Lots has been happening in the risk-based cyber security market as of late. In the past couple of weeks alone, we’ve witnessed two major power moves: Insight Partners’ $110M investment in Brinqa and the announcement of Kenna security’s acquisition by Cisco. At Vulcan Cyber, we know this rising tide will float all boats.

So first, we’d like to welcome Cisco to the risk-based cyber security market and offer our sincere congratulations to both Cisco and Kenna Security. These recent developments are yet further evidence of a shift in mindset among companies and tech giants, who are finally realizing that cyber risk management must be a top priority. And this is in large part due to mounting pressure from customers following the initial 2017 Equifax breach.
The need here is clear: Cyber hygiene tailored to the needs of the modern enterprise both in terms of scale and complexity. And the more players there are working to better manage and reduce cyber risk, the more secure our digital businesses, governments, and online livelihoods will be.
But a big piece of the cyber hygiene puzzle is missing…
It’s not just about the tools; It’s also about the process
It’s no secret risk-based cyber is a challenging market—one that’s frequently neglected, under-resourced, and underfunded. It’s no surprise then that managing cyber hygiene programs is often considered a dirty job.
To address this challenge, millions of startups worldwide are working to develop new, cutting-edge technologies. And technology is great, but when it comes to the risk-based cyber security market, it’s about much more than just the tools. There is a real need to look at the bigger picture in order to manage risk across all attack surfaces and to combine technology with processes and workflows so that cyber security is viewed as a business risk, not just a security problem.
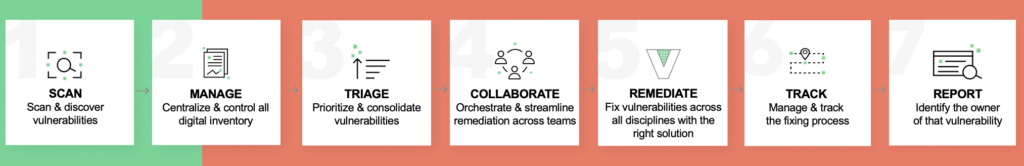
Dev teams have Jira as their end-to-end development management hub; IT teams use ServiceNow as their go to for ITSM processes; but what about the cyber security market? It too needs, and deserves, tools to support the business processes associated with reducing cyber risk.
I believe that at Vulcan Cyber, we’ve designed and built exactly that—a Risk Remediation Platform that empowers security teams to manage every risk, across any attack surface in order to achieve cyber-risk remediation outcomes.
Risk-based prioritization is just the start
Vulnerability prioritization, the fundamental layer of our Risk Remediation Platform, is also one of the anchors in our philosophy; prioritization is fundamental. But it’s the means, not the end. It’s the how, not the why. The goal should always be getting vulnerabilities fixed, and driving remediation outcomes.
In fact, based on years of experience in this space and hundreds of customer interactions, we’ve found that focusing too much on prioritization may actually increase risk. How?
-
Black-box priorities:
Vulnerability scoring systems aren’t always accurate, transparent, or customizable, making it difficult to know if you’re really capturing your organization’s top priorities.
-
Missing remediation:
Prioritization is just one piece of the puzzle. Without a clear path to remediation, a list of top-priority vulnerabilities can increase confusion and sidetrack key team members.
-
Lack of scale:
With the size and scope of most organizations’ networks, automation and orchestration are essential features for actually dealing with vulnerabilities at scale.
We’ve had a healthy competition with Kenna Security over the years. No doubt this market is big enough for a difference in approach and core philosophy. Kenna’s philosophy is that, faced with “a tidal wave of vulnerabilities… you can’t fix them all.” Their product focuses on effective vulnerability prioritization, but there it ends.
Implementing an effective cyber hygiene program—whether vulnerability management, cloud security, or application security—requires going beyond prioritization. It must involve multiple components, supported by automation and not only powered by manual efforts, in order to truly master cyber hygiene programs across the organization.
There is indeed a growing awareness of the need for cyber risk management. But when it comes to everything beyond scanning vulnerabilities, the majority of organizations are still relying on manual, complex processes. With no proper cyber security asset management in place; no remediation, tracking, and reporting capabilities; as well as a lack of collaboration between teams; companies are still remaining at risk.
And with 56% of organizations lacking the ability to remediate vulnerabilities quickly and at scale, according to our vulnerability remediation maturity study, there is certainly a gap to be filled.
The companies that have become the golden standards in their markets, such as Atlassian, ServiceNow, and Salesforce, all focus on delivering outcomes to their customers—whether delivering code, driving and applying change, or closing deals. And when it comes to cyber risk, remediation and not prioritization must be the outcome.
This is the Vulcan difference.
What sets Vulcan apart
The Vulcan Cyber® Risk Remediation Platform starts with prioritization, but doesn’t stop there. We provide a complete scan-to-fix solution with four levels of defense:
- Prioritize: Determine priorities based on your organization’s business needs and mission-critical assets, rather than on an opaque or “black-box” score.
- Remediate: Find the best fix for every risk and get them into the hands of the right teams for rapid remediation.
- Orchestrate & automate: Hand over the most tedious aspects of vulnerability management to automated workflows so your team can scale up and clear their backlog.
- Analyze: Analyze the effectiveness of remediation campaigns so identified vulnerabilities are fixed, not just identified, to minimize business risk.

At Vulcan Cyber, we deliver. So to put our money where our mouth is, we are offering the cyber community two complimentary, game-changing products: Vulcan Free, the industry’s only free risk-based vulnerability prioritization tool, so you can kickstart your risk-based security program without zero commitment; and Vulcan Remedy Cloud, the world’s largest database of vulnerabilities, featuring easy-to-implement remediation steps.
Final thoughts
Philosophies may differ, but we founded this company to make a change, to provide a better, safer digital world. And that’s why we are so thrilled to see industry leaders like Cisco and Insight push the risk-based cyber security market forward. And we at Vulcan will continue to do our part to help customers “get fix done.”









