-
Platform
OVERVIEW
Capabilities
-
Solutions
USE CASES
-
Cyber Risk Hub
LIBRARY
-
Company
GET TO KNOW US
-
Pricing
Understanding vulnerability exploitation is crucial; EPSS provides essential insights for prioritizing remediation. Here's what we learned from our detailed study.

Understanding and predicting the likelihood of vulnerability exploitation is crucial. The Exploit Prediction Scoring System (EPSS) serves as a pivotal tool in this endeavor, offering data-driven insights that help organizations prioritize vulnerabilities for remediation.
In an inaugural study written by Cyentia and sponsored by Vulcan Cyber, we have an in-depth analysis of EPSS data, shedding light on key trends and patterns in vulnerability exploitation.
The following sections highlight the most significant findings and statistics from this groundbreaking research, providing valuable takeaways for cyber security professionals.
As of the end of May 2024, there have been 237,687 Common Vulnerabilities and Exposures (CVEs) published. This statistic highlights the substantial growth in the identification and disclosure of vulnerabilities, reflecting an annual increase rate of 16% over the past seven years.
The increasing volume presents a significant challenge for vulnerability management teams in prioritizing and addressing these threats efficiently.
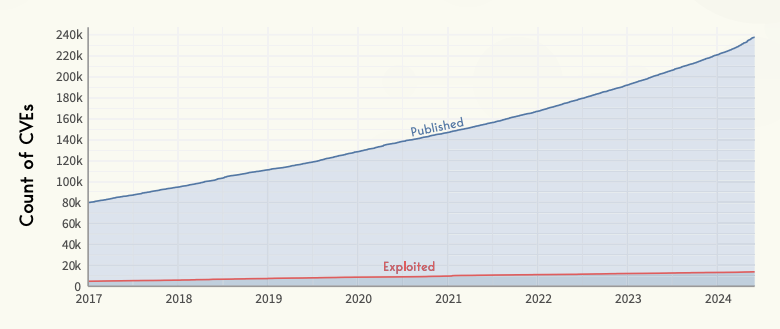
Out of the total published CVEs, 13,807 have been observed with exploitation activity. This figure represents approximately 6% of all published vulnerabilities.
The consistency in this proportion over recent years underscores the importance of monitoring and prioritizing these exploited vulnerabilities for remediation, as they pose a higher risk of being targeted by malicious actors.
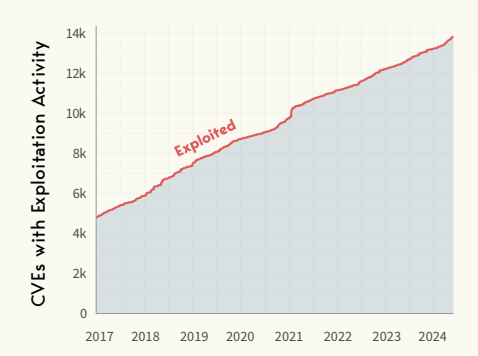
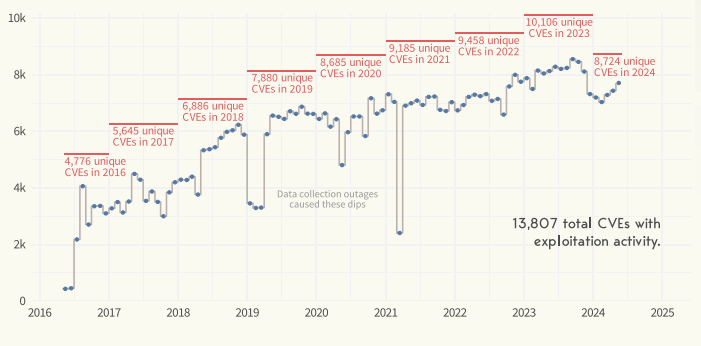
While nearly 14,000 CVEs were seen to have some exploitation activity, this does not mean that all of them are being actively exploited today.
For example, In 2023, around 10,000 CVEs were actively exploited, indicating that exploitation activity is dynamic and fluctuates over time. Not all exploited vulnerabilities are persistently targeted, which suggests that security teams need to continuously update their prioritization strategies based on the most current threat landscape and exploitation data.
The report indicates that 8% of known exploited CVEs were targeted before their official publication. These “reserved but public” CVEs, although not formally published, contain enough information for them to be identified and potentially exploited by malicious actors.
A strong majority, 70%, of known exploited vulnerabilities see exploitation activity within a year of their publication. The critical need for timely vulnerability management processes is clear, as most exploited vulnerabilities are targeted within this timeframe. Organizations must prioritize quick remediation to mitigate the risks associated with these vulnerabilities.
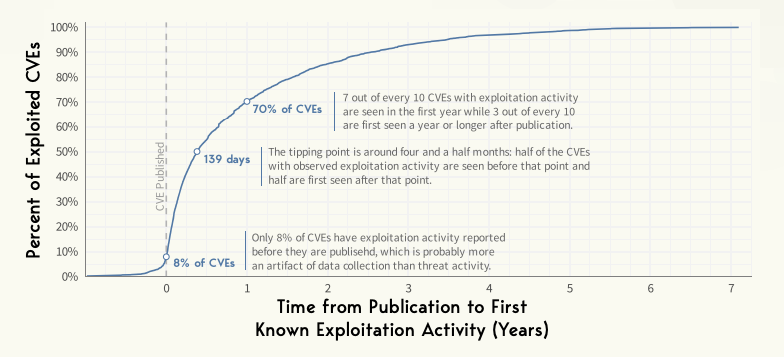
Five percent of the known exploited CVEs last saw exploitation activity more than five years ago, and have not been seen or heard from since.
This underlines the point that some exploitable or previously exploited vulnerabilities do not need immediate attention, and nor do they need to remain on your prioritization radar.
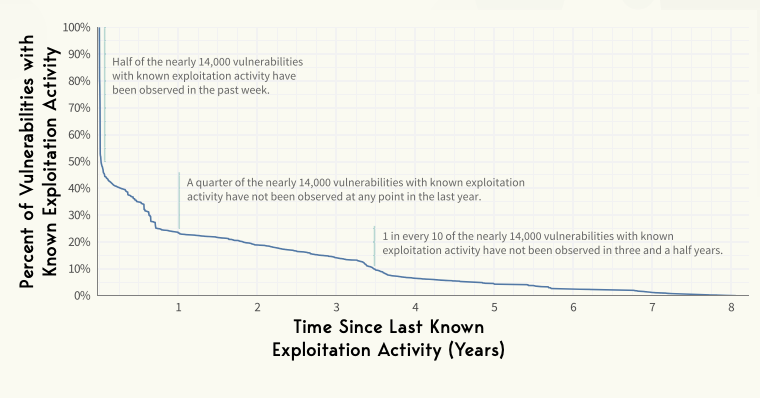
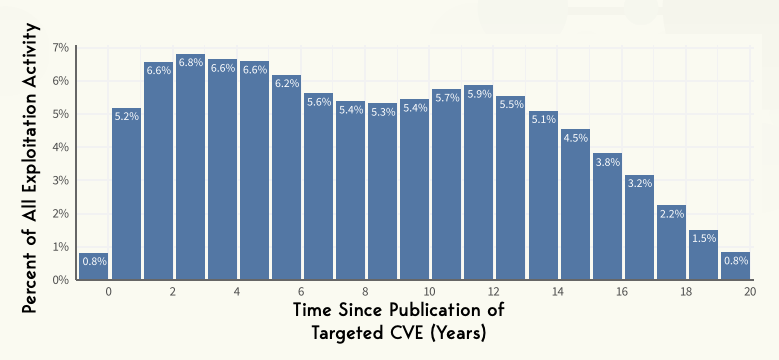
Conversely, the report also highlights a key trend about older vulnerabilities. Despite the common perception that attackers focus primarily on newer vulnerabilities, 39% of exploitation activity targets CVEs that are over ten years old.
The persistence in exploiting older vulnerabilities suggests that attackers exploit known weaknesses regardless of their age, highlighting the importance of addressing all potential vulnerabilities, not just the most recent ones.
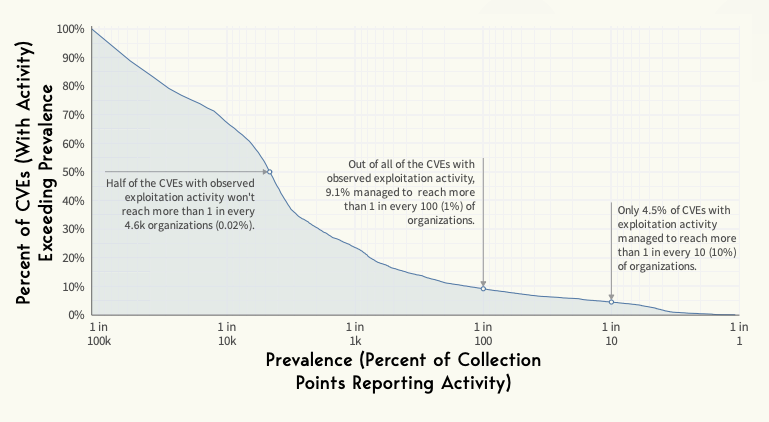
Only 5% of exploited CVEs are reported to affect more than 1 in 10 organizations. This rarity of widespread exploitation suggests that while certain vulnerabilities may be known and exploited, they do not necessarily pose a risk to all organizations.
This finding underscores the need for contextualized threat intelligence and tailored vulnerability management strategies.
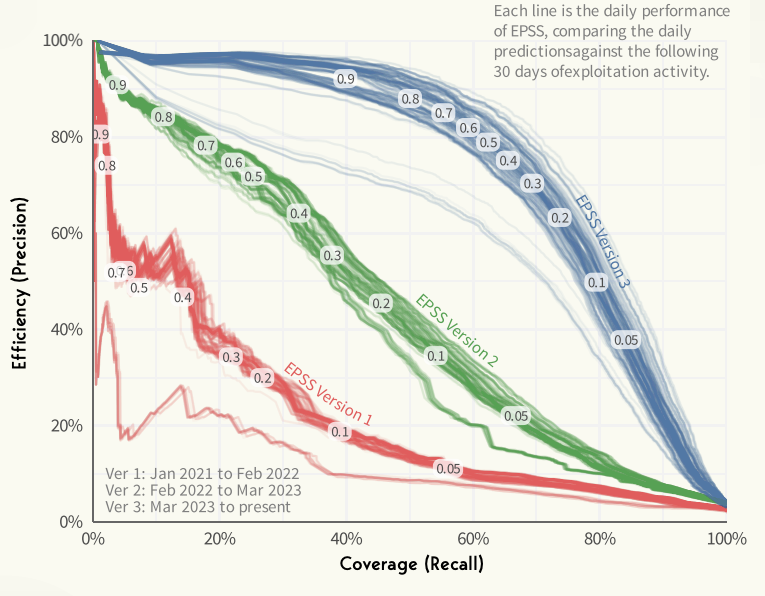
The Exploit Prediction Scoring System (EPSS) achieves an 80% efficiency rate for vulnerabilities with a score of 0.6 or higher, covering approximately 60% of known exploited CVEs.
This high efficiency demonstrates the effectiveness of EPSS in predicting exploitation and prioritizing vulnerabilities that are more likely to be targeted, providing a significant advantage over traditional scoring systems like CVSS.
However we prioritize threats, each new vulnerability is a reminder of where we stand and what we need to do better. Check out the following resources to help you maintain cyber hygiene and stay ahead of the threat actors: