What is SSVC?
SSVC, a vulnerability prioritization methodology, was introduced to the cyber security market in April 2021 by security researchers at Carnegie Mellon University’s Software Engineering Institute (SEI) and the Cybersecurity and Infrastructure Security Agency (CISA).
The SSVC method was created to help security analysts and vulnerability managers with vulnerability prioritization decision-making.
How does it work?
SSVC is based on the decision tree model. According to this method, every vulnerability eventually “falls” into one of four possible decisions:
- Track
- Track*
- Attend
- Act
It attempts, in a more qualitative way, to classify vulnerabilities based on what the organization needs to do – monitor or remediate. These decisions are based on five values:
1) Exploitation status
2) Technical Impact
3) Automatable
4) Mission prevalence
5) Public wellbeing impact
Using this CISA SSVC Calculator organizations can input decision values and get to the “final decision”. There are 36 funnel decisions in total.
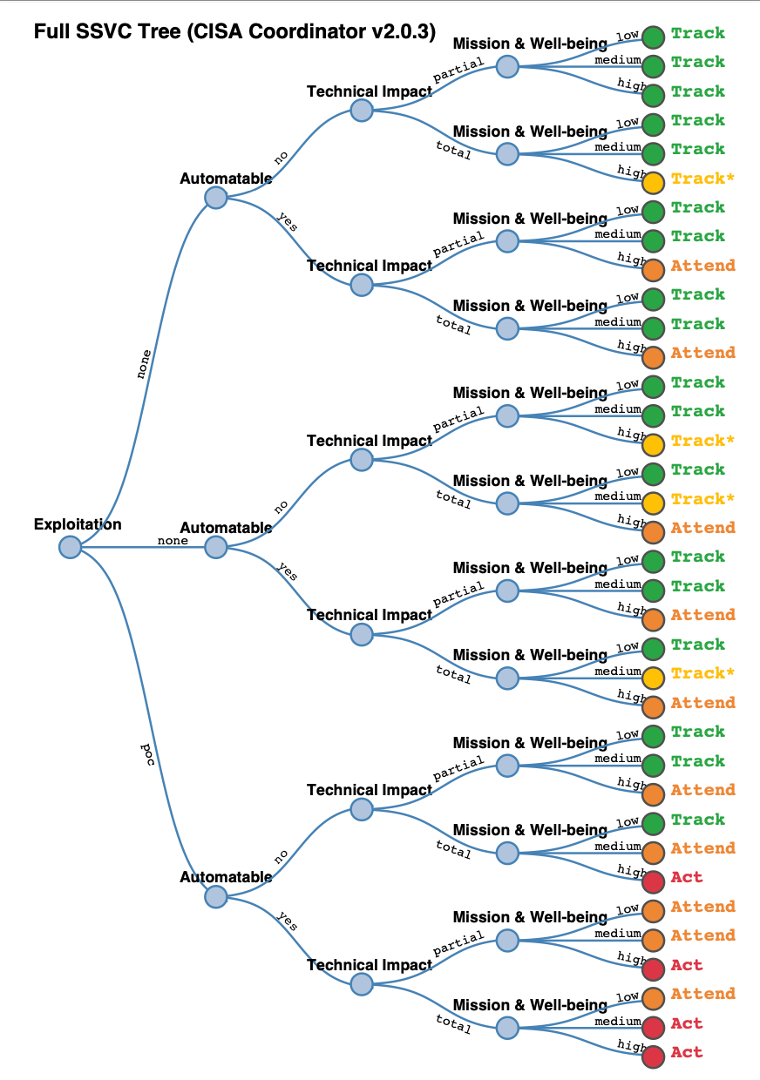 Figure 1: The full SSVC tree | www.cisa.gov
Figure 1: The full SSVC tree | www.cisa.gov
 Figure 2: A simplified view of the SSVC decision tree options
Figure 2: A simplified view of the SSVC decision tree options
When should you use SSVC?
SSVC relies on manual input of values from an organization, meaning each recommended decision is tailored to that business and particular vulnerability. It’s important to note that the manual effort involved here makes SSVC harder to scale.
Nonetheless, it’s a useful tool to enhance other risk scoring methods like CVSS or EPSS, providing more specific guidance and severity context. Think of SSVC as a playbook, helping you ask the right questions about each vulnerability to determine your organization’s specific exposure level and recommended actions.
CVSS, EPSS, SSVC: How do they compare?
SSVC is grabbing more attention lately from the cyber security industry. Some even suggest “flipping” from CVSS to SSVC when it comes to vulnerability decision-making as a primary method. We’ve created this comparison table to provide a comprehensive view of the major differences:
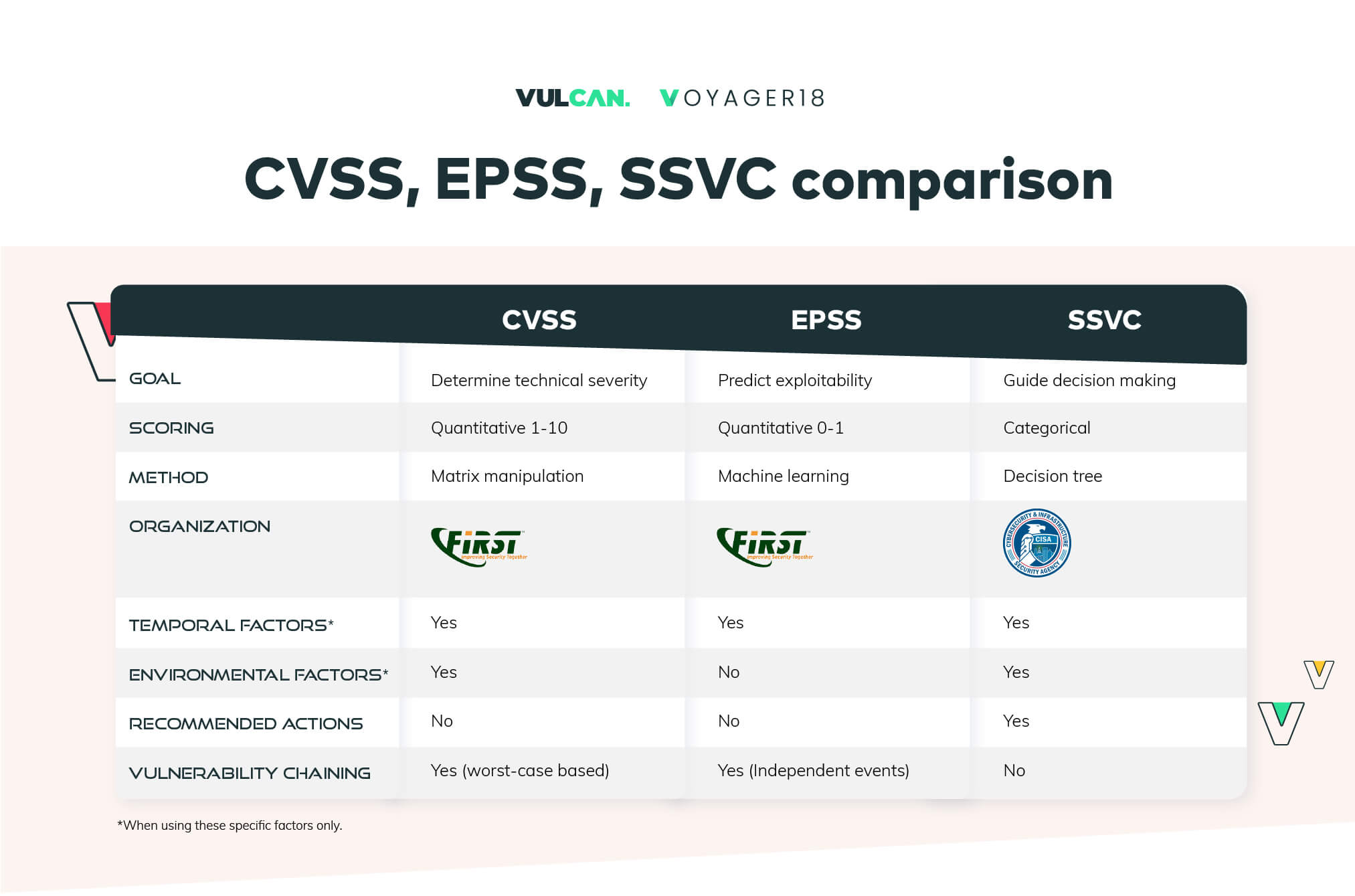 Figure 3: CVSS, SSVC, EPSS risk prioritization methods – comparison
Figure 3: CVSS, SSVC, EPSS risk prioritization methods – comparison
Our take
We are seeing more scoring methodologies emerge as viable options. But why choose one when you can select all of them? The key here is to know when to use them and when one method is more effective than the other. Examples:
- EPSS is great when trying to address vulnerabilities with limited resources, as it represents a more “efficient” score to consider. When there are indications of exploitation in the wild, EPSS will serve as yet another prioritization score to augment other methods.
- And while CVSS is commonly used to assess vulnerability severity and impact when trying to prioritize from the list of those critical CVSS vulnerabilities, EPSS can still be of value.
Next steps
Each new vulnerability is a reminder of where we stand, and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors:
- CVSS v4.0 – what you need to know
- Can you trust ChatGPT’s package recommendations?
- MITRE ATTACK framework – Mapping techniques to CVEs
- Exploit maturity: an introduction
- IBM’s Cost of a Data Breach report 2023 – what we learned
And finally…
Don’t get found out by new vulnerabilities. Vulcan Cyber gives you full visibility and oversight of your threat environment and lets you prioritize, remediate and communicate your cyber risk across your entire organization. Get a demo today.








