Many IT pros hold the mistaken belief that macOS is safer than either Windows or Linux. But Apple vulnerability trends show otherwise.
It’s easy to see why Windows and Linux are the most frequently targeted by cyber criminals. With 74.79% market share, Windows is nearly ubiquitous; almost every organization is running some Windows systems. Linux holds a far smaller market share, at 2.49%—less than macOS, in fact—but it’s disproportionately targeted because it dominates the server sphere and hosts many mission-critical web apps and data.
So does that mean if you’re running macOS, you’re in the clear? Unfortunately not. The truth is that macOS, which holds 15.38% market share, is still a significant and growing target for attackers. In Q3 2021 alone, Apple Mac computer shipments were at 6.8 million units worldwide. And it only takes one serious Apple security flaw to wreak havoc on those systems.
So it comes as no surprise that, as DarkReading reported, “threat actors may be getting more serious about attacking Apple macOS and iOS environments.”
In fact, on MITRE’s list of Top 50 Products by Total Number of “Distinct” Vulnerabilities, macOS has leapt from #15 in 2020, to its current position at #5, right behind three top Linux flavors and Android and above Windows.
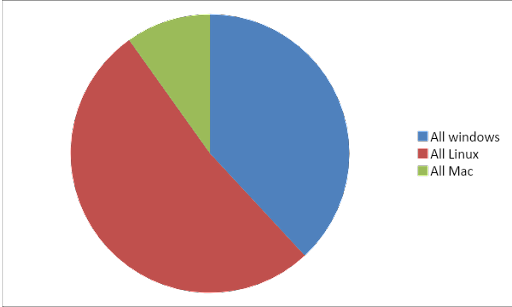
Figure 1: Top vulnerabilities by operating system (Source: MITRE data)
This has been an alarming rise, proving that no OS is immune from today’s vulnerabilities. And feelings of overconfidence on the part of security pros may be the downfall of organizations relying on macOS systems. Let’s explore a few top Apple security flaws to see what types of vulnerabilities are occurring most commonly in this environment.
Apple vulnerability 1: IOMobileFrameBuffer LPE CVE-2021-30807
IOMobileFrameBuffer is a kernel extension that lets developers control the device’s screen display. This vulnerability, CVE-2021-30807, exploits improper memory handling in the IOMobileFrameBuffer and could lead to privilege escalation, meaning unauthorized parties can perform unwanted and arbitrary actions on the system.
Like all local privilege escalation (LPE) vulnerabilities, the IOMobileFrameBuffer vulnerability requires local access, but it is relatively easy to exploit.
This was a zero-day vulnerability discovered and reported in 2021. A public exploit was issued immediately on GitHub, and this may have been exploited in the wild. This highlights a trend toward zero-day vulnerabilities for macOS in 2021.
This vulnerability affects more than just macOS systems: iOS products may also be affected. The only remediation available is updating to the latest OS versions immediately.
Apple vulnerability 2: WiFi Velocity LPE CVE-2021-30655
Sysdiagnose and WiFi velocity are debugging and logging utilities present on macOS systems. As demonstrated by security researcher Wojciech Reguła in his exploit, these two utilities can easily be combined to allow for privilege escalation. Reguła refers to this as a “vulnerability with a story.” Apparently, it was first reported to Apple in 2020, but they were unable to reproduce the exploit. So he eventually created and published a “five-key” exploit, meaning all an attacker has to do is press five keys to gain root access on the local machine. As with the previous vulnerability, LPE vulnerabilities are often used in combination to ultimately grant privileges to remote attackers as well.
This vulnerability affects all macOS versions prior to 11.2.3. And like all LPE vulnerabilities, it requires local access; but it’s relatively easy to exploit, so you should never rely on local users to behave in a safe manner if this vulnerability is still present in the system. The only available remediation is to update to the latest macOS version immediately.

Apple vulnerability 3: Webkit memory corruption RCE CVE-2021-30734
Webkit is an Apple-developed (now open-source) web browser (rendering) engine used to provide web browsing services across all Apple systems including iOS, macOS, and iPadOS (along with Safari and some Linux browsers). The vulnerability actually lies in the WebAssembly subsystem of JavaScriptCore, an engine used in both Webkit and Safari. This makes it almost ubiquitous across macOS systems.
This one is another “Apple vulnerability with a story.” Discovery of this vulnerability actually translated into a $100,000 prize for a security researcher in Pwn2Own 2021, an annual hacking competition held at CanSecWest. Unlike the previous two examples we’ve seen, CVE-2021-30734 is a remote code execution (RCE) vulnerability, meaning that exploitation could allow an attacker to perform a “sandbox escape,” ultimately running arbitrary code through a privileged user account or the kernel.
This is not the first RCE vulnerability identified in Webkit over the years; 2010-1770 was perhaps among the earliest, and many more have been found to date.
All Safari browser versions up to 14.5.1 are vulnerable. In addition, both Apple and CISA report that a similar Webkit vulnerability, CVE-2022-22620, is currently being exploited in the wild. The only available remediation involves immediate upgrade to the latest version.
Final thoughts
With macOS taking an increasingly important role in enterprises of all kinds, you need to be aware of each Apple vulnerability lying in wait for this operating system. That’s especially true given that cybercriminals are actively exploiting older Apple vulnerabilities for which a fix is already available—in some cases, for almost a decade.
Are you giving enough thought to macOS and other Apple OSes when planning your risk management and vulnerability remediation programs?
Many organizations are so slow to remediate problems, or don’t have the expertise to practice proper cyber hygiene. This occurs for a couple of reasons:
- Most security professionals are far more comfortable with and strongly prefer Windows and Linux systems.
- Some risk management and remediation solutions don’t handle all your environments, demanding that you run specialized tools and procedures for macOS.
But as we’ve seen, macOS systems in organizations of all sizes are under attack. Again, it only takes one Apple security flaw. There’s really no excuse to let this major OS fall through the cracks. That’s why Vulcan Cyber is here to help with Vulcan Remedy Cloud, the world’s largest free, curated database of the latest fixes and mitigation solutions. So you can get answers, strategies, and workarounds fast when you need them—for all of your OSes.
And if you’re looking for a comprehensive risk management system that can handle macOS along with Linux, Windows, and more, Vulcan Cyber® has you covered, reducing risk across all your attack surfaces.









