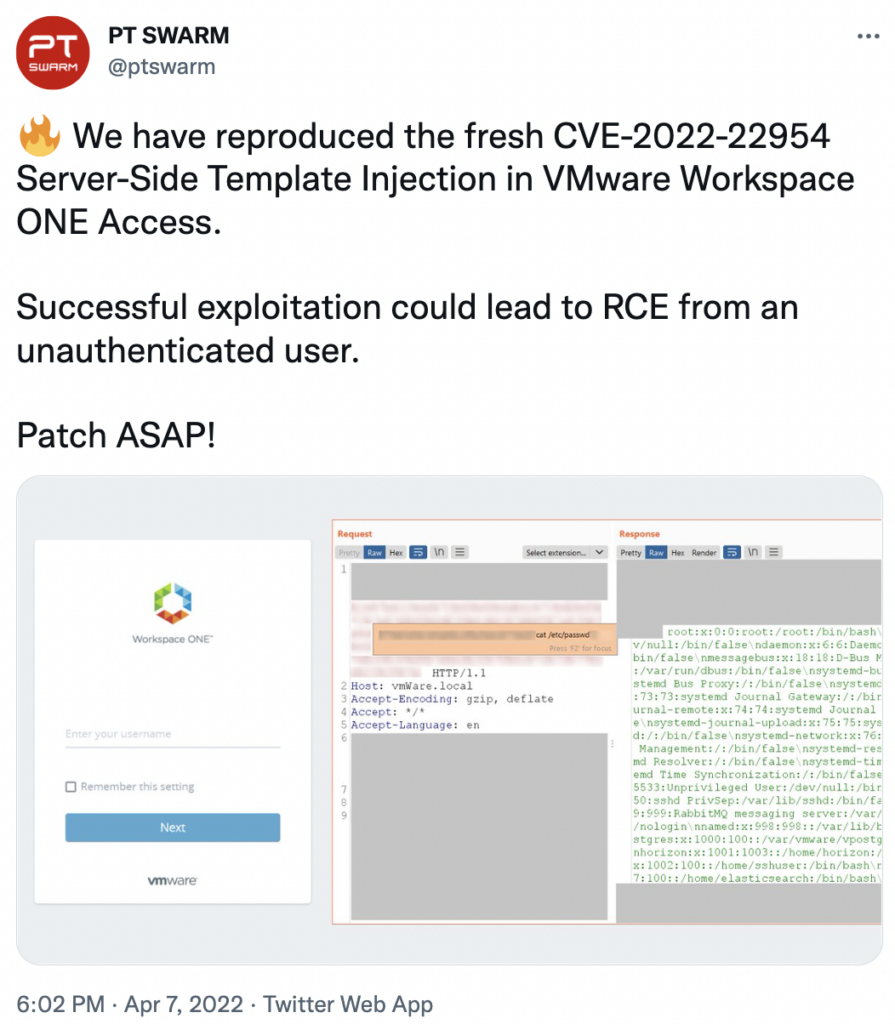
At this time, the CVE was not officially published by NVD, and no Proof-of-Concept was published in the wild so users gained time to easily patch their systems.
Proof-of-Concept in the wild
Yesterday, NVD cleared the fog and published the official CVE reference for CVE-2022-22954 .
The first PoC was also published on GitHub by sherlocksecurity on that same day.
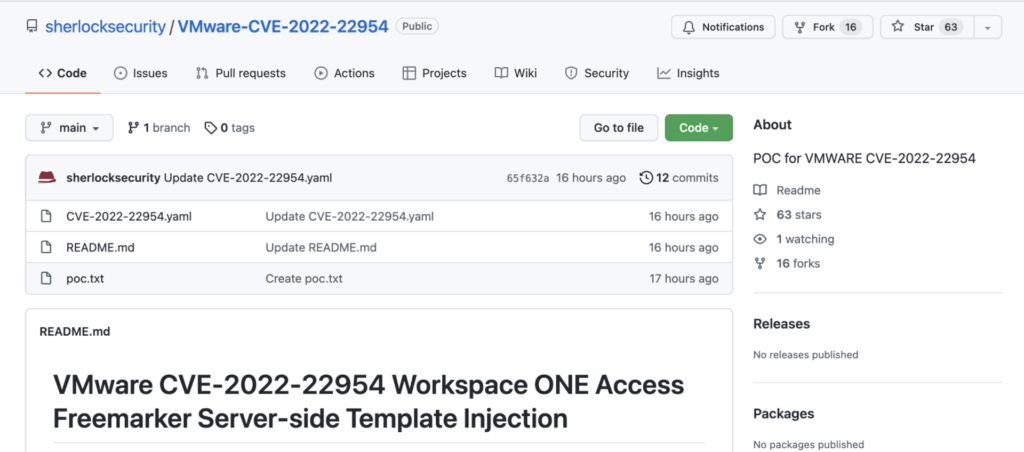
This brings us to the conclusion that there is no more time to wait – if you’re using VMWare Workspace ONE Access in your organization – patch it ASAP!
What is the CVE-2022-22954 vulnerability?
CVE-2022-22954 is a Server-Side template injection vulnerability. This kind of vulnerability arises when user input is directly embedded, in an unsafe manner within a template.
Template engines are commonly used on webservers, and they help developers create static templates with fixed structures, that are rendered at runtime with dynamically changed variables values.
As the PoC header implies, VMWare Workspace ONE uses FreeMarker as a template engine. FreeMarker is a quite common Java-based template engine used in Apache servers.
By decoding the payload in the PoC, we can easily see how the injected payload attempts to instantiate an object of Execute class and run a Linux shell command.
${“freemarker.template.utility.Execute”?new()(“cat /etc/passwd”)}
Does it Affect Me?
If your organization is using Workspace ONE Access, check your deployed version and verify it is not listed as one of the following affected versions:
| VMware Workspace ONE Access Appliance | 21.08.0.1 |
| VMware Workspace ONE Access Appliance | 21.08.0.0 |
| VMware Workspace ONE Access Appliance | 20.10.0.1 |
| VMware Workspace ONE Access Appliance | 20.10.0.0 |
| VMware Identity Manager Appliance | 3.3.6 |
| VMware Identity Manager Appliance | 3.3.5 |
| VMware Identity Manager Appliance | 3.3.4 |
| VMware Identity Manager Appliance | 3.3.3 |
| VMware Realize Automation | 7.6 |
Has it been actively exploited in the wild?
We did not capture any threat report that mentions the vulnerability was exploited in the wild, but now that the PoC is published, we believe it is just a matter of time.
Fixing CVE-2022-22954
Both remediation and workaround instructions were published by VMWare so there’s no need to wait too long to get fixing.
For those of you who can patch their system, patch instructions can be found here.
If patching is not feasible right now, please carefully follow the workaround instructions, that can be found here.
Get ahead of the game with Vulcan Remedy Cloud – the free, comprehensive resource for everything you need to know about how to fix the latest CVEs.
Good Luck!