Silicon Valley Bank (SVB) collapsed on Marth 10th, 2023, less than two weeks before this writing. It’s the second-largest bank collapse in US history, and the worst since the financial crisis of 2007-2008. The repercussions have been felt worldwide, as SVB was widely used across the tech sector internationally. There have already been serious issues with organizations and individuals who lost substantial amounts of money, forcing some smaller businesses to scramble to recover.
While the US government moves to try and prevent further damage, and other financial institutions pick up customers from the collapse, threat actors have already started to move on the new opportunity presented by the financial turmoil. It’s a familiar pattern. An experienced social engineer will always take advantage of a good hook, and this is an exceptionally good hook.
There have already been reports of phishing attempts against SVB customers, with threat actors using multiple variations of “we’re here to help in your time of need” or other stories as their hook. This is a well-known Spear phishing and cast-netting technique. A threat actor sees something directly relevant and timely and uses it as a hook, hoping that the target’s concern about the event will override the common sense they would usually have about a suspicious email.
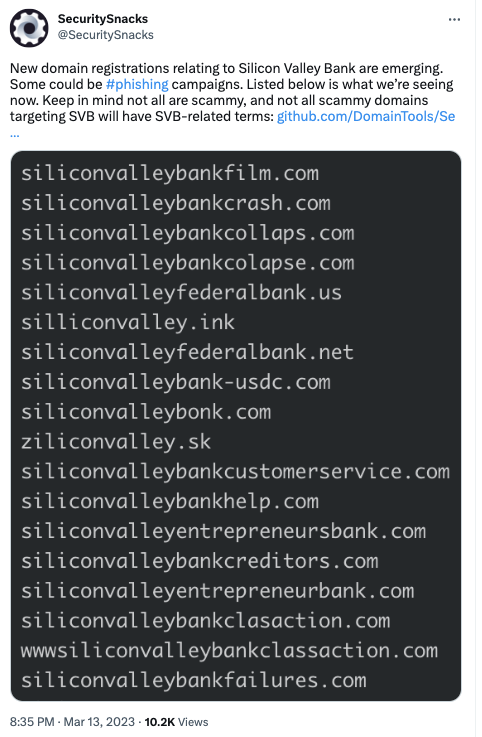
Not surprisingly, multiple domains were registered almost immediately after the announcement of SVB’s collapse that were designed around this very idea. Domains including “collapse,” “bailout,” “claims,” etc., all referencing SVB, appeared almost overnight and were, not surprisingly, associated with threat actors’ attempts to social engineer targets that were affected by the bank’s collapse. If someone falls for the phishing email, the newly minted domain becomes the attacker-controlled landing point for the next stage of the attack.
In a former life as a penetration tester, this is exactly the kind of incident we would look for to use as a hook. At least when we were allowed to use email in the engagement.
None of this should be news, of course. Anyone who’s been in cyber security for even a brief time knows that threat actors never miss a chance to leverage a good crisis – the SVB collapse certainly falls into this category. The question is how organizations will be best able to deal with it.
The biggest risk here comes from social engineering, as it’s easy for the threat actors to make their messages convincing, and the urgency of the situation is likely to make their targets less cautious. That means organizations will need to be especially cautious, especially anyone in departments that would have had dealings with SVB, doubly so if there is legitimate communication on the matter.
Don’t be a phish in the sea
There are some technical steps that can help as well. Existing email filters can be tuned to highlight references to Silicon Valley Bank or any of the likely keywords that would be associated with a social engineering attack. Some commercial filters are doing this already.
Another option is to use a DNS filtering tool that will block, or at least warn about, newly created domains in general and SVB or finance related terms in the domain name. Again, there are commercial tools that are doing this already.
These are just two examples of things organizations can do to improve their security posture against the specific threat created by this incident. Though these are not just specific to this event. They are useful tools to have in place to handle any similar incident, since this, inevitably, will not be the last we see of its kind. While the next may not be a bank collapse, there will be future incidents that serve as the ideal bait for social engineering attacks.
Ultimately, organizations need to stay vigilant and manage their own risk profile. We do have the tools to do it, from the edge inward to the endpoint, but we need to recognize that risk management is a process, and we always need to be ready to adapt to evolving threats.