First Officer’s log, Terrestrial date, 20220811. Officer of the Deck reporting.
The ship is back to normal operation and our patrol continues. As a support vessel, we are often in a position to “clean up the mess” discovered, or sometimes instigated, by the ships engaged in First Contact situations. They get all the glory. And that’s OK. They have often earned it, identifying threats like Chrome zero-day vulnerabilities and rogue employees, and blunting incursions when they happen. But without crews like ours making sure all the follow up gets done after than initial attack, the situation behind the lines would be much, much, worse.
We remain, as ever, vigilant.
Everyone wants to play
What happened
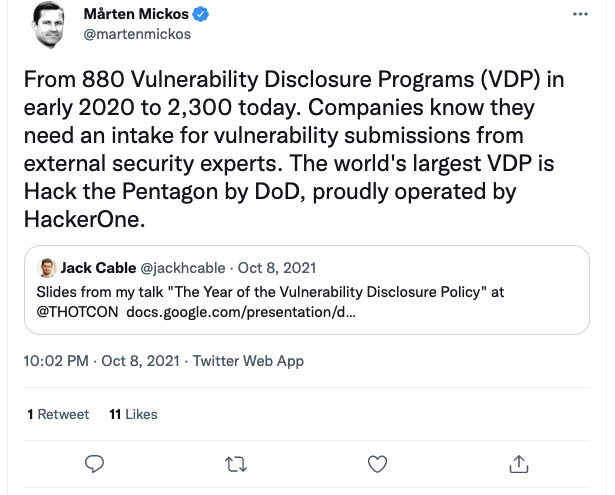
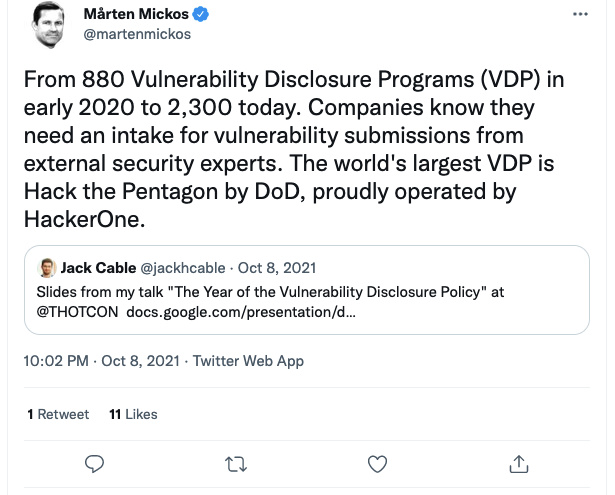
Bug Bounty programs are nothing new at this point. What was new was a malware gang recently offering a bug bounty program of their own. Now, not to be outdone, the US Department of Defense has joined the game with their own Bug Bounty program.
Why it matters
While this was a limited duration program run by a 3rd party, HackerOne, it shows that even the DoD can embrace the concept. With recent legislation to protect some “Good intent” research (see earlier 1st Officer’s Log entries), it shows that government and industry can see the value in independent research and is willing to protect, and reward, the folks who do it.
What they said
The news has been met with plenty of responses across the board. Read more.
But, funnily enough…
Bad people do bad things
What happened
An employee of HackerOne was fired for effectively stealing other people’s research and claiming it as their own to collect bug bounties. While stealing other people’s work is, sadly, not unheard of in, well, any field, it’s not often seen in the security research community. HackerOne reacted quickly, severing ties with the offending researcher.
Why it matters
Trust is a Big Thing™ in security research, both between researchers as a community and the organizations that rely on them to help secure their applications. Hopefully, this breach of trust will be a reasonably isolated incident and won’t damage the ecosystem that’s developed. If anything, it will severely damage the reputation of the researcher in question. Hopefully, it will also serve as a reminder that stealing other people’s work is not cool in anyone’s book.
What they said
No misuse of information gets off easy. This was no exception. Read more.
Another Chrome Zero-Day
What happened
Google has released a patch for CVE-2022-2294, which is the fourth Chrome zero-day vulnerability reported this year, and says the vulnerability has been exploited in the wild.
Why it matters
Google Chrome is one of the most popular browsers in the world, and with the proliferation of web applications and cloud applications that rely on browsers for management, zero-day exploits against Chrome, or any of its competitors, can be problematic. Fortunately, Google patched this one quickly and anyone with automatic updates will already be receiving the latest version.
What they said
Zero days are hot topics. And this one’s no different. See what people are saying.
Want to get ahead of the stories? Join the conversations as they happen with the Vulcan Cyber community Slack channel