TL;DR
Kaspersky’s Global Emergency Response Team (GERT) conducted a thorough investigation into an incident involving a Windows server that had been compromised via a vulnerable FortiClient EMS installation. Initial containment efforts included isolating affected systems to prevent further lateral movement by the attackers. Analysis revealed that the adversaries exploited CVE-2023-48788, targeting the FortiClient EMS to gain unauthorized access and execute malicious payloads. This exploitation allowed them to establish persistence and escalate privileges within the environment.
The investigation uncovered the attackers’ reliance on specific tools and techniques, including the use of PowerShell scripts to download payloads and execute commands. Indicators of compromise (IoCs) such as the following IP addresses were identified, highlighting their command-and-control (C2) infrastructure.
This blog delves into the technical details of CVE-2023-48788, the research conducted by Kaspersky’s Global Emergency Response Team (GERT), and the implications of the ongoing attacks. We also provide actionable guidance to mitigate the risks associated with CVE-2024-48788.
What is the FortiClient EMS Vulnerability (CVE-2023-48788)
CVE-2023-48788 (Critical CVSS Score: 9.8) is a critical vulnerability in Fortinet’s FortiClient EMS, a centralized management platform used to configure, deploy, and monitor FortiClient endpoints. The vulnerability stems from insufficient validation of user inputs in the EMS’s web interface, leading to a Remote Code Execution (RCE) exploit.
An attacker exploiting this flaw could execute arbitrary code on the EMS server with administrative privileges, potentially gaining full control of the system. The exploit mechanism leverages a flaw in the web interface’s input validation, allowing attackers to send malicious payloads to the server, bypassing authentication mechanisms.
The vulnerability emphasizes the growing challenges of the cybersecurity landscape as increasingly sophisticated attack vectors keep targeting critical vulnerabilities. With a CVSS score of 9.3, the active exploitation of this critical SQL injection in Fortinet’s FortiClient Enterprise Management Server (EMS) has lately been weaponized by threat actors to execute unauthorized code, allowing them to gain initial access and deploy remote access tools for deeper penetration into victim environments.
Exploit technical overview
On October 23, 2024, further attempts to exploit CVE-2023-48788 were detected. Kaspersky’s Global Emergency Response Team (GERT) identified signs of malicious activity when telemetry from their Managed Detection and Response (MDR) technology flagged suspicious registry hive access attempts originating from an internal IP address on a customer’s Windows server.
The IP was part of the customer’s network but not covered by the MDR solution. The unauthorized activity targeted administrative shares and registry hives through the Remote Registry service. Subsequent investigation by the team revealed that the affected server, exposed to the internet, had open ports associated with a vulnerable version of FortiClient EMS (7.01).
Analysis of filesystem artifacts and log files, such as ems.log and ERRORLOG, confirmed that attackers exploited CVE-2023-48788 through SQL injection to execute remote commands. They utilized tools like curl and certutil to download and execute the ScreenConnect remote access application, followed by installing additional payloads for lateral movement and persistence.
Logs also linked the attacker’s IP to a network associated with malicious campaigns involving Cobalt Strike. Further tracking uncovered similar exploitation attempts leveraging services like webhook.site to gather responses from compromised systems in multiple countries.
Gaining access through SQL injection, the attackers deployed remote monitoring and management (RMM) tools like ScreenConnect and AnyDesk for persistence and lateral movement. They did this using a PowerShell script hosted on webhook[.]site to collect responses from vulnerable systems.
This evolution highlights their ability to adapt and refine techniques for exploitation. These attacks leveraged unique ScreenConnect subdomains, such as infinity.screenconnect[.]com, to manage remote access.
The Kaspersky GERT Team also observed the use of the Windows native binary certutil for the same purpose. The installer would be stored as update.exe in the root of the C: drive, which would then be executed in the background. Judging by the y=Guest parameter in the URL query, the attackers seemingly relied on a ScreenConnect trial license.
“We found that after the initial installation, the attackers began to upload additional payloads to the compromised system, to begin discovery and lateral movement activities, such as enumerating network resources, trying to obtain credentials, perform defense evasion techniques and generating a further type of persistence via the AnyDesk remote control tool.” the researchers explain in their exploit analysis.
According to their investigation, information from webhook.site, the service “generates free, unique URLs and email addresses and lets you see everything that’s sent there instantly”. A specifically generated token which is already included within the URL guarantees uniqueness either by DNS domain or email addresses.
Additional services and features for a fee is also available for users of choice, sometimes included or complementary . GERT experts have confirmed that threat actors were using this service to collect responses from vulnerable targets while performing a scan of the systems affected by the FortiClient EMS vulnerability.
Knowing the specific webhook.site token used by the attackers, the experts were also able to identify 25 requests to webhook.site on a time period of five hours. Of these 25 requests, they validated that three requests had come from the same source while the other 22 all originated from distinct source IPs of vulnerable targets
Who is affected from CVE-2023-48788?
Affected Versions of the exploited vulnerability are: FortiClient EMS versions prior to 7.0.9 and 7.2.3. This vulnerability is particularly concerning for enterprises that rely on FortiClient EMS for endpoint management, as a successful exploit could lead to:
- Data Breaches – Unauthorized access to sensitive information stored on or transmitted through managed endpoints.
- System Compromise – Full administrative control of the EMS server, enabling attackers to deploy malware, ransomware, or other malicious tools.
- Lateral Movement – Exploitation of EMS to gain access to other systems within the network.
Organizations using FortiClient EMS versions prior to 7.0.9 or 7.2.3 should determine whether they’re affected and at risk:
- Verify the version of FortiClient EMS deployed in your environment.
- Check your system logs for unusual activity, particularly on the EMS server.
The active exploitation of CVE-2023-48788 was confirmed by last October, during an incident response investigation where attackers have been observed leveraging this vulnerability to compromise a Windows server running an outdated version of FortiClient EMS. The attackers used this access to install backdoors and exfiltrate sensitive data.
In their research, Kaspersky’s Global Emergency Response Team showed how the attack specifically targeted unpatched FortiClient EMS servers in enterprise environments, with the Attack Vector to Exploitation occurred via the internet-facing EMS web interface. After gaining access, attackers executed scripts to escalate privileges and establish persistence.
These findings underscore the critical need for timely patching and robust network defenses.
How to protect organizations from CVE-2023-48788
To effectively mitigate and defend against such attacks, it is highly advisable to deploy an Endpoint Protection Platform (EPP) agent on every operating system host, regardless of its designated role.
Additionally, implementing controls such as Application Control can help restrict the misuse of legitimate tools by malicious actors. Notably, the deployment of a Managed Detection and Response (MDR) solution on systems adjacent to the initial attack vector played a critical role in identifying and thwarting the attackers promptly, preventing significant damage or goal completion.
Equipping devices with agents designed for continuous threat monitoring and detection is essential in limiting the impact of an incident and ensuring a swift response.
Fortinet released an advisory detailing the vulnerability and providing patched versions of the affected software. However, unpatched systems remain highly vulnerable. Organizations at risk should take the following steps immediately:
- Update FortiClient EMS to version 7.0.9 or 7.2.3 (or later).
- Download patches from the official Fortinet support site to ensure authenticity.
For systems that cannot be patched immediately, the following mitigation steps are strongly recommended to consider:
- Restrict Access – Limit access to the EMS web interface to trusted IP addresses only.
- Network Segmentation – Isolate EMS servers from other critical systems within the network.
- Monitor Traffic – Deploy intrusion detection and prevention systems to monitor for suspicious activity targeting EMS servers.
Additionally, best practices include the establishment of a patch management policy to ensure timely updates of all software (regular updates). AnIncident Response Plan is also crucial – organizations are advised to develop and test a robust incident response plan to quickly detect and mitigate threats. Finally, always apply Awareness Training: Educate employees about phishing and other tactics attackers might use to gain initial access.
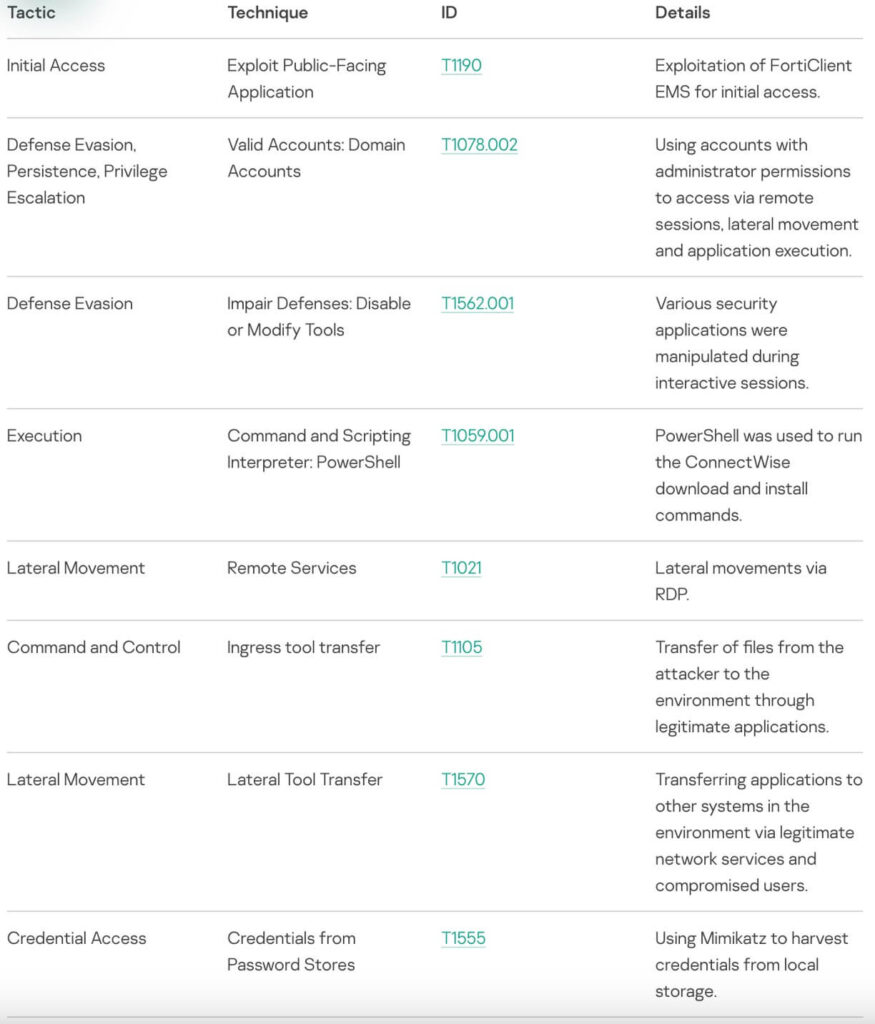
Tactics, techniques and procedures
Below are Kaspersky’s GERT team identified set of TTPs from their analysis and detections:
Conclusion
The FortiClient EMS Vulnerability is a stark reminder of the critical importance of maintaining up-to-date software and implementing robust security practices. With active exploitation of CVE-2023-48788 confirmed in the wild, organizations using FortiClient EMS must act immediately to protect their systems and data. By applying patches, implementing mitigations, and adhering to cybersecurity best practices, enterprises can significantly reduce the risk posed by this vulnerability.




