With DevSecOps best practices, teams can remain on top of their security controls while taking full advantage of everything the cloud has to offer. A growing trend in the cloud ecosystem, DevSecOps brings the security mindset to modern cloud-native applications. While it may sound simple, securing a cloud environment with distributed applications is not so straightforward. Implementing DevSecOps can be tricky due to some fundamental properties of the cloud:
- Dynamic environment
- Configuration-as-a-code approach
- Vulnerabilities related to cloud operations
DevSecOps, however, is certainly an attainable goal. In this blog, we cover DevSecOps best practices for vulnerability management in the cloud.
What is DevSecOps?
In order to understand the DevSecOps concept, let’s take a look at its basic principles and how the security mindset is integrated into DevOps.
DevOps is illustrated as a chain of development and operations covering all responsibilities of both the development and operations teams:
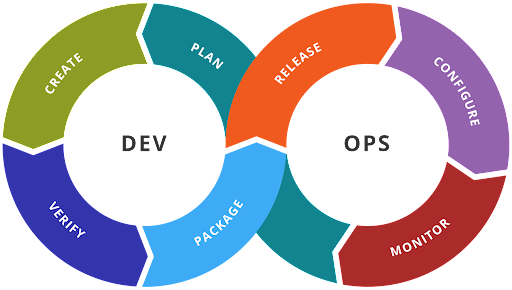
Figure 1: DevOps cycle (Source: Wikimedia)
Figure 1 above shows the pre-DevSecOps era, when security teams worked in silos, thus slowing down the software development process. Missing from this diagram is the security aspect; namely, how to develop and deploy applications securely.
As the cloud-native approach prompted faster development cycles, DevSecOps came to the scene and integrated a security mindset in every step of the DevOps chain. Merging security with DevOps affects every point of the development chain from the very start: requirement collection, design, development, testing, and deployment. In addition, teams’ increased communication and understanding create a shared responsibility, leading to shorter development cycles and faster releases.
Let’s explore how to implement DevSecOps in cloud environments.
DevSecOps best practices
When it comes to implementing DevSecOps, there is no silver bullet that can magically transform your organization from DevOps to DevSecOps. But there are a number of widely accepted methods for a successful transformation.
Vulnerability scanning and automation
Scanning your code for potential security flaws is an essential first step in creating secure applications. In the cloud, applications generally run as packaged in containers. Thus, the best approach is to check the code before building it into a container image in CI/CD systems.
Checks should be distributed throughout the development, testing, and deployment stages to detect vulnerabilities as early as possible. Ultimately, this will ensure that your code is safe to be packaged and distributed into servers running in your cloud providers.
Static application security testing (SAST) and software composition analysis (SCA) analyzers are essential tools for testing and analyzing your code and components. They are flexible and can be run both locally and in CI/CD systems for different stages of the DevOps chain.
The December 2021 Log4j vulnerability has only emphasized the importance of identifying and tracking vulnerabilities. Most companies are simply unaware of which Log4j version they are using, or in some cases whether they are even using it at all. Automation and continuous vulnerability scanning are key for giving you complete visibility of your stack, so you can be notified if any new vulnerabilities are found.
Runtime protection
While you can create container images with vulnerability-free applications, they are then distributed to data centers and run on host VMs. It is therefore recommended to secure applications against the threads that arise after running. For cloud-native applications, it is essential to analyze activities inside containers, such as network connections, processes, syscalls, and file activities.
In addition, as the containers will run on host VM instances, it is important to keep an eye on the underlying infrastructure. Your monitoring and alerting systems should therefore be capable of detecting unusual behavior such as environment variables or configuration changes.
Cloud provider analysis
Not only do cloud service providers provide compute, networking, and storage services; they also offer a robust set of security features. These features create a solid outer security layer around your applications as the cloud provider manages them. You can also enable or disable the security features by changing the configuration during deployment or later stages; thus, they are easy to automate in your CI/CD systems. AWS, GCP, and Azure also offer a number of native cloud security tools.
Security standards
When running data-sensitive and critical applications in the cloud, you must fulfill the accepted industry security compliance standards. If you have users in the EU region, for example, you will be required to implement General Data Protection Regulation (GDPR), considered the most challenging privacy and security law in the world.
Similarly, if you have credit card payment transactions in your application, you will need to meet the latest PCI DSS (Payment Card Industry Data Security Standard) requirements.
These standards encourage the most up-to-date best practices while ensuring user data is well protected. Incorporating security standard requirements in every step of the DevSecOps chain—from design to deployment—is therefore critical.
Policy analysis
Cloud policies are the set of restrictions and guidelines that ensure the integrity and privacy of your organizational information. The policies can be grouped into three categories:
- Finance management policies: To control operational budgets and monitor the trends in the cost in order to identify sudden increases, which may be related to the hijacking of resources.
- Performance policies: To set performance limits for virtual machines, storage, and networks in order to monitor utilization of services. Helpful for downgrading underutilized resources and upgrading those that are overutilized.
- Network policies: To set a secure perimeter for the applications running in the cloud provider so that only the allowed ports, IPs, and networks have access.
You will need to design the limitations of these policies, deploy them to the cloud provider, and then monitor for unauthorized changes. In addition, these policies consist of dynamic configurations such as server ports or usage levels. Thus, you need to update the policies with the deployment of the applications; and it is important to incorporate them in every stage of the DevSecOps chain.
DevSecOps culture
The last of the DevSecOps best practices is DevSecOps culture – this is the most critical for long-term success. In this context, “culture” refers to an organization’s shift in mindset, focusing on four key areas:
- People: DevSecOps is based on the idea of eliminating silos and creating a collaborative environment with shared responsibility. The people on your development, operations, and security teams are key to fostering this collaborative environment.
- Processes: Not only does DevSecOps change team structure and product features; it also changes how you do business—namely, processes. The DevSecOps culture calls for process flows that involve security teams and incorporate internal security processes into the processes of other teams within the company.
- Technology: DevSecOps is a modern approach, and it cannot be achieved using outdated technologies. Choose tools you can incorporate into the DevSecOps pipeline.
- Governance: After making the decision to run with DevSecOps and beginning to implement DevSecOps best practices, the next step is to measure the performance of your processes, teams, and tools to pinpoint bottlenecks and optimize them further.
The success of the DevSecOps culture depends on how well these four pillars work together. Before diving into the DevSecOps world, it is important to assess the current state of your organization. Once you’ve done that, you can designate action items in the four areas to ensure successful implementation of DevSecOps and find the right tools for implementing the DevSecOps culture in your organization so that nothing is overlooked.
Transforming from DevOps to DevSecOps at scale
Making the transition from DevOps to DevSecOps is far more complex than simply involving your security team in meetings or design decisions. It also requires deploying your applications to your cloud providers and scaling them with container orchestrators and service meshes with thousands of instances. This makes risk management challenging.
The Vulcan Cyber® risk management platform integrates with your existing toolset and empowers DevSecOps teams through asset management, risk-based prioritization, automation, orchestration, and performance tracking and reporting. With DevSecOps best practices and Vulcan Cyber, teams can gain full visibility of their cyber security life cycles in the cloud.
Help your DevSecOps teams keep up with emerging vulnerabilities across the cloud environment. Try Vulcan Free today.









