-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
CVE-2024-6387, or regreSSHion, allows remote unauthenticated attackers to execute code on OpenSSH servers.

CVE-2024-6387, dubbed regreSSHion, has been identified in the OpenSSH server. This vulnerability enables remote unauthenticated attackers to execute arbitrary code on the target server, presenting a severe risk to systems that utilize OpenSSH for secure communications.
As with last July’s CVE-2023-38408 affecting OpenSSH, this vulnerability is already making waves in the cyber security community.
CVE-2024-6387 is the first of two vulnerabilities discovered in OpenSSH in July 2024, alongside CVE-2024-6409.
Here’s everything you need to know.
|
Affected products: |
OpenSSH:
|
|
Product category: |
Server & network |
|
Severity: |
Critical |
|
Type: |
Remote code execution |
|
Impact: |
Confidentiality, integrity, availability |
|
PoC: |
|
|
Exploit in the wild |
No current evidence |
|
CISA Catalog |
No |
|
Remediation action |
Update to the latest OpenSSH version, restrict SSH access to trusted networks, use key-based authentication, and monitor logs for unusual activity. As a temporary fix, set LoginGraceTime to 0 if updating is not feasible. |
|
MITRE advisory |
CVE-2024-6387, referred to as regreSSHion, is a critical remote unauthenticated code execution vulnerability in the OpenSSH server on glibc-based Linux systems.
Discovered by the security researchers at Qualys, this flaw results from improper input validation in OpenSSH’s handling of certain SSH connections.
Specifically, the vulnerability is due to a buffer overflow, which occurs when an attacker sends a specially crafted request to the OpenSSH server, causing the buffer to overflow and allowing arbitrary code execution.
This vulnerability is rooted in the way OpenSSH processes user-controlled data during the SSH handshake. During this process, the OpenSSH server fails to properly validate the length of certain inputs, leading to a buffer overflow condition.
By sending a maliciously crafted request, an attacker can overflow the buffer, overwriting adjacent memory, including critical function pointers or return addresses.
This allows the attacker to gain control of the execution flow and run arbitrary code with the same privileges as the OpenSSH process, which often operates with elevated privileges.
To determine if your systems are affected by CVE-2024-6387, you need to evaluate your use of OpenSSH. This vulnerability impacts OpenSSH server versions prior to the latest patch.
If your systems use OpenSSH for remote management and are exposed to the internet, they are at significant risk.
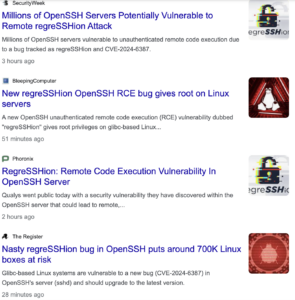
Affected OpenSSH versions are:
OpenBSD systems are unaffected by this bug, as OpenBSD developed a secure mechanism in 2001 that prevents this vulnerability.
Systems vulnerable to CVE-2024-6387 include those running affected versions of OpenSSH, particularly those with publicly accessible SSH servers.
If your OpenSSH deployment is exposed to untrusted networks or the internet, it is crucial to assess the version in use and take immediate action to mitigate the risk.
As of the latest reports, there have been no confirmed instances of active exploitation of CVE-2024-6387 in the wild.
However, the nature of this vulnerability and the widespread use of OpenSSH mean that the risk of exploitation remains high. Cyber security experts urge immediate action to mitigate this risk due to the potential for severe consequences if the vulnerability is exploited.
In its advisory, The Qualys research team emphasized that the vulnerability could be exploited without any prior authentication, making it a severe threat to systems with public-facing SSH servers.
The potential impact includes unauthorized remote code execution, which can lead to complete system compromise, data breaches, and other malicious activities.
Although there are no confirmed exploitation cases, the cyber security community is on high alert.
The ease with which this vulnerability can be exploited, and the critical role of OpenSSH in secure communications, necessitates proactive measures to protect affected systems. Researchers and security professionals continue to monitor for any signs of active exploitation.
As with any major vulnerability, CVE-2024-6387 has prompted particular attention and interest:
Customers are advised to upgrade to OpenSSH 9.8 or later to remediate this vulnerability. This patch addresses the input validation flaw, ensuring that specially crafted requests cannot exploit the vulnerability.
On June 6, 2024, this signal handler race condition was fixed by commit 81c1099 (“Add a facility to sshd(8) to penalize particular problematic client behaviors”), which moved the async-signal-unsafe code from sshd’s SIGALRM handler to sshd’s listener process, where it can be handled synchronously.
Since this fix is part of a large commit (81c1099), on top of an even larger defense-in-depth commit (03e3de4, “Start the process of splitting sshd into separate binaries”), it might prove difficult to backport. In that case, the signal handler race condition itself can be fixed by removing or commenting out the async-signal-unsafe code from the sshsigdie() function.
In addition, Qualys’s recommendations for enterprises to safeguard against the threat:
Finally, if sshd cannot be updated or recompiled, this signal handler race condition can be fixed by simply setting LoginGraceTime to 0 in the configuration file.
This makes sshd vulnerable to a denial of service (the exhaustion of all MaxStartups connections), but it makes it safe from the remote code execution presented in this advisory.
Each new vulnerability is a reminder of where we stand and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors: