For many organizations, implementing a successful vulnerability management framework remains a challenge. Tracking vulnerabilities has been possible for decades, followed by the ability to identify them in systems, software and applications. But even the most established vulnerability management programs are held back by certain aspects of their processes.
In our recent survey with SANS, we found that the number of organizations with formal vulnerability management (VM) programs is up more than 11 percentage points from 2020. This means that more than 92% of organizations have at least some processes in place to manage their vulnerabilities.
Meanwhile, while infrastructure remains the main focus of most programs, cloud services have emerged as a growing area of interest for organizations.
This blog is a summary of just some of the survey findings, covering each stage of the VM lifecycle, and addressing the effects of remote work and increasing migration to the cloud. You can read the full report here.
Setting the stage
Fortunately, most organizations have a formal vulnerability management (VM) program, managed either internally or by a third party. According to the report, nearly 20% of organizations have an informal vulnerability management framework, and the remaining organizations have plans to develop a program in the near future.
As expected, VM programs are most mature when it comes to on-premise infrastructure, already employing automation to a high degree. Cloud and container infrastructures are getting more attention, though, with organizations increasingly adopting or planning to adopt frameworks to meet the shifting reliance on cloud solutions.
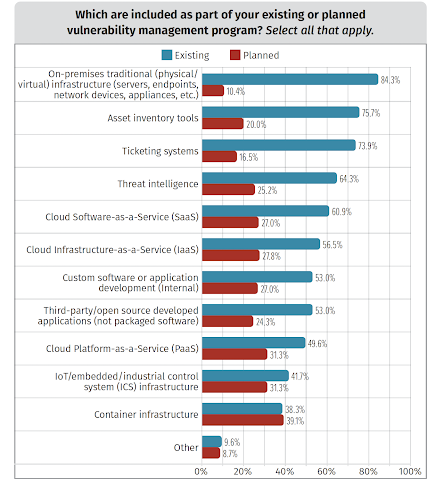
How mature are vulnerability management frameworks today?
Prepare
Organizations are limited when it comes to keeping track and managing their assets and therefore their maturity of assets is affected. Contextual data is not easily available and the cloud has only made things more complicated. Tighter integration will help here.
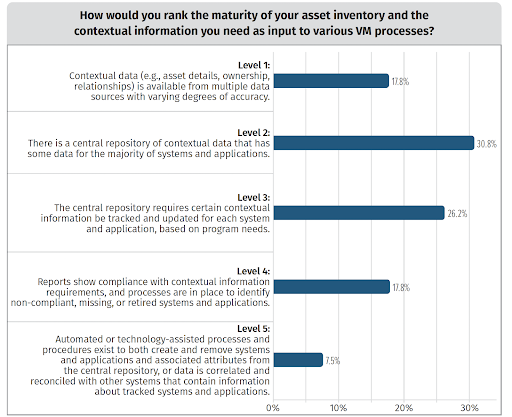
Identify
Identifying vulnerabilities is easiest within traditional infrastructure, with most organizations achieving this to a high level. Where they predictably fall short is when it comes to the cloud and containers.
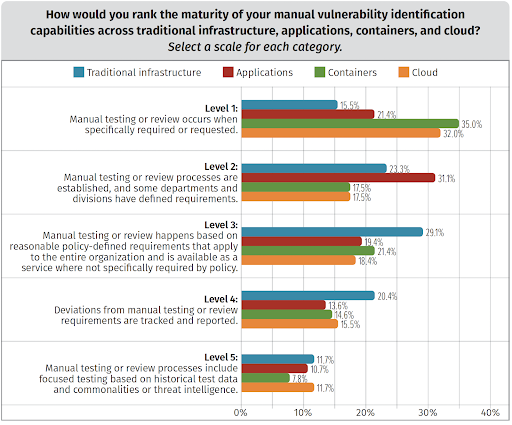
Analyze
Most organizations are effective at prioritizing risk based on threat intelligence sources and external data, alongside some light customization to more closely correlate with their business-specific needs. But cyber risk is not a one-size-fits-all consideration. Prioritization must take into account the organization’s unique profile and environment.
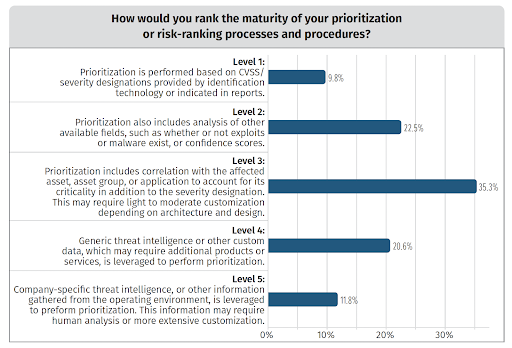
Communicate
Communication plays a key role in establishing buy-in from the community of VM stakeholders. Use cases can range from getting executives and board members to fund special projects that deal with technical debt to influencing IT and development stakeholders to engage more meaningfully in treating or remediating vulnerabilities. Making sure we are building and refining the right stories—backed by data—is a key component of this phase of the life cycle.
Metrics and reporting are a challenge for many organizations, while it appears that organizations are a little more confident in their alerting capabilities than in the reports and metrics they have available to present to stakeholders.
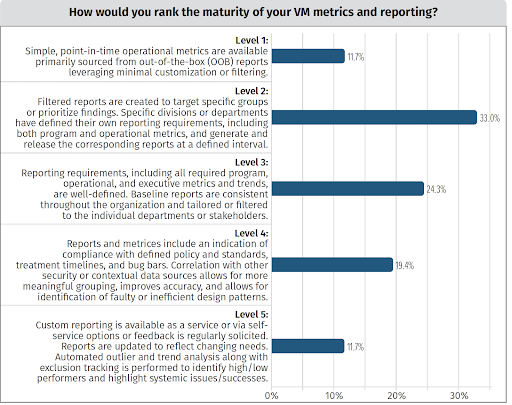
Treat
Treatment or remediation is the end goal of any vulnerability management program. The problem is that it is rarely the responsibility of a single team, but a joint effort utilizing different departments, resources, and tools. Clear communication and robust, well-established processes go a long way to effectively mitigating risk, while ill-defined workflows and solutions can exacerbate existing issues.
Adapting your vulnerability management to the cloud
It’s no surprise that organizations fall short when it comes to vulnerabilities in the cloud. Given that we still haven’t completely nailed vulnerability management in traditional infrastructure, it is understandable that we’re struggling with the added complexity, scale, and change that comes with increasing cloud deployment.
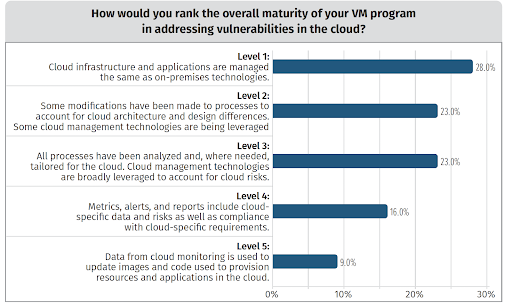
The opportunity is there to hugely improve VM in the cloud. But this takes planning and strategy to keep up with the scale and rate of change. Organizations must embrace the shared responsibility model, and recognize the distribution of responsibility across the cloud provider and the organization. Finally, they must keep up to date with cloud-native or other technologies that can help them succeed in keeping their environments secure.
Getting the most out of your vulnerability management framework
Organizations have the best of intentions when it comes to managing vulnerabilities. But often they are held back by unclear communication and muddy data, exacerbated by recent moves to multi-cloud and remote working models. As this trend grows, we must take advantage of the solutions that might help us in staying secure.
The Vulcan Cyber risk management platform provides an end-to-end solution to give you full oversight across all attack surfaces and all stages of the cyber security workflow, allowing you to fully own your risk, and finally mitigate it. Book a demo today to find out more.
This blog post is based on our latest survey with SANS: vulnerability management— impacts on cloud and the remote workforce. You can read the full report here.









