The first part of this blog post series, The Three Stages of Enterprise Vulnerability Remediation, described the most serious challenges facing effective vulnerability remediation—complex infrastructures, distributed applications, and fragmented stacks. In order to pre-empt threats or contain their blast radius, today’s enterprises must have policies, processes, and tools in place to: analyze and assess vulnerabilities, apply the optimal combination of remediation methods to high-priority vulnerabilities, and automate and orchestrate vulnerability remediation workflows to the greatest extent possible.
This blog post will provide eight best practices to help overcome the challenges and requirements of vulnerability remediation in today’s dynamic and complex environments.
Continuous Detection
With traditional periodic scanning, organizations are in the dark regarding their vulnerability status between scans. The objective, therefore, must be continuous detection so that they have visibility into their current security posture at all times.
The first two best practices, therefore, are focused on how to effectively achieve continuous discovery and detection of vulnerabilities. Continuous detection is particularly critical in today’s dynamic, always-connected, and borderless environments. It’s no longer just corporate servers under attack but also ephemeral cloud instances and containers, highly exposed web applications, not to mention the mobile devices and IoT endpoints that interface continuously with the network.
In theory, an enterprise can actively scan its assets and detect published vulnerabilities using public sources such as the CVE (Common Vulnerability Exposure) List from MITRE and the U.S. government’s National Vulnerability Database (NVD). The Common Vulnerability Scoring System (CVSS) maintained by the Forum of Incident Response and Security Teams (FIRST) is a good resource for scoring the severity of a vulnerability. However, legacy active scanning methods can impact availability and are therefore not typically run continuously. Another obstacle to continuous detection is the sheer scope and velocity of vulnerabilities, with the number of vulnerabilities exposed over the last three years having doubled compared to the previous three-year period.
Here are three best practices that can support continuous detection:
1. Scan hosts more frequently than networks: Network-based scanners add significant overhead as they scan through network services. They also require attention such as configuring settings, opening firewall ports, and so on. Host-based scans, on the other hand, do not traverse the network; they eliminate network overhead and allow more continuous scanning.
2. Scan images rather than instances: In modern cloud-native applications, most of the server instances are installed from one image. Testing the image for vulnerabilities instead of scanning the instances is yet another way that organizations can achieve continuous detection without straining network resources.
3. Augment active scanning with “scanless” non-disruptive methods: Use data from existing DevOps, security, and IT repositories such as patch/asset management systems to conduct scanless rule-based profiling of potential vulnerabilities across all network nodes. When these non-disruptive scanless results are consolidated with the results of periodic active scanning, the organization can achieve virtually real-time visibility into vulnerabilities without impacting performance. This approach can be implemented using open-source tools such as osquery and QRadar.
Smart Prioritization
Legacy vulnerability management systems rely on external metrics to prioritize vulnerabilities. One very common metric is the above-mentioned CVSS score, which reflects the vulnerability’s severity according to characteristics such as attack vector, scope of potentially impacted components, level of risk to confidential data, and impact on availability. However, it is not unusual to vulnerability risk management; 44% of vulnerabilities incorporated into malware had low or medium CVSS scores.
This relates to best practice #4:
4. Using multiple factors and a broad context when assessing the risk level and hence the priority of a detected vulnerability.
A variety of external and internal sources should be correlated in order to better understand the severity of a specific vulnerability within the organization’s unique environment. Examples of external sources would be the CVSS score as well as threat intelligence repositories. Internal sources would be the organization’s asset management and change management systems to understand the business criticality and security posture of the assets threatened by the vulnerability.
An example of highly customized and targeted prioritization would be the discovery of a vulnerability with a high CVSS score that can only be exploited via USB, in a public cloud based workload. Information from the organization’s infrastructure and cloud monitoring stack reveals that all the assets that could be affected by the vulnerability are cloud-based only. The detected vulnerability can be safely assigned as low priority since it cannot be exploited in the organization’s environment.
Orchestrated and Automated Remediation
The one overarching goal of vulnerability management is fast and effective remediation. The next three best practices can help you ensure that your vulnerability management process is remediation-focused:
5. Maintain a single source of truth for all relevant teams: Enterprises typically have multiple teams working on vulnerability remediation. For example, the security team is charged with the responsibility for vulnerability detection, but it is the IT or DevOps team that is expected to remediate. Effective collaboration is essential in order to create a closed detection ↔ remediation loop. The teams’ specialized stacks of databases, processes, and tools must be tightly integrated into an orchestrated vulnerability management platform that shares a single source of truth. This best practice can be implemented in-house, or it can be achieved through third-party solutions.
6. It’s not all about patching: Vulnerability remediation must take shape in a reality where patches are not the only solution. Other remediation approaches include, for example, configuration management and compensating controls, such as shutting down a process, session, or module. The optimal remediation method—or combination of methods—will differ from vulnerability to vulnerability. In order to achieve this best practice, it is important to maintain a knowledge base of how to match the best remediation solution to a vulnerability, based on the organization’s cumulative vulnerability management experience. It is also possible to take advantage of third-party knowledge bases that rely on very large data sets.
7. Remediation playbooks: In order to match the scalability and velocity of today’s threat environment, vulnerability remediation must be as automated as possible. One highly effective way to achieve such automation is to create predefined playbooks that are tailored to the organization’s environment. A simple playbook scenario is illustrated below:
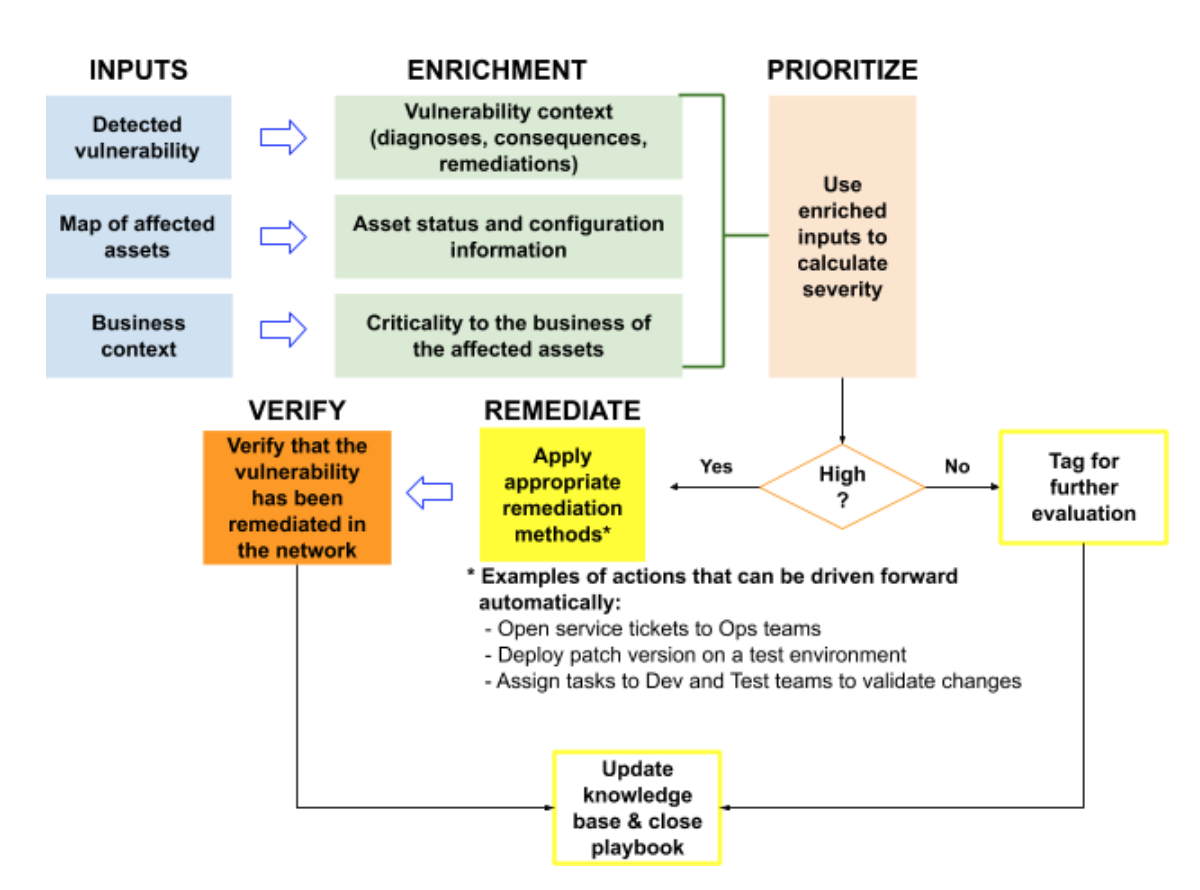
Today, there are tools that support both off-the-shelf and customizable automated remediation workflows. And vulnerability management platforms like Vulcan Cyber come with a library of workflows that can then be customized to meet the organization’s specific requirements.
Constant Metrics-Based Improvement
And here’s the eighth best practice:
8. Use vulnerability management metrics to constantly improve and finetune detection, prioritization, and remediation processes.
An important part of this best practice is knowing which vulnerability management metrics are important to track. Purely quantitative metrics such as a vulnerability count, average CVSS scores of detected vulnerabilities, number of scans run, or vendor-based criticality do not provide meaningful insight into the effectiveness of your vulnerability management efforts. As discussed in more detail in this blog on vulnerability metrics, the more meaningful metrics are qualitative—such as coverage, vulnerability dwell time, average number of vulnerabilities per asset over time, and to what extent SLAs are being met.
Make it a cross-enterprise objective to improve the vulnerability remediation metrics that have a real impact on your organization’s KPIs.
Final Note
Vulcan Cyber was designed from the ground up to fit seamlessly into an organization’s environment in order to address its unique vulnerability management needs. It integrates via bi-directional APIs with the organization’s existing scanning, monitoring, and remediation tools to create automated workflows that ensure end-to-end vulnerability detection, prioritization, and remediation. Vulcan Cyber becomes a single source of truth for all teams involved in vulnerability remediation. Its advanced prioritization, automation, and orchestration capabilities significantly shorten time to remediation while enhancing the organization’s security posture.
Contact us to learn more about how Vulcan Cyber can help you overcome the challenges of vulnerability remediation. Arrange your free demo today.









