Cloud transformation offers many benefits to the modern enterprise. But it also presents significant challenges. It takes a lot of research and planning. It calls for expertise in the new cloud-based model of delivering IT. And it can potentially involve a significant amount of application redesign and coding work. But it also requires a fresh look at compliance.
Large-scale enterprises are often subject to a wide range of data protection regulations and standards. And a move to the cloud can add to the complexity of meeting these compliance obligations.
At the same time, the risk of attack on your information systems continues to grow at an alarming rate. This means the security requirements laid down by different regulatory bodies have become more important than ever.
This post runs through the most important considerations security professionals need to bear in mind when an enterprise is in the process of adopting the cloud.
1. Compliance and security are not the same
Compliance is simply a box-ticking exercise to ensure you have the right processes and technologies in place to meet the requirements of a regulatory authority, contract, or framework.
By contrast, security is driven by the specific threats to your organization and the measures it needs to take to protect against them. In other words, security is practiced for its own sake rather than to satisfy the requirements of a third party.
Security should therefore go beyond compliance, which is no more than a set of baseline measures that don’t necessarily guarantee sufficient security.
This distinction is key to understanding the difference between security requirements of compliance frameworks and the security measures you should actually take when you migrate your workloads to the cloud.
2. Most compliance frameworks cover more than just security
Security forms just one part of most data protection regulations and standards, which also cover the integrity and availability of personal data and the rights of data subjects.
For example, regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) grant citizens the right to access the personal data you store about them. Under the GDPR, you must also seek consent from individuals to send them marketing emails or, in the case of the CCPA, consent to sell the personal information of children under the age of 17.
Some requirements will have implications for any personal data you migrate to the cloud. In particular, data residency rules, which prohibit the transfer of personal data outside the territory they cover—except to specific countries that offer sufficient regulatory protection of personal data.
This isn’t by and large a concern if you only store personal data in your on-premises data centers. But, if you migrate it to the cloud, you may not be able to host it in certain cloud regions.
To ensure compliance, you’ll need to choose your cloud regions wisely. You may even need to adopt a multi-cloud strategy to ensure you have the right mix of data center regions in which to host personal data. However, this can have a knock-on effect on security by increasing the attack surface, adding to the complexity of protecting deployments and managing vulnerability remediation.
The Payment Card Industry Data Security Standard (PCI DSS) is slightly different from many other compliance frameworks because it’s specifically a security-orientated information standard. However, certain types of cardholder information are also classed as personal information. In such cases, you must also comply with any applicable data privacy regulations at the same time.
3. Cloud compliance is a shared responsibility
Public cloud platforms are compliant with a wealth of different data protection regulations and standards. However, just because your vendor has the appropriate attestation, certificate, or validation still doesn’t mean your workloads are necessarily compliant.
This is because compliance is a shared responsibility between the cloud vendor and the cloud user. That therefore means the responsibility for meeting the security requirements of compliance is also shared.
Each of the leading public cloud providers publishes its own guidelines to shared responsibility. These set out the security obligations of each party, so customers fully understand their responsibilities and those of the cloud vendor.
AWS breaks down its own shared responsibility model into the following two simple concepts:
- Security of the cloud: Amazon’s responsibilities as the cloud provider. These include its host operating system and hypervisor, the physical security of its facilities, and the security tools it provides to customers.
- Security in the cloud: Your responsibilities as the cloud customer. These include configuration of your network and other AWS services, the security of your applications and the guest environments that support them.
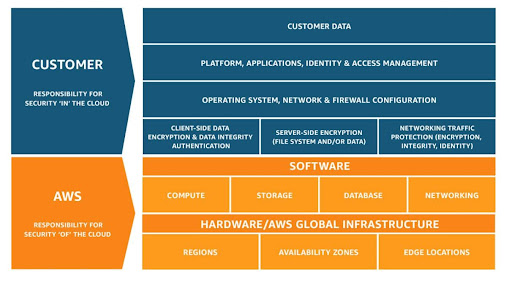
Figure 1: AWS shared responsibility model (Source: AWS)
4. Security provisions are loosely defined
Data protection regulations do not usually define specific measures you should take to protect personal information but rather that you maintain security practices that are appropriate to your organization. This should take into account the level of risk to your data and the potential harm to individuals in the event of exposure.
In other words, it’s down to you to determine what security controls you should take to protect sensitive information.
This will heavily depend on whether you host your workloads on-premises or in the cloud—each of which requires a very different approach to security. That’s because the cloud is a dynamic and much more complex IT environment, with lots of moving parts. It therefore has a very different kind of attack surface, with different risks and security challenges.
By contrast with its regulatory counterparts, the PCI DSS is more specific about what security controls you need to implement. It specifies twelve technical and operational requirements that cover measures such as firewalls, monitoring, encryption, and patch management.
The PCI Security Standards Council has also published a set of guidelines to help organizations, who are using or planning to use the cloud to process cardholder data, to meet their compliance obligations.
5. Cloud and on-premises requirements are fundamentally the same
With relatively few exceptions, the requirements of data protection laws and standards are no different whether you host your workloads in a traditional data center or in the public cloud. But that doesn’t mean to say the cloud hasn’t shifted the compliance goalposts.
What’s different is how you address the requirements and where the responsibility lies for meeting them.
For example, the cloud is dynamic, virtualized infrastructure and much more geared towards open-source technologies and distributed application architectures. This necessitates different tooling, such as cloud security posture management (CSPM) and container image scanning solutions, which have evolved to meet the new security challenges of the cloud.
Keeping track of cloud-based data assets is also much more problematic—especially for any large-scale enterprise with a complex array of deployments. This calls for automated discovery tools to ensure you have complete visibility into your inventory of assets, without which you cannot guarantee compliance.
All this additional complexity also adds to the burden of managing your attack surface. As a result, enterprise security teams can quickly become overloaded by the bewildering array of different security tools they need to protect their data assets and the substantial number of alerts they generate.
The answer to cloud complexity
On the one hand, shared responsibility for cloud security can help relieve you of much of the work traditionally involved in protecting sensitive data assets. But, on the other, you face an uphill struggle to stay on top of the overwhelming number of remediation tasks needed to keep your cloud workloads fully secure.
The answer to the problem is to take a risk-based approach to cybersecurity—through tooling that can help your organization focus its priorities on the biggest threats to your data. That way, you’ll both minimize the potential of a successful attack and satisfy the security requirements of meeting compliance.
Keep up with emerging vulnerabilities across your cloud environment. Get free access to thousands of vulnerabilities and get a fix done with Vulcan Remedy Cloud or request access to Vulcan Free.









