First Officer’s log, Terrestrial date, 20220825. Officer of the Deck reporting.
The crew is preparing for a series of presentations on Terrestrial date 20220827 at the CyberRisk Summit, where many of the senior officers will discuss our mission with representatives of the worlds we serve, and, hopefully, will serve in the future. It’s a reminder that our mission is subtle but also vital. I am looking forward to presenting with our department head on several aspects of our mission and how we address specific challenges.
In the meantime, here are some of the week’s biggest stories, including quantum computing and the emerging CVE-2022-26138:
VOIP: Vulnerable over internet protocols?
What happened
Late last year, researchers noticed a series of attacks against Digium phone systems, seeing around half a million between late December ‘21 and the end of March ‘22. The attackers dropped a web shell onto vulnerable VOIP servers which is not unlike the attack seen in 2020 against the Sangoma PBX software.
Why it matters
VOIP servers are very, very common in a lot of organizations, which makes them an inviting target to any threat actor looking to establish a foothold. And web shells can give the attacker a platform to launch any number of additional attacks, from exfiltrating data to spring boarding to other targets in the local environment or beyond.
The only unusual thing here is that the Unit 42 folks were looking at this back at the start of the year, and the report on it is coming out in July.
What they said
Phone hacks get people talking. Learn more.
Will Quantum Computing End Cryptology as we know it?
What happened
The short answer is no. But not through lack of trying, and a bit of hype. Though with practical quantum computing just around the corner, as it has been for a while, it’s time to seriously look at encryption standards that will be resistant to the quantum processers when (if?) they hit the mainstream. To that end, the Cybersecurity and Infrastructure Security Agency (CISA) has launched the post-quantum cryptography initiative.
Why it matters
While this may be coming a little late, it’s still a Good Thing™ and will hopefully lead to some algorithms and standards that will remain secure against a quantum computer. Fortunately, there are some existing algorithms that should prove resistant, so we’re already ahead of the game. The question is which will happen first: CISA is able to release a new standard, or quantum computing will make it into the mainstream.
What they said
The future has made a splash. See what people are saying.
CVE-2022-26138 and the continuing perils of hard coding
What happened
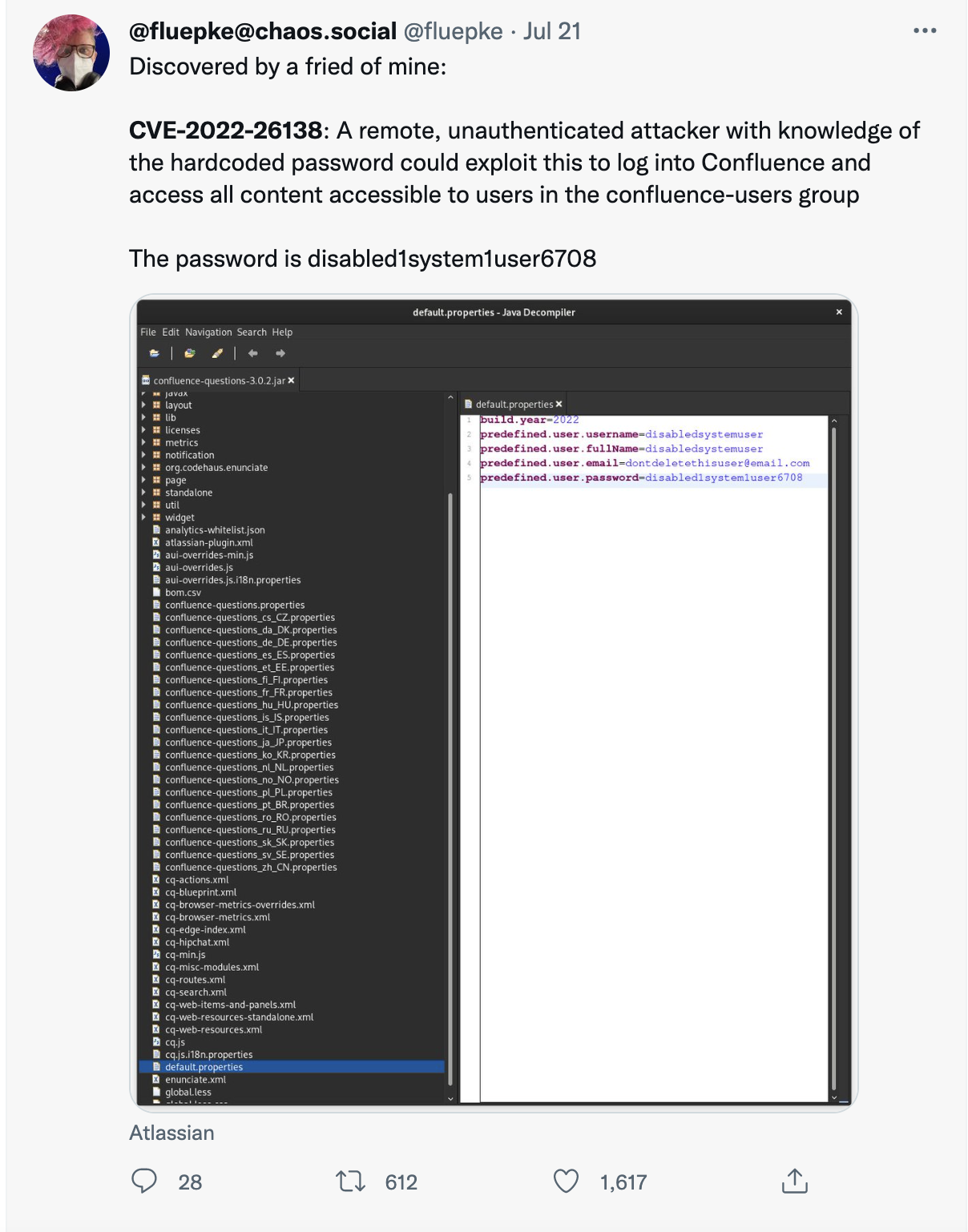
Atlassian warned that CVE-2022-26138 “is likely to be exploited in the wild.” The vulnerability stems from a hard coded password in the Questions For Confluence application on both Confluence Server and Confluence Datacenter. While uninstalling the app doesn’t fix the problem, Atlassian has released instructions on how to mitigate the issue.
Why it matters
Hard coding passwords is, basically, almost always a Bad Idea™. Threat Actors have a long history of leveraging hard coded and default passwords whenever they can, which is why “change the default” password is a normal part of most installations. Hard coding them is even worse than a default, because they’re not easily changed if they can be changed at all. Kind of the definition of “hard coding” there.
If you’re running the Questions For Confluence application, implement the fix sooner rather than later. Threat actors will leverage CVE-2022-26138 as soon as they can.
What they said
Exploit or no exploit, this one’s creating a lot of buzz.
Want to dive deeper into the stories? Join me, other members of the Vulcan Cyber team, and some of the industry’s leading practitioners, at the CyberRisk Summit. Register here.