-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
Discover the "0.0.0.0 Day" vulnerability affecting major browsers on macOS and Linux, posing serious risks from local network exploits.

This post explores the technical details and potential impacts of the “0.0.0.0 Day” vulnerability, a critical flaw that affects popular web browsers – Chrome, Firefox, and Safari, by exploiting local network requests.
Discovered by Oligo Security’s researcher Avi Lumelsky, this vulnerability impacts systems running macOS and Linux, presenting a serious security risk.
The root of the problem lies in the varying levels of security enforcement among different web browsers, coupled with the absence of a unified standard across the browser industry.
This disparity allows the otherwise benign IP address 0.0.0.0 to be weaponized by attackers, turning it into a gateway for accessing local services. These services may include those crucial to development environments, operating systems, and even internal networks.
The 0.0.0.0 Day vulnerability impacts are extensive, posing risks to both individual users and entire organizations. The recent identification of exploitation campaigns, such as ShadowRay, highlights the critical need to mitigate this vulnerability promptly and effectively.
Avi Lumelsky of Oligo Security was instrumental in identifying the 0.0.0.0 Day vulnerability. The research, detailed in their blog post, uncovered a flaw in how browsers process requests to the 0.0.0.0 IP address – a special address used to indicate all network interfaces.
This address, rather than being properly isolated, was found to be accessible through common browser mechanisms, leading to the exploitation of local network services.
Oligo’s discovery uncoveres a logical flaw affecting all major browsers, including Chromium, Firefox, and Safari. This vulnerability allows external websites to interact with and potentially exploit software running locally on MacOS and Linux systems. Notably, Windows is not affected by this issue.
The 0.0.0.0 Day vulnerability exploits the inherent handling of the 0.0.0.0 IP address in browsers. Here’s a breakdown of how this vulnerability operates:
0.0.0.0 serves a variety of purposes. You might recognize some of its common uses: representing “all IPs on this host,” “all network interfaces on this host,” or simply “localhost.”
According to RFC 1122, 0.0.0.0 is identified by the notation {0,0}.
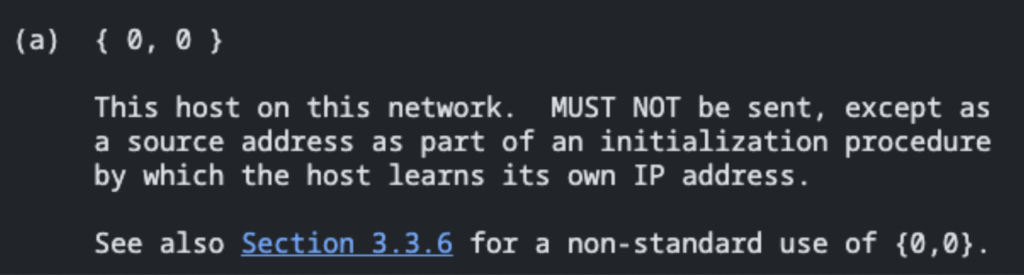
The standard restricts its use as a destination address in IPv4, permitting it only as a source address in specific scenarios, such as during the DHCP handshake when an IP is being assigned for the first time via a DHCPDISCOVER packet.
Additionally, 0.0.0.0 is sometimes utilized in /etc/hosts files to block specific domains, functioning as an adblocker, or in networking policies where the CIDR block 0.0.0.0/32 is used to allow all IP addresses.
This is a well-known technique with various purposes, the most common being to recognize returning visitors. However, it can also be exploited by threat actors for phishing and other malicious activities.
Websites would often gather significant information about a visitor without them ever logging in by cross-referencing this data. Some sites would go a step further, using JavaScript to scan a visitor’s local ports (localhost, 127.0.0.1) immediately upon loading the page.
This technique creates a fingerprint that can distinguish between valid responses (indicating something is running on a port) and HTTP errors (indicating nothing is there).
Browsers should ideally block such requests, as even a single one could lead to exploitation. Yet, for years, this was standard practice on the internet, overlooked until it became clear that it could lead to security breaches.
By the time this was realized, the behavior was deeply embedded in browser functionality, making it challenging to rectify.
In 2006, malicious script tags were already being documented in the wild, specifically targeting home routers. The absence of standardization was a major contributor to this problem, highlighting the urgent need for a consistent security framework across all browsers.
There was a clear demand for a standardized approach that could extend Cross-Origin Resource Sharing (CORS) to help browsers differentiate between local, private, and public networks. Google responded decisively to this need by introducing Private Network Access.
Browsers have consistently been a prime target for security threats, prompting developers to introduce advanced security features like sandboxing, HTTPS-only cookies, and standards like Cross-Origin Resource Sharing (CORS) to manage cross-site requests.
These measures help protect servers and users from malicious websites that attempt cross-site request forgery (CSRF) attacks, safeguarding private data, internal networks, and local applications.
Even non-browser applications often rely on loading resources from external domains, such as Google Analytics, client-side SDKs, or embedded scripts and videos.
By design, browsers can send requests to nearly any HTTP server using Javascript. When a cross-site response is received, the browser’s security protocols determine the appropriate action:
However, there are instances where the response itself is irrelevant. The 0.0.0.0 Day vulnerability highlights a scenario where a single request can be sufficient to inflict harm. Before delving into the details, it’s essential to understand some foundational concepts.
For years, there was uncertainty around how browsers should manage requests to local or internal networks from less secure contexts. In practice, domains like attacker.com should never have access to localhost in any real-world scenario.
Historically, browsers have leaned heavily on CORS (Cross-Origin Resource Sharing) to address these issues. While CORS is effective, it primarily works at the response level, allowing requests to be made before determining if they should be blocked or allowed.
This isn’t sufficient, as even a single HTTP request could potentially compromise a home router. Users need a way to stop these risky requests from occurring in the first place.
Eventually, Chrome has introduced Private Network Access (PNA) as a new standard which enhances CORS by limiting the ability of websites to send requests to servers on private networks.
PNA establishes a clear distinction between public, private, and local networks. Websites loaded in less secure contexts are restricted from communicating with more secure ones. For instance, malicious domains cannot connect to IP addresses like 127.0.0.1 or 192.168.1.1, as these are considered private to a higher degree.
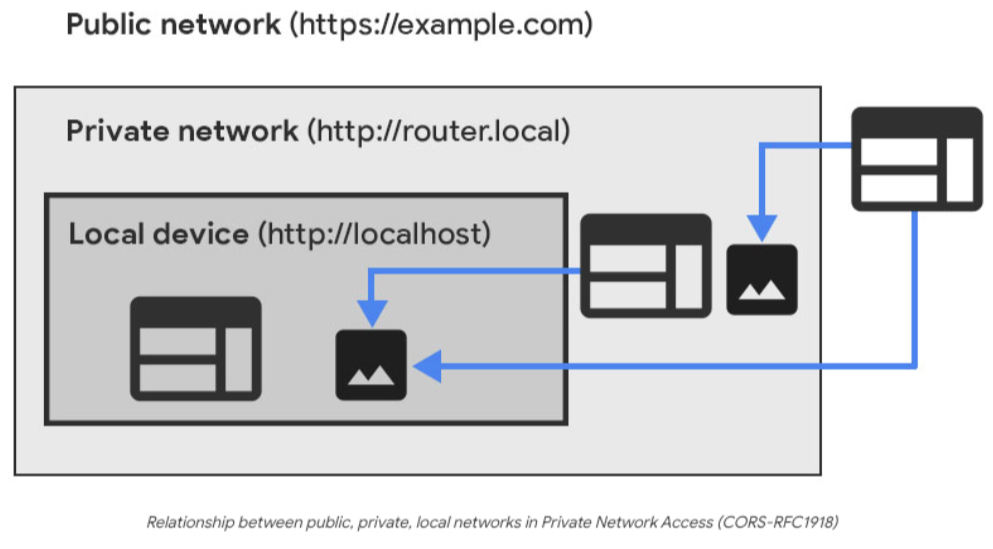
Unlike CORS, which primarily safeguards against unintended content being loaded in unsafe contexts at the response level by masking or dropping resources, PNA goes further by preventing the request from being made in the first place.
During their investigation, Oligo’s researchers noticed something peculiar about the PNA specification—while certain IP segments are categorized as private or local, “0.0.0.0” was conspicuously absent from this list. They assumed that, under PNA, websites would be restricted from sending requests to 0.0.0.0, as it shouldn’t be used as a destination address.
To test this, they set up a dummy HTTP server on localhost (127.0.0.1) and attempted to access it from an external domain using 0.0.0.0 in a Javascript request. To their surprise, the request went through, successfully reaching the server.
What happened here is that the browser, operating under a public domain (.com), sent the request to 0.0.0, which was then intercepted by the dummy server listening on 127.0.0.1.
The server processed the request and returned a response, which was blocked by the browser’s CORS implementation from reaching the Javascript context. This revealed a significant oversight—public websites could initiate requests to any open port on a host without being able to view the response, effectively bypassing the current PNA protections.
Recognizing the severity of this flaw, the researchers responsibly disclosed their findings to all major browsers, emphasizing the need for a real-world threat and attack vector to underscore the vulnerability.
As a first step, Oligo identified an application that could be at risk due to the 0.0.0.0 Day vulnerability. Many services using localhost operate under the assumption of a secure, restricted environment. This assumption often leads to insecure server implementations, where essential security measures like CSRF token checks or robust authorization/authentication are either weak or absent.
In some cases, no authorization or authentication is enforced, and CSRF tokens are ignored, as the application believes it’s running in a trusted, isolated network. This can lead to exposed POST HTTP routes that allow unauthorized write access to resources and configurations, potentially enabling code execution.
To exploit this vulnerability via the browser, a locally running HTTP server on a localhost port is needed. An attacker could exploit services that have HTTP routes capable of modifying files or configurations, as many real-world applications make such security trade-offs, presenting an opportunity for exploitation.
Private Network Access (PNA) is a significant step forward, led by Google and the broader community, aimed at preventing public websites from sending HTTP requests via Javascript to services on local networks.
However, until PNA is fully standardized and widely adopted, such risks remain. PNA needs to be universally implemented across all browsers to effectively close this loophole.
Cross-Origin Resource Sharing (CORS) also plays a crucial role in web security, helping to ensure that attackers can’t read response data when making unauthorized requests. If a CORS header isn’t included in a response, the attacker’s Javascript code won’t be able to access the response content.
However, CORS primarily blocks the response from reaching Javascript, allowing requests to still reach servers in “no-cors” mode, even if the attacker doesn’t care about the response.
In their demonstration, Oligo Security researchers revealed that by combining 0.0.0.0 with “no-cors” mode, attackers can exploit public domains to attack localhost services, potentially leading to remote code execution (RCE) with just a single HTTP request.
Thanks to their findings, browser developers prioritized fixing this vulnerability by blocking 0.0.0.0 as a target IP, ensuring that all browsers coordinated to avoid introducing new vulnerabilities in isolation.
While waiting for browser updates isn’t always feasible, Oligo advise developers to take proactive steps to safeguard their local applications:
In response to responsible disclosure, major browsers are beginning to address the vulnerability associated with HTTP requests to 0.0.0.0. This issue is now being incorporated into security standards through a Request for Comment (RFC), leading to forthcoming restrictions on 0.0.0.0 as a target IP in the Fetch specification, which governs HTTP request behavior.
Starting in April 2024, browser teams have acknowledged the flaw and are working on updates.
For instance, Google Chrome, through its Private Network Access (PNA) initiative, will gradually block 0.0.0.0 in Chromium versions, with full implementation expected by Chrome 133.
Apple Safari has already adjusted WebKit to block 0.0.0.0 requests, while Mozilla Firefox has yet to implement a fix but is updating the Fetch specification to block the IP in the future.
Currently, different browsers handle requests to local networks inconsistently, leaving a gap that still allows potential exploitation.
Each new vulnerability is a reminder of where we stand and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors: