-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
Cloudflare's latest reports sheds some interesting light on application security in 2024. Here are our 7 biggest takeaways.

The “State of Application Security 2024” report from Cloudflare provides an in-depth look at the evolving landscape of web application security. With insights derived from one of the world’s largest networks, the report sheds light on the most pressing security challenges and trends facing businesses today.
From the rapid weaponization of vulnerabilities to the increasing prevalence of DDoS attacks, the findings highlight the critical areas where organizations need to focus their security efforts. Here are the top 7 takeaways from the report that every business should be aware of to bolster their application security posture.
Hackers are attempting to exploit vulnerabilities faster than ever. In one case, a vulnerability was exploited just 22 minutes after the proof-of-concept (PoC) code was published.
This rapid weaponization of Common Vulnerabilities and Exposures (CVEs) highlights the critical need for organizations to deploy swift security patches and proactive defense mechanisms.
As soon as a vulnerability is disclosed, a race begins between attackers seeking to exploit it and defenders working to mitigate the risk. This finding underscores the importance of having automated security measures and real-time threat intelligence to stay ahead of attackers.
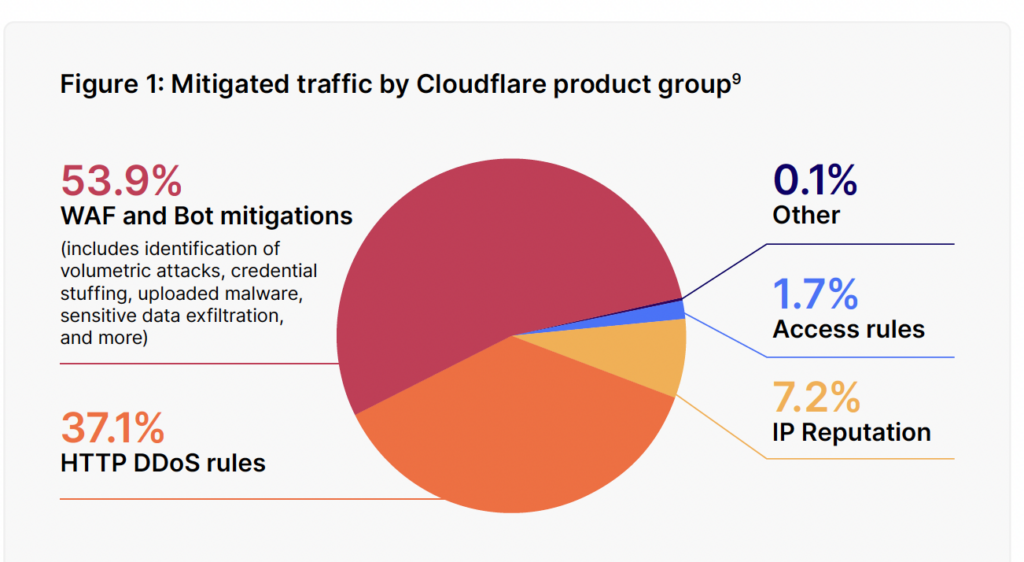
Distributed denial-of-service (DDoS) attacks continue to be a dominant threat to web applications, making up 37.1% of all mitigated traffic, according to the report. DDoS attacks overwhelm web servers with a flood of traffic, rendering them inaccessible to legitimate users.
The prevalence of these attacks highlights the need for robust DDoS mitigation strategies. Cloudflare’s data shows an increase in the volume and sophistication of these attacks, emphasizing the necessity for businesses to adopt comprehensive DDoS protection measures to safeguard their web applications and ensure uninterrupted service.
31.2% of traffic is bot traffic. 93% of that bot traffic is unverified and potentially malicious. This means that the majority of automated traffic hitting web applications could be aimed at disrupting services, scraping data, or executing fraudulent activities.
Effective bot management is crucial to differentiate between legitimate bots, like search engine crawlers, and harmful bots.
Without robust bot management, organizations risk performance degradation, data theft, and increased vulnerability to various attacks.
Implementing advanced bot detection and mitigation strategies can help safeguard applications from the detrimental impacts of malicious bot traffic.
The report reveals a staggering 93% year-over-year increase in application layer DDoS attacks. These attacks target the application layer, making them more difficult to detect and mitigate compared to traditional network layer attacks.
The significant rise in these sophisticated attacks highlights the need for advanced DDoS protection solutions that can identify and block application-specific threats. Organizations must stay vigilant and continually upgrade their DDoS defenses to protect against this growing threat.
In 2023, there were 97 zero-day exploits, marking a concerning increase in these types of vulnerabilities. Zero-day exploits take advantage of previously unknown vulnerabilities, giving attackers a window of opportunity before defenses can be implemented.
The rise in zero-day exploits emphasizes the need for proactive security measures, such as machine learning-based threat detection and automated patch management systems, to identify and mitigate vulnerabilities before they can be exploited.
APIs have become integral to modern web applications, accounting for 58% of all dynamic internet traffic. This reliance on APIs, while beneficial for business operations and customer experience, introduces new security challenges.
APIs expose endpoints that can be exploited if not properly secured. Organizations must prioritize API security by employing advanced tools that provide visibility into API traffic, enforce security policies, and protect against common API vulnerabilities like data exfiltration and endpoint enumeration.
A significant portion of APIs, approximately 33%, are shadow APIs—those that are unknown and unmanaged by IT departments. These shadow APIs pose substantial security risks as they can be exploited without detection.
This statistic highlights the importance of comprehensive API management and discovery tools. By continuously scanning for and inventorying all APIs, including shadow APIs, organizations can ensure that all endpoints are secured and monitored, reducing the risk of unauthorized access and data breaches.
Each new vulnerability is a reminder of where we stand and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors: